Data Exfil & Sabotage
Detection of excessive file deletions or movements, unusual e-mail activities and consumer web application uploads is critical to preventing the exfiltration or sabotage of data. ITDR detects unauthorized or suspicious data access and activity and makes key correlations on file actions and transfers, focusing on ‘crown- jewel’ data in the cloud, apps, databases, file-shares and disks.
Outgoing Employee Threat
Individuals who plan to depart or learn they are to be off-boarded pose a substantial risk to corporate systems and data. ITDR focuses on detecting network and application access patterns that indicate job searches, outreach to competitors, and data exfil intent. Response capabilities include proactive alerts on these activities plus changes in behavior and productivity and forensic reports for use during post- termination reviews.
Account Compromise
With the right tools, it’s possible to pinpoint behaviors that indicate a potential takeover of credentials by third-party actors via negligent or malicious insiders, at speed and at scale. By detecting unusual login volumes, logins from high-risk locations, or geographically/ temporally impossible login sequences, ITDR excels at alerting investigative teams to instances of potential account compromise— before a data exfil attempt happens.
The Common Challenge
Insider threats pose a complex challenge for most organizations.
Information security and IT departments are constrained by conventional network detection systems that don’t account for the distinctly human motivations behind such threats. Meanwhile, HR, legal and physical security teams lack the means to derive useful intelligence from cyber indicators. The result is that risky insiders often go undetected until after an adverse event occurs.
How We Do It
24/7 Detection & Response

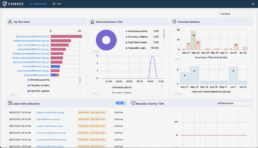
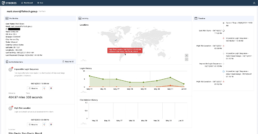
Through the application of our CYDERES Cloud Native Analytics Platform (CNAP) and the pioneering human-risk analytics of our industry-leading data models, we derive intelligence from existing network and endpoint telemetry to pinpoint malicious, negligent, or even unwitting individuals who show potential for causing harm to an organization’s finances, intellectual property, IT systems and reputation. This intelligence is prioritized, triaged, and delivered to our customers as rich alerts, optionally coupled with recommendations for mitigation actions and even policy changes.
At the heart of the ITDR service is a bayesian analytical model that ‘reasons’ like a team of insider threat experts and uses machine learning and advanced risk analytics to proactively identify risky individuals, as seen in the workflow diagram below. The system correlates relevant insider risk activities using data sources that report unusual login times, file accesses, and file downloads. These alerts may individually appear innocuous but, when combined and run through the model, create early indications of high-risk insider activity.
1
Data ingested from O365, Okta, G Suite, etc.
2
Platform analytics contextualize and prioritize indicators
3
CYDERES analyst validates and triages results
4
CYDERES delivers alerts and response recommendations
CYDERES ingests, validates and triages these indicators and delivers the results to organizations in the form of detailed incident alerts and the related evidence needed to launch an investigation, comply with legal and audit requirements associated with such activity and enhance future risk mitigation via policy and control changes.
Training and awareness programs can also be refined, ensuring an organization’s insider threat program has positive and proactive elements instead of being focused solely on punitive responses.
Overall Benefits of ITDR:
- Accounts for the human factor in user behavior analytics
- Uses context to filter out insignificant noise and false positives
- Prioritizes the highest-risk insiders
- Leverages existing cyber/IT telemetry with no new data sources needed
- Implemented rapidly to enable immediate insider risk mitigation
- Supports investigators with appropriate evidence and processes to address high-risk employees and suppliers