Real Solutions in 2020: A Cloud Governance Case Study
As things continue to change around us, our mission hasn’t.
Recognizing our 4th anniversary this week finds us more committed than ever to helping organizations minimize risk and thrive. Born in the cloud, and prepared to help clients deal with every aspect of security incidents of all kinds, our teams continue to lead organizations to a more secure future.
As our expanding team works around the clock, the threat landscape continues to grow and evolve. During the current COVID-19 crisis, phishing, malware, business email compromise, and other malicious attacks have spiked, and many organizations are scrambling to ensure their large remote workforces remain secure.
Recently, we looked at a client who had a lack of visibility and understanding of their attack vectors/vulnerabilities, with no partner to help manage, monitor, and remediate, along with a growing alert-factory from a sprawl of disconnected tools. Their adoption of CYDERES’ Enterprise Managed Detection & Response offering helped alleviate these issues and help them achieve faster, more secure growth.
Next, we looked at a recent client who needed help finding the cloud security gaps in a branch of their business and needed outside help to identify these gaps and recommend actionable solutions to help them move forward toward security maturity. Our Cloud Architecture Analysis illuminated these gaps and provided a roadmap for the best way for them to move forward.
With today’s post, we’re continuing our Real Solutions blog series with our third case study looking at a large retail customer who found that their cloud security immaturity left them extremely vulnerable.
A Few Pain Points…
A few of the challenges the client was experiencing before engaging with Fishtech were:
- Lack of awareness with requirements necessary to secure cloud workloads and how to remain compliant within a containerized/microservices environment.
- Lack of continuity with existing services and technology partners.
- Tool sprawl leading to operation and integration challenges.
- Locked into multiple long-term contracts with many underperforming solutions that didn’t satisfy requirements with their move to cloud-based infrastructure and requirements.
There were also cases where production S3 buckets were completely open, and developers were sending code to production environments that were not meeting compliance standards.
After reviewing the pain points of this particular customer, we got them working with our cloud governance team to start them on the path to compliance in their application environments.
How Did We Get It Done?
At the very beginning of this engagement, we led meetings, demos, and proof of concepts with various cloud compliance platforms. We scored these proofs of concept based off of the requirements of this client after several sessions gathering intel and data on the company’s major pain points and desired objectives.
Once we had worked through what the pain points were for this client, we worked to build out processes to get them compliant, up to speed, and more secure. By the end of the initial engagement, compliant code was put into place and is currently used within their application environments.
Through this process of improving this client’s Cloud Governance, we also started exploring other projects that would improve their overall security and digital infrastructure. For example, their security teams now have visibility and controls in place to automate the compliance process. A combination of interoperable tools, in-depth training, and thorough processes have been put in place to better their overall security posture.
In getting this client involved with our DevOps and Security Automation team, we were able to improve the efficiency of their processes to set the stage for growth while giving them the peace of mind that they will be secure along the way.
This has been a consistent theme to many of the case studies reported by account executives. We work to get solutions right the first time, so that the initial process runs so smoothly, that we often find our clients are willing to work with us in more areas to further improve their organizations.
In this particular instance, once we implemented our initial solution into production, we were able to help grow their environment from 400 projects/workloads to 1500. As we look to secure their containers, the environment will soon grow to over 4000.
Talk about Real Solutions with real results!
Next Steps with Fishtech Group
Efficiency in organizations operating in the cloud is hugely important in the modern business environment. Engaging Fishtech for our cloud governance services can be an important first step.
Learn About Fishtech’s FREE Cloud Maturity Workshop
If you have any further questions on cloud governance, fill out the form below and we will connect you with one of our experts.
Securing Third Party Remote Access
Securing access anywhere, anytime. This simple idea, which we have been passionate about since the founding of Fishtech Group, has taken on new urgency over the last couple of weeks.
With the recent worldwide shift of a large portion of the global workforce to social distancing by way of working from home, issues and challenges around remote access, business continuity, and even disaster recovery have become a priority.
Solutions around securing remote access like multi-factor authentication, VDI, and even VPN solutions only solve part of the problem. Thinking holistically on the remote access challenge is key. Organizations should start by asking themselves the following:
- Are users still using corporate-owned devices from their home or are they now using their own personal remote devices?
- Are we able to enforce patch management and push our DLP strategies to the remote devices?
- Are we still able to enforce authorization after authentication to the user?
- Have we validated the network segmentation strategy including cloud access from the remote access address pool?
- Are there concerns with latency issues for the remote workers and the data they are working on or accessing?
These are just a sample of the basic questions to ask as you deploy your remote strategies. Another challenge we are seeing our customers face is regarding 3rd party contractors who may not use corporate-owned devices. In our case, we were able to secure their access previously, because they were probably coming from corporate networks with corporate security standards and images being enforced.
As 3rd party contractors, or otherwise outsourced support, now move to work remote, how are we able to enforce who they are, what they can access, and make sure their endpoints are secure?
Fortunately, there is technology available to take advantage of the cloud for access. For example, pushing controls down to “per application” level security and integrating with VPN or SSO technologies to create an “Application Private Access” layer for security. This may become a newer and easier way of pushing out a layer of defense in-depth since physical access to systems is now limited.
The “APA” model allows for security controls to be built into this new type of remote access, with requirements such as DLP, endpoint enforcement, and even open API’s for log management and integration into Authentication and Authorization systems. Furthermore, in deploying a cloud-based solution, another added benefit is the ability to build this “APA” tunnel to the closest GEO location, solving general latency issues as they connect back to main corporate datacenters.
Many businesses are needing to adapt to a “new normal” with the increased amount of remote work needed from their employees as we all work to adapt to the curveball that has been sent our way. This also becomes a perfect time to refine how you do business and overcome challenges as they present themselves, like securing third party remote access.
If you are interested in furthering conversations about how you can make your business more secure in this turbulent time, fill out the from below, and we can talk to you about the above, or any other questions or concerns you may have regarding your current security posture, and the steps necessary to secure your organization so you can navigate these troubled waters with confidence. We have teams standing by to deliver virtual workshops, assessments, and demos.
Stay safe out there, and we’ll talk to you soon.
2020: Not Your Father's Ransomware

Business leaders and IT professionals have become increasingly familiar with ransomware over the last several years. Time after time, we’re exposed to high-profile stories where brands and organizations we know and love are crippled by cyber criminals encrypting sensitive data and asking for money in exchange for the “safe” return of data. We don’t have to search long to understand why we’re continually plagued by ransomware.
In 2019 alone, the top 5 largest payouts to cyber criminals made by organization’s struck by ransomware totaled over 1.6 million dollars!
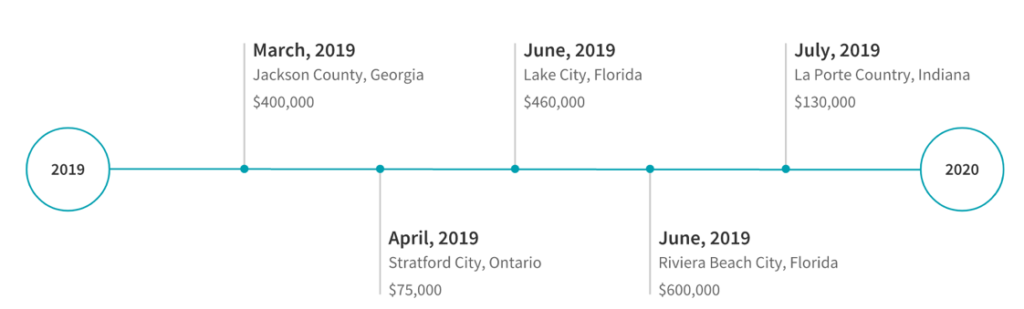
- Riviera Beach City, Florida – $600,000 [link]
- Lake City, Florida – $460,000 [link]
- Jackson County Georgia – $400,000 [link]
- La Porte County, Indiana – $130,000 [link]
- Stratford City, Ontario – $75,000 [link]
One of the biggest payouts ever made to malicious actors came from a South Korean hosting company called Nayana. During the 2017 Erebus malware outbreak, around 150 of Nayana’s Linux servers were infected causing more than 3,400 hundred hosted websites to go down. The company negotiated with the attackers, ultimately agreeing to pay 1 million dollars to release their data. [source]
There are several straightforward steps to take in helping to reduce the risk of becoming a victim; backing up and validating sensitive data, auditing and remediating accesses, and having an approved ransomware incident response plan are just a few. Undoubtedly, there are some organizations that have not begun implementing steps to reduce the impact of a ransomware event, while others recognize the risk to their business and have comprehensive systems in place to recover quickly from an attack.
|
“If you are looking for ransom I can tell you I don’t have money, but what I do have are a very particular set of skills. Skills I have acquired over a very long career. Skills that make me a nightmare for people like you. If you let my data go now that’ll be the end of it.”
|
With our best practices for recovering data loss in place, it would make sense to breathe easy and get a little extra sleep at night without worrying about losing that special project everyone has been working on, right? Not so fast…
Ever tenacious, money-hungry cybercriminals have begun a disturbing new trend aimed towards squeezing every cent out of their target, despite the organization having recovery capabilities.
Exfiltration is certainly nothing new, but some actors have started pulling this tactic out of their playbook and combining it with encrypting data to get extra leverage when demanding payment. It’s a simple scheme really, if you won’t pay to decrypt your data, then you’ll pay to prevent the data from being leaked publicly.
With the financial impact of losing data averted, organizations face additional challenges around data exfil like brand reputation, and regulatory compliance. After all, it’s one thing to lose access to your data and another to let the world know about that pending merger, research delay, ongoing litigation, or embarrassing personal matter. Some organizations may also have to contend with the possibility of regulatory fines related to the release of personal information, or financial filings. Incidents like this already have a media presence.
At the end of 2019, reports surfaced that Travelex was hit by the Sodinokibi ransomware after failing to patch their Pulse Secure VPN servers. Attackers stood to make a tremendous amount of money by reselling Travelex’s PII on the darkweb. As such, they demanded Travelex pay upwards of 4.6 million pounds for the recovery of the data and to prevent further exposure. The impact of the event also affected more than a dozen UK banks by taking down their foreign currency services. The Sodinokibi operators followed through on their threat to release information publicly after Artech, an IT staffing company, failed to pay the actor’s ransom demands on time.
The Sodinokibi actors followed in the foot steps of the Maze group who earlier released stolen data after compromising the network of security staffing firm Allied Universal. Operators demanded the company pay 300 bitcoins, or around 2.3 million US dollars, at the time of the attack to release the files. Not only did the malicious actors threaten, and subsequently follow through with, exposing company data publicly, the actors engaged directly with bleepingcomputer.com to break the story. Maze operators leaked a subset of Allied’s data, including termination agreements, contracts, medical records, and other sensitive data after the timeline to pay had expired and subsequently increased the ransom demand to 3.8 million to prevent further leaks. [source]
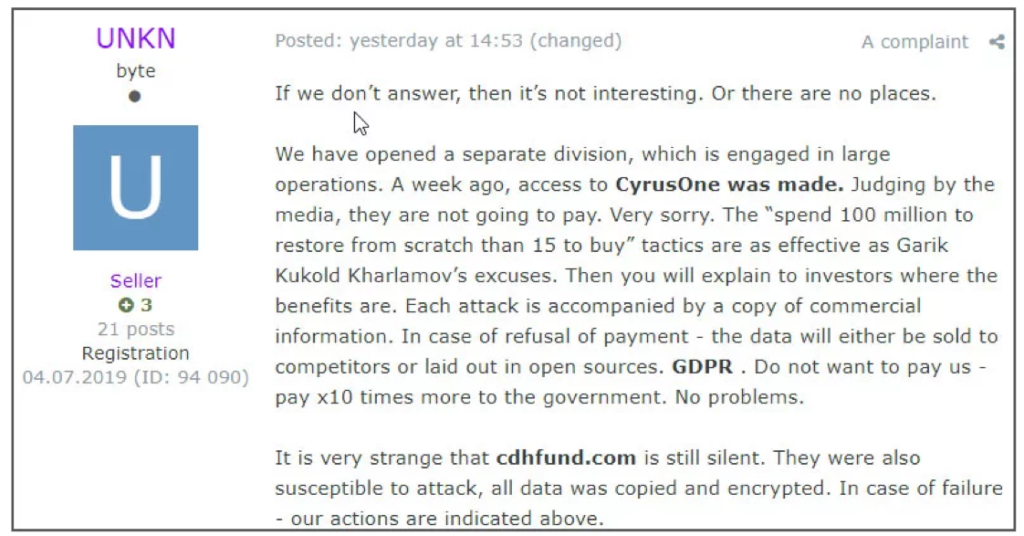 [Russian forum post]
[Russian forum post]
In a very recent incident, cyber criminals operating DoppelPaymer ransomware began to make headlines after infecting Visser Precision manufacturing. This incident is particularly interesting as some of the material published by the malicious actors exposed non-disclosure agreements between Visser and other companies such as Tesla and SpaceX. Previews of Visser’s data, released on a shaming site created by the DoppelPaymer crew, show folders and files implicating business dealings with other companies like Boeing and Lockheed Martin. [source]
As we move away from “spray and pray” attacks, it’s a fair question to ask how these malicious actors target an organization. Cursory searches online can often reveal the types of data an organization may be handling. Payment information, personally identifiable information, as well as electronic personal health information are all data types that could prove useful to an attacker when trying to extort the target organization. Additional information about cyber operations within an organization could be gathered by searching for infosec personnel on LinkedIn, looking at job postings on popular sites focused on cyber hiring, or collecting social media information from executives or cyber employees. These services can reveal clues to the security posture of an organization and may help make it a more attractive target. Attackers may also use public financial filings in addition to calculated regulatory fines for leaked data types to influence their decision in who to target, how much to ask for in their ransom demands, and how to frame the language of the demand to elicit the best response.
Whether a threat actor’s motivation is driven by financial gain, ideological difference, or nation state, they will continue to evolve their attacks in response to security’s evolution. It seems likely that these combined exfil + ransomware tactics are effective enough that they will not only persist, but continue to evolve. That evolution requires cyber professionals and business leaders alike to embrace creative thinking in combating an ever-increasing threat to your business and partners.
CYDERES is primed to help with threats like ransomware, and can help organizations in situations like those detailed above. If you are interested in finding out more about how CYDERES can help your organization combat ransomware and beyond, fill out the form below.
The Case for the Cloud
The current COVID-19 (Coronavirus) has caused disruption across many industries, and we are watching both the economic effects, and broader business and societal effects as the crisis continues to unfold. As always, please visit the CDC website to learn more from experts much more qualified than us to talk about the specifics of this outbreak from a personal health standpoint.
Beyond the crucial health implications, many businesses are struggling to grasp how exactly to manage a large mobile workforce from a cybersecurity perspective. Can existing infrastructure handle that load? Are proper identity and access management controls in place? This is the time when many cyber strategies (or lack thereof) and spending come into question.
The fact is, this crisis is creating a unique disturbance for many businesses we serve and has been a stronger case than ever for something we feel very passionately about: Digital Transformation.
What is Digital Transformation?
Digital Transformation is the fundamental shift in the way an organization operates. It is an integration of digital technology into every facet of a business, which creates a foundational change in its day-to-day functioning. This includes the digitization of your informational assets, implementing the use of technology for communication and customer interaction, and of course, securing this new digital perimeter.
So, what does this have to do with the Coronavirus?
It is imperative in uncertain times like these to put the safety of citizens and most certainly employees above all else. In this particular case, we’re seeing self-quarantines, and extended periods of sickness, but there can be any number of events that could cause your everyday work and routine to get interrupted. The future is uncertain. These events can be a huge disruption for many businesses, and can lead to lost productivity, and a huge slowdown in overall activity for your organization.
This is an opportunity to highlight how important it is to adapt when unexpected factors change the way you normally do business. The biggest shift in the overall business landscape in recent years has been the adoption of the cloud, or various cloud architectures including public, private, and hybrid models.
What Does The Cloud Look Like For Your Business?
There are many ways that digital transformation and cloud adoption can help your organization navigate times of uncertainty, and even operate more efficiently when times are good. Let’s look at a couple examples:
Video Conferencing
We have seen cases of self-quarantine in the current timeline of the Coronavirus, and employees get sick with or without newsworthy outbreaks. Cloud video conferencing allows employees to continue to connect with one another when they are unable to make it in the office in-person and create safer environments for everyone when there is significant disruption to daily life.
This becomes even more important when you are still needing to interface with clients and may be affected by travel restrictions, as we’re seeing right now. Video conferencing is an integral part of the cloud ecosystem of the modern enterprise.
Cloud Storage
There is more to business than just meetings (believe it or not!) Operating in the cloud allows organizations to store their data and allows employees to have access any applicable assets for their jobs, even while they are remote. This can be a big productivity booster, as individuals are not tied to their offices, and can work from anywhere when disruption comes calling.
If multiple employees are working on the same project, there is also more opportunities for simultaneous collaboration through cloud storage. If multiple employees are out of the office, they can continue to make progress, even if they aren’t in the same location geographically.
Scalability
The cloud allows for unprecedented opportunity to grow as you do. You won’t have to worry about a strain on your resources if you have a surprise change in your organization. This is very different from the on-prem options from the days old. The modern business needs to be agile, especially when faced with uncertainty.
Security
With the right partners, digital transformation can be a way to increase your overall security posture while you increase your flexibility. Especially when outside forces look to take advantage of vulnerable parties in newsworthy times, it can be imperative to have your position in place to continue to move forward with confidence in your organization when other factors may be out of your control.
Let Us Make the Case to You
Like you, we are continually monitoring the ongoing crisis, and we again recommend visiting the CDC website for all health-related updates as this situation continues. In the meantime, if you have questions about what the current climate means for your business, or you have questions about how to better utilize the cloud during this unpredictable time, we can help!
Our teams are standing by, ready to assist you with virtual workshops, demos, and assessments to ensure you continue to operate efficiently in this climate. Fishtech Group teams throughout the country are flexible, informed, layered, and able to collaborate to assist you from any location. We are accustomed to virtual work situations, and are well equipped to help you with any challenges you may face with your own teams.
It’s important that we continue running our organizations to add stability to our employees, communities, and countries. We’re ready to help in any way we can. Fill out the form below to get connected with one of our experts, or ask a question that you would like to see us address in the coming weeks. Stay safe, wash your hands, and we will continue to promote messaging to help you through digital transformation during this season and beyond.
To your secure future!
Supercharge Your Pen-Testing with Red Team as a Service
Whether you are just getting started building out your cybersecurity practice, or simply refining your maturity to secure your future, the flexibility of CYDERES 24-7 Security-as-a-Service has an offering for everyone, and is adaptable to businesses across the security maturity spectrum. These services range from the very niche all the way up to fully managed 24/7 protection. Let’s take another quick look at their current offerings:
- EMDR: Enterprise Managed Detection & Response
- GSOC: Global Security Operations Center
- CNAP: Cloud Native Analytics Platform
- ADD-ONS:
- CLOUD: Cloud Governance as a Service
- SIRT: Security Incident Response Team
- THREAT: Red Team as a Service
Today we want to go a bit deeper on one of these offerings that is delivering a ton of value to organizations looking for something more than their average penetration test: Red Team as a Service.
Red Team as a Service: The Next Level
Red Team Services through CYDERES provide objective assurance that your environment is secure – we are not looking to check a box and deliver a canned report like most pen-tests do.
Our penetration testing is designed to identify and validate vulnerabilities, exploit discovered gaps in the cyber and information security posture to establish a beachhead, and emulate real-world attacks against your infrastructure.
Our Red Team Professionals devote the time and attention required to achieve defined goals and “capture the flag.” Uniquely, we are 100% U.S. Citizens conducting our operations from U.S. soil with decades of industry experience in red team activities.
Final deliverables include an executive summary, an attack summary that reads like a storybook – telling you what we did, where we went, and how we got there. Recommendations regarding remediation for any discovered or created gaps in the organizations information security posture are also provided.
Domain Admin isn’t the end: CYDERES will work with your team to define objectives that show if an adversary can reach the most sensitive sections of your network.
CYDERES will even provide customization of proof of concept code for exploitation of discovered vulnerabilities in your environment.
Think your security controls are up to the task of keeping us out? CYDERES Red Team professionals regularly deploy custom malware specifically tailored to your environment to stress test your security tools and skip right past most AV/EDR solutions.
In an effort to align the assessment with real-world attacks CYDERES Red Team Professionals will leverage known password leaks, perform brute force attacks, dictionary attacks, hybrid password cracking and phish users with MFA support.
Our Red Team professionals take real-world tactics a step further by exploiting discovered gaps in WiFi deployments, testing Enterprise security for exploitable vulnerabilities and deploying leave-behinds on insecure network drops.
Lastly, our Red Team as a Service comes with “packs” of penetration tests bundled in a timeframe that makes sense to your organization’s size and ability to remediate, whether that’s monthly, quarterly, or bi-annually.
Conducting more frequent vulnerability tests arms your organization to protect against malicious attackers, but too frequently can also bloat your spend before remediation efforts are even accomplished from the previous round.
With Red Team as a Service, you are getting industry-leading professionals working with you to understand your architecture, your goals, and your adversaries to develop a real-world plan of attack that works with you as you scale your organization.
Penetration testing is critical for all organizations – but too often companies waste money with “run-of-the-mill” testing that yields unhelpful reports from distant third-parties.
Red Team as a Service works alongside you to meet your objectives and grow securely.
Next Steps as Your Organization Grows
Red Team as a Service is a great way to get started with CYDERES services to find your vulnerabilities and discover next steps to improve the security posture of your organization. Once you are integrated into the CYDERES ecosystem, we will help you leverage additional services that make sense as you continue to scale your organization, all the way up to 24-7 Enterprise Managed Detection & Response.
If you are interested in learning more about Red Team as a Service, or any of the other services that CYDERES offers, fill out the form below, and we will connect you with one of our experts so that you can focus on your business while we handle your threats.
Real Solutions in 2020: A Cloud Architecture Analysis Case Study
Why has our first focus in 2020 been on real solutions? Because that is our constant focus. 2019 was a huge year of growth for us at Fishtech Group, and that was due, in part, to one very big reason: We ignored the hype that has become so common in our industry.
New solutions pop up all the time (especially during RSA season), competing for your attention, with flashy buzzwords to overcompensate for the fact that these solutions may not be as game-changing as they are promoted to be.
This is a constant challenge for many modern enterprises and makes it very difficult to know which direction to go when their singular focus is securing their business.
The good news? That’s our goal for you too. We don’t advocate for the flashiest solutions. We advocate for the solutions that have a track record of success. With industry experience that goes back to the 90s, we know a successful solution when we see one!
We are now on our third blog post in our series advocating for our focus on Real Solutions in 2020. Last week, we took a deeper dive on how CYDERES helped one of our clients address a growing alert-factory from a sprawl of disconnected tools, and gave them peace of mind while they navigated the turbulent waters of acquisitions and mergers.
This week, we’re looking at a recent client who needed help finding the cloud security gaps in a branch of their business and needed outside help to identify these gaps and recommend actionable solutions to help them move forward toward security maturity. Let’s look a bit deeper on some of the pain points they came to us with.
A Few Pain Points…
A few of the challenges this customer was looking to address included:
- Needing to protect publicly accessible API services/SIEM.
- Looking to add security/IT assistance for a new multinational branch that is in a surrounding area lacking talent.
- Looking for a security architect to join their staff for projects requiring more than one full year.
- Needing an overall assessment for further recommended actions to improve overall security architecture.
After reviewing the pain points of this particular customer, we began a program of cloud architecture analysis to identify what they were lacking, and what further recommendations we had to address their needs.
How Did We Get It Done?
Taking a listen-first approach, we were ready to spend as much time as necessary to understand the client’s needs and then to give an accurate assessment to the client. We had extensive conversations that clearly explained the process of delivery and execution for this project. We had two consultants involved with two weeks onsite, and a few weeks offsite as well.
This client was looking to hire a security professional to take overall ownership of their security program but currently had no dedicated security resources. Knowing this, we performed our assessment with solutions in mind for a business that is still in transition.
Once completed, the assessment included recommendations for a number of technology products to fill the identified gaps. This client has limited internal resources to deploy and support additional security technology. Therefore, they needed to look to external services for the operational aspects of security like monitoring, auditing, and incident response, which we informed them of.
On top of all of this, we had to make sure each of the technology products were sufficiently validated to work alongside their existing stack, and optimized to function as required. Our constant aim is to deliver the right solution, the first time – shelfware is never a good solution.
Real Solution: Cloud Services Architecture Analysis
All of this led to presenting this client with a custom roadmap to give them actionable steps they would need to take to reach their overall security goals and KPI objectives.
We don’t just look at addressing present issues. We supply a strategic plan for future actions as well as the potential risks the organization will face as it scales.
We know that improving organizational security is a journey. Like with any journey, a map is incredibly helpful. Our experts have experience with organizations across the maturity spectrum, and therefore serve as incredible guides for navigating the digital topography that lays out in front of them.
Don’t know where to start? It can often feel overwhelming, but that’s what we’re here for.
If you are ready for your own cloud services architecture analysis to start your path to security maturity (and peace of mind!) in your organization, fill out the form below to get connected with one of our experts, and see for yourself how our Real Solutions in 2020 can help you grow your business in a real way.
Real Solutions in 2020: A CYDERES Case Study
Hype. A persuasive tool OVERUSED by industries of all persuasions. Just because something is talked about excessively doesn’t make it good, or right.
2020 has already been a particularly hyped up year with everything surrounding COVID-19. And that’s not even getting into the hype train in our own industry that chugs on in even the most uneventful of times.
Unfortunately, the field of cybersecurity solutions is RIFE with hype.
This makes life difficult for organizations looking to find the right solution set to elevate their cybersecurity maturity. Weathering the waves of hype that inevitably come year after year is a challenge, one that we seek to conquer to create trusted relationships with our customers.
Our constant focus: real solutions. What is working for our customers? Let’s double down on that. We’re continuing a blog series that aims to highlight real solutions that are working for our customers, and we’re continuing that with today’s focus on one solution that continues to deliver: CYDERES.
We recently worked with a small business client in the health care industry that saw real value with CYDERES and utilized their flagship offering: Enterprise Managed Detection & Response.
Let’s take a closer look at what this organization was facing, and what led to this decision.
A Couple Pain Points…
A couple of the challenges this customer was looking to address included:
- A lack of visibility and understanding of their attack vectors/vulnerabilities, with no partner to help manage, monitor, and remediate.
- A growing alert-factory from a sprawl of disconnected tools.
- Fast growth through acquisitions and mergers that exacerbated these issues and concerns.
Furthermore, prior to this client’s engagement with Fishtech, they were unaware of the security issues of the companies with whom they were merging, so their potential for breach was magnified.
Challenges like these are not uncommon in the modern business landscape and are challenges that CYDERES is tailored for. For these specific pain points, it was a no-brainer that our Enterprise Managed Detection & Response was the way to go.
Going with this option allowed this client to have full visibility of their vulnerabilities with experts from the CYDERES team ready and able to help give them any additional information that gave them more insights into their current security situations.
What Are the Other Solution Offerings of CYDERES?
CYDERES has a full set of solutions that are set-up for organizations all over the security maturity spectrum. Let’s take a quick look at the list of the various solutions that CYDERES provides:
- EMDR: Enterprise Managed Detection & Response
- GSOC: Global Security Operations Center
- CLOUD: Cloud Governance-as-a-Service
- SIRT: Security Incident Response Team
- THREAT: Red Team-as-a-Service
- CH/ES: Chronicle Essentials
Having these options available allows businesses to have flexibility once they enter into the CYDERES ecosystem to add or subtract services as necessary to meet the exact needs or their organizations.
For a small business to see the value in scaling their business with 24-7 managed detection and response put in during the early days of growth is a great strategy. Unfortunately, we encounter too many large organizations who failed to put solutions like this into place earlier and are suffering the consequences at a much larger scale.
The ripple effect of putting such a high value on securing intellectual property and customer data while a small business will help this company put more resources into growing their business, instead of sacrificing huge costs of recovering from a breach down the road.
In this particular case study, the client was already looking for help managing, monitoring, and remediating their threats. This was especially due to the rapid changes they were continuing to see with their acquisitions and mergers.
Having a third party to detect and remediate issues 24/7 gave them the peace of mind they were looking for as they focused their own resources on navigating their ever-changing organizational landscape. The ability to get real time insight into their security issues, some of which were grandfathered in to their organization once they had been acquired has been a huge benefit.
How Did We Get to the Right Solution the First Time?
We’re very aware that cybersecurity solutions are big decisions for organizations in every industry.
Any time potential clients are able, we invite them to come to our Cyber Defense Center in Kansas City to our state of the art SOC (or in these current times of coronavirus, have them take our virtual tour) and learn first-hand how potential security incidents are handled in real-time.
In this particular case, the client was brought in 6 months before the ink dried on the contract to see our facilities and talk with CYDERES professionals so that we could get a better idea of what their pain points were, and how we can help.
In learning about some of the specifics of this client’s environment, we made sure a roadmap was drawn out on what would happen when acquisitions took place, and how we would be able to engage with that change in a flexible way.
This is a huge reason CYDERES continues to win in the marketplace. We place a huge an emphasis on scalability with a roadmap to maturity as the business grows.
In fact, we have found so much success with our initial implementation of EMDR for this client, that they have engaged us to start scoping a DevOps project for them as well. Talk about a Real Solution that keeps customers coming back for more.
Real Solution: CYDERES
Even without having read through this blog post, you may have heard us talk about CYDERES a time or two. We continue to highlight CYDERES on our blog because customers are not only coming to us to improve upon their current cybersecurity solutions, but as we just mentioned, they are actually EXPANDING their usage of the CYDERES solutions.
This had led to an incredibly strong second full year of operations with 1,214% growth in year-over-year (YOY) in bookings and 960% YOY growth in gross profit. Those kinds of numbers don’t happen when a solution isn’t working.
So, let us make it work for YOU. This successful case study isn’t an isolated incident. We’re making CYDERES work for customers across the country, and we’re improving with each successful implementation.
If you’re interested in seeing real solutions with CYDERES, fill out the form below to talk with one of our professionals, so that you can start to truly focus on your business while we handle your threats.
2020: A Year of Hype. Our Year of Real Solutions.
Olympics. Elections. Super Bowl (Go Chiefs!). Viral outbreaks. Cyber-attacks. Make no mistake, the new decade is upon us with a year that will surely bring a ton of hype. The 24-hour media cycle pings around to each item with such great intensity that heads are turning back and forth as if we’re all looking at a global tennis match.
All of this can be incredibly distracting as our focus shifts to items that may not be applicable to our own personal goals and the goals of our organizations. What’s worse, it’s accompanied by that sinking feeling of missing something of ACTUAL importance to you and your organization.
Let’s commit together NOT to follow the hype. Moving your strategy this way and that according to the news of the day is not the way to run your business. In terms of cybersecurity strategy for organizations, we covered a similar idea in a recent blog post saying that the news cycle should not be your alert to put to proper practices into place to protect your business.
Through the turbulence of the modern business era, there are strategies that have held tried-and-true. This is why we are so adamant about our focus on being a data-driven cybersecurity solutions provider. We don’t advise on hype. We advise on real information.
This will be a huge focus for us to start this year. We want to double down on what’s actually working for our clients, and what proven methods got us there. In a year of hype, we want to flip the narrative and make 2020 a year of real solutions.
We have already been seeing huge wins operating in a data-driven way to provide real solutions for our customers that keep their businesses secure. CYDERES, our security-as-a-service division has seen explosive growth over the last year of operations as more organizations have trusted in our approach to managed security.
We have been expanding into new areas across the country to better service our growing customer base, including announcing a new Cyber Defense Center in Northwest Arkansas. We have continued to expand on trusted partnerships that have allowed us to better serve the organizations we are protecting every day.
Let us be clear… we’re just getting started. We’re not keeping our solutions a secret. We’ve seen what works for our customers, and we’re ready to implement these solutions for your organization so you don’t have to worry about what the news says you should worry about. You can trust our experts to get it right, because we have been getting it right with solutions backed by real data, regardless of what’s getting hyped.
Over the next month, we’ll be highlighting some of the real solutions we have implemented, talking to our experts on how they’re finding the right solution the first time for our customers, and lastly we’ll be taking deep dives into customer case studies let you see for yourself how our solutions are working first-hand. Stay tuned!
It’s time to get off the hype train. At Fishtech Group, 2020 is a year of real solutions.
The History of Haystax: Protecting the Super Bowl
When the Kansas City Chiefs and San Francisco 49ers face off against each other at Super Bowl LIV next Sunday, all eyes will NOT be on the field.
In secure command centers, field outposts, aircraft, vehicles and on foot, hundreds of security professionals will be diligently watching for any sign of threats on Game Day, augmented by thousands of cameras and sensors to detect everything from chemical and biological agents to conventional explosives and suspicious activity.
The security teams deployed inside Miami’s Hard Rock Stadium and in the surrounding area will consist of law enforcement and emergency personnel from the host city and surrounding municipalities, as well as regional and state government agency officials and personnel from federal government agencies such as the Department of Homeland Security and certain ‘three-letter’ agencies of the U.S. intelligence community. After all, the Super Bowl is routinely designated as a National Special Security Event (NSSE) due to its attractiveness as a terrorist target.
Nor is this a one-afternoon event. The Super Bowl is in reality a week-long affair, chock full of VIP parties, fan fests and of course the multi-day Super Bowl Experience, which kicked off on January 25th.
We’re proud that our colleagues at Haystax have been entrusted with security monitoring at eight of the last 11 Super Bowls. In each case, Haystax augmented its off-the-shelf analytics software platform by assembling a team of in-house specialists who uploaded data and photos on critical assets within the Super Bowl perimeter, assessed key buildings for likely threats and potential vulnerabilities, entered data on hundreds of scheduled events, established channels to monitor digital media feeds, deployed mobile field reporting apps and much more — all of the data precisely geo-located on digital maps for enhanced domain awareness.
Here are some examples of prior Haystax Super Bowl deployments:
Super Bowl LI
In 2017 in Houston, Haystax helped security teams and first responders maintain complete situational awareness and get ahead of their most serious threats. Using advanced analytics, the Haystax team looked for behavioral patterns that might indicate an attack. Data sources included chatter on a ‘dark web’ site, stolen vehicle data and suspicious activity reports. Each of these data points represented risk indicators, and bringing those pieces together into a single analytic environment enabled security decision-makers to get a better grip on whether the likelihood of a terrorist attack was going up or down.
Super Bowl 50
In the San Francisco Bay Area during the 2016 Super Bowl, the Haystax team pulled in data from a number of sources, including police and fire dispatches, weather reports, maps, news agency articles, social media activity and video camera feeds. Finely tuned algorithms then processed the huge amounts of collected sensor data, which was studied in real-time by analysts to deliver critical information in the form of actionable intelligence alerts to the event’s key security decision-makers.
Super Bowl XLVIII
The 2014 Super Bowl and more than 200 related events in the preceding week spanned police jurisdictions in two states (New Jersey and New York), several counties and multiple cities, and of course several federal agencies as well. The Haystax system made headlines for its crucial role in identifying a potential biological incident that turned out to be harmless white powder, averting major disruption to key events.
Super Bowl XLVII
During the infamous power blackout that occurred in the middle of the 2013 game, Haystax software in the New Orleans Emergency Operations Center discovered Twitter postings referring to ‘power outages’ at the venue, BEFORE the actual outage occurred. All related suspicious traffic and information was forwarded to FBI representative at the EOC, who quickly determined the threat was not credible or even linked to the actual blackout. As a result, the game could proceed without any major fan disruptions once power was restored.
According to an intelligence director at Super Bowl 50, “Having the ability to use Haystax applications — where you can literally take a quick note or a snapshot and say this is the situation here right now — clears up those radio channels and allows people to feel more freely about reporting things that they may otherwise not have reported until things escalate.”
Nor does Haystax limit itself to championship sporting events. In the past we additionally have managed security awareness for other NSSE events like the 2015 U.S. visit of Pope Francis, as well as national political conventions and high profile gatherings like the Oscars and the Indy 500.
# # #
Note: Want to read a play-by-play account of an earlier Haystax Super Bowl deployment? Download this free white paper on how we secured Super Bowl XLVI in Indianapolis.
CYDERES Tracks 1214% Growth and Hires Chris Currin as CBDO
FOR IMMEDIATE RELEASE
Contact: Jennie Hanna, jennie.hanna@fishtech.group
CYDERES Tracks 1214% Growth and Hires Chris Currin as CBDO
Fishtech Group’s Security-as-a-Service division is its fastest-growing area
Kansas City, MO (Jan. 21, 2020) — CYDERES, the Security-as-a-Service division of Fishtech Group, has capped an incredibly strong second full year of operations with 1,214% growth in year-over-year (YOY) in bookings and 960% YOY growth in gross profit.
CYDERES provides the people, process, and technology to help organizations manage cybersecurity risks, detect threats, and respond to security incidents in real time. CYDERES solutions include Managed Detection and Response (MDR), Security Operations Center as a Service, Cloud Security as a Service, Red Team as a Service, and Security Incident Response services.
On track to triple its year-over-year business growth in 2020, CYDERES has hired security industry veteran Chris Currin as Chief Business Development Officer. Currin is focused on helping CYDERES achieve its growth objectives and helping lead its go-to-market initiatives.
Key growth statistics for CYDERES point to a solution that is resonating with clients of all sizes, from small and midsized businesses to multiple Fortune 500 and FTSE 100 organizations:
- 212% achievement of CYDERES 2019 bookings plan
- 220% net revenue retention rate with zero “churn”
“We’re exceptionally proud of our results to date and even more excited about the growth to come,” said Eric Foster, President of CYDERES. “We know customers deserve a managed security service provider that delivers a legendary service at a fair price, and we’re honored that so many organizations trust Fishtech Group and CYDERES to be their provider. We look forward to helping transform the security industry with the help of our industry-leading security solution partners.”
Technology partners integrated into the CYDERES Cyber Defense Platform and delivered in its Security-as-a-Service model include: Google’s Chronicle global security telemetry platform; Corelight and Perch Security for network traffic analysis; deception solutions from Thinkst and Illusive Networks; phishing defense solutions from Cofense, Mimecast and Proofpoint; vulnerability management solutions from Qualys, Tenable and Kenna Security; and managed Endpoint Detection and Response (EDR) solutions for every major endpoint platform including Carbon Black, Crowdstrike, Cylance, LimaCharlie, Microsoft Defender ATP, SentinelOne, and Tanium. Integrated solutions for the CYDERES Cloud security service include Disrupt:Ops and Palo Alto Prisma Cloud.
In September, CYDERES was named as #25 in the Top 200 MSSPs list for 2019 by MSSP Alert, published by After Nines Inc. The list honors the top 200 managed security services providers (MSSPs) that specialize in comprehensive, outsourced cybersecurity services.
About Fishtech Group
Fishtech Group is the leading current-generation service provider enabling secure business transformation. Our experienced cybersecurity professionals plan, produce, and implement innovative solutions that ensure security and success. We focus on threats so you can focus on your business. Founded and led by CEO Gary Fish, Fishtech Group includes the Security-as-a-Service division CYDERES and the security analytics firm Haystax of McLean, VA. Fishtech venture partners include Perch Security of Tampa, FL, and Foresite of Overland Park, KS. Visit https://fishtech.group/ or contact us at info@fishtech.group.








