How Organizations are Optimizing their AWS Costs
Every day, our customers ask for help in seeking a better understanding of Amazon Web Services’ (AWS) complex and intricate pricing structure and how to leverage best practices around optimizing costs.
Cloud administrators, technical executives and FinOps managers make decisions every day to make their cloud usage as efficient as possible. But how do you know when a decision could compromise either performance or business continuity?
Some often-neglected keys to cost optimization include combining real-time visibility with the ability to instantly manage power schedules, control unused and idle services, and leaning into hundreds of reserve instance opportunities.
One partner we see providing tons of value (and cost savings) in this effort is CloudBolt Software. They recently (2020) acquired Kumolus, an AWS Advanced Partner, and one of the few companies with an AWS Competency certification in Cloud Management Tool (CMT), to accelerate their expansion and capabilities, not only around cost optimization, but also public cloud security.
To celebrate the addition of Kumolus, the CloudBolt team has capitalized on their newly-added expertise to create the Ultimate Guide to AWS Cloud Cost Optimization.
This guide helps advanced users gain an in-depth understanding of the key AWS concepts, service pricing, and best practices related cloud cost optimization. It covers areas of interest including Elastic Block Storage, EC2 Spot Instances, Bill Analysis, Cost Allocation Tags and so much more.
Each chapter contains charts and graphs to illustrate real-life examples of how the information can be used. And best of all, it’s written in a way that boils down difficult, complex concepts into an easy-to-consume format.
We are proud to count CloudBolt as a valued partner and applaud their initiative for freely sharing their experience to promote user awareness of these critical concepts for your business.
You can access the guide here and bookmark relevant chapters to your business, or download a full PDF copy here. It’s all free, you don’t even have to fill out a form. Check it out, and start using the information to optimize your AWS environment, today.
Talking with Fishtech Group Executive Vice President and CISO Kerry Kilker at CDC 2
We opened up Cyber Defense Center 2 in Rogers, Arkansas last summer to meet the growing needs and demands of our customers. Rubber met the road and CDC 2 is starting to really kick into high gear in 2021. We’re excited to expand our capabilities to better serve our clients, and to join such a thriving community in Northwest Arkansas. We recently sat down with our Executive Vice President and CISO Kerry Kilker in the new building to talk about why we chose NWA for CDC 2, what operations are taking place in the new building, our Security-as-a-Service offerings, and much more. Check out a few clips from our interview below.
Why Northwest Arkansas?
Why did we choose Northwest Arkansas for CDC 2? Kerry talks about the culture of NWA and how setting up shop there felt like a perfect fit.
Why Security-as-a-Service?
Why have we put such an emphasis on Security-as-a-Service at Fishtech Group? When Fishtech Group was founded, our goal was to provide cybersecurity solutions that adequately address our modern challenges. As Kerry explains, in today’s environment, Security-as-a-Service makes a lot of sense for many organizations.
How Fishtech Can Augment Your Existing SOC
Already have a Security Operations Center? Fishtech Group solutions are tailor-made to seamlessly fit into your operations. As Kerry explains, we work as an extension of your team, no matter how large or small.
Monitoring Your Data 24/7/365
We now have a 24/7/365 SOC in both Kansas City, MO and Rogers, AK with analysts that are working around the clock to make sure your business is protected so you can rest easy, no matter the hour of the day.
What Makes Fishtech Different From the Traditional VAR?
We strive to make sure you get the right solution for your needs, and we understand that your needs may be different than many other organizations in operation today. Fishtech can help you identify the exact solutions that work for your environment with the help of our experts.
Tips for Prioritizing Your InfoSec Strategy
Kerry details a few items to consider when prioritizing your InfoSec strategy. Overall, your priorities have to be based off of risk.
How Has the Pandemic Changed the Priorities of a CISO?
COVID-19 created significant shifts for organizations across the world, and CISOs’ priorities changed dramatically. Kerry details a few of the items that arose from the events of last year and how many organizations reacted.
The Most Rewarding Part of My Job
Jobs in cybersecurity can be challenging, but they can also be extremely rewarding. Kerry highlights some of his favorite parts of his job.
Want to learn more about Fishtech Group and our offerings? Fill out the form below to be connected with one of our experts.
Talking Security Incident Response with Bob Strohm, CYDERES Customer Success Manager
Having a team on standby to help with every aspect of a security event is more than a valuable proposition for many organizations, it’s an absolute must. The peace of mind that comes along with a highly skilled team that is ready to help when a cyber-attack strikes can help you focus more on growing your business rather than worrying about it.
We recently sat down with Bob Strohm from our CYDERES team to talk a little bit more about our Security Incident Response Team, or SIRT, which is included in our more comprehensive Security-as-a-Service offerings, but also offered as a standalone service.
Our Security Incident Response Team is made up of world-class professionals that have robust experience seamlessly working with organizations of varying sizes and helping them navigate the stressful circumstances that come with cyberattacks.
We asked Bob a couple of questions to highlight some core features of our SIRT offering and will continue to go behind the scenes to showcase all that this vital piece of our CYDERES organization does for our customers.
Stay tuned as we continue our interview series with leaders of the various offerings across our organization to highlight how we can help lead your organization to a more secure future. If you are interested in learning more about how our offerings can work with your organization, fill out the form at the bottom of the page to be connected with one of our experts.
Now, let’s dive into our interview with Bob.
Hi, Bob. Thanks for taking the time to talk with us today. Tell us about what you do at Fishtech Group.
I’m Bob Strohm and I am a Customer Success Manager with CYDERES, the Security as a Service group of Fishtech. I work with customers that come to us with a potential breach and assist in navigating their response.
Recently, we have been re-visiting our various offerings throughout the Fishtech Group organization, but particularly in CYDERES. Today we’re going to be talking about our CYDERES Security Incident Response Team, or SIRT. Could you give us a brief overview of our CYDERES Security Incident Response Team Offering?
With our Security Incident Response Team, we have a team of responders waiting to assist the customer with the incident on hand. At a predetermined discounted rate, our responders will act like an extension of your own team to provide services and intelligence at a moment’s notice.
With a wide variety of experience and background, our team can provide the expertise any organization needs during the stressful times.
What are some of the solutions provided by our Security Incident Response Team?
As already mentioned, our SIRT service will provide on demand response, but we also provide organizations so much more. With our “Use It, Don’t Lose it Policy”, any of the funds not utilized during the life of the retainer can be repurposed for any number of services.
Some of these services include Tabletop Exercises, Incident Response Plan Development and Review, Forensic Analysis or our Red Team as a Service for Penetration Test. We also have the flexibility to engage professional services within the larger Fishtech Group.
So, now that we have hit on some of our SIRT solutions, what are some examples of security incidents?
Of course, there’s the usual malware, ransomware, network intrusion, DDoS attack, hacked website, or other breach, but we also see company insiders who steal confidential data. The best preparation is a proactive approach that not only builds security maturity throughout an organization, but also has a response team prepared to handle every aspect of a security breach.
What would we recommend for organizations looking to take the first step in navigating an incident response plan?
There’s no need to reinvent the wheel, or try to do it all in-house, diverting resources from teams focused on building the business. At CYDERES, we bring a wealth of experience in building robust incident response programs that your organization can leverage to help you avoid common pitfalls and get peace of mind that you are as prepared as possible.
We can help you assess your risk matrix, and tailor a SIRT strategy for your organization and your use cases. At the end of the day, it’s about how quickly you can identify, contain, eradicate, and recover from a security incident.
CYDERES is proud to partner with organizations by providing the people, process, and technology to manage cybersecurity risks, detect threats, and respond to security incidents in real-time.
Learn more about how CYDERES can enable your business with a solid incident response program today.
The Things You Don’t Want to Forget from 2020
2020 was as unprecedented as everyone told you it was. A once in a generation pandemic upended our lives and our businesses and required us to find solutions to new obstacles as well as existing ones exacerbated by the crisis.
But the important question now is, what can we take away from the year we all want to forget? There were major lessons to be learned from the events of 2020, and by internalizing these lessons, we can properly prepare for the pitfalls of tomorrow. With focus and discipline, our difficult year can propel us to new heights of success this year and beyond.
So, in the spirit of learning, growing, preparing for the future, and ultimately setting ourselves up for success, we’re going to briefly talk about making sure that we’re not leaving behind important lessons from last year.
Are our remote workers truly secure? Can we handle remote work at a massive scale? Is our organization prepared for increased and widespread cyberattacks? Did we retain critical telemetry? What does it tell us about what our security priorities should be? All in all, do we have the most effective and cost-efficient solutions in place for whatever else the future has in store?
Let’s dive in and look at the things you don’t want to forget from 2020:
Lessons Learned
Remote Work Vulnerabilities
Having a largely work from home model thrust upon us was a challenge, but it also helped us learn some great lessons very quickly.
How do our remote workers access our applications and information? Are these avenues secure? Because there was an added emphasis on questions like these due to the sheer number of newly remote employees, many organizations gave dedicated attention to these issues, and worked on remediating any vulnerabilities that may have been discovered in the process.
These lessons and solutions should not be forgotten as we shift back toward hybrid models in 2021. Remote work is beginning to feel less like a trend and more like the new reality for organizations across the globe. Let’s use what we learned in 2020 to continue to improve our remote work processes.
Rapid Cloud Adoption
Playing into how remote workers conduct their operations, but also a pillar of the modern enterprise in general, the next lesson learned was surrounding cloud adoption and the security of cloud environments.
We have talked for years about digital transformation and cloud adoption is crucial for businesses in any industry if they are wanting to thrive in the 21st century. In order to accommodate a large remote workforce, rapid cloud adoption was crucial in making sure operations could continue in full force.
As many organizations were forced to adopt more cloud practices, they began to see the benefits that cloud operations can bring to their overall business practices. As we move deeper into 2021, we urge businesses to not ease up just because the overall necessity is beginning to wane.
Urgency toward growth and productive operations can be just as valuable as urgency for overall necessities. We know the most successful businesses in the years to come will be those that build about the foundations that were set in the cloud 2020.
Cloud Cost Efficiency
Many organizations consequently learned the costs associated with cloud adoption and found that they may not have been as efficient in their spend as they could have been. With a strategic approach to cloud adoption, businesses can find efficiencies in both operations and associated costs.
Now that there is room to analyze best solutions, it is imperative to take the data from cloud integration in 2020 to help you grow into your overall processes with the cloud in 2021 and beyond.
Many solutions popped up in 2020 that were tailor made to allow for better cost efficiencies in the cloud. Engaging with solutions like these are great launchpads to help you thrive in the years to come.
Data Access for Threat Hunting
With so much more data flowing from so many more devices, there is a lot to keep track of. With solutions like CYDERES using tools like Chronicle to allow to sub-second search latency for all inquiries dating back a full year, organizations were able to better address security risks that may have come from new remote work practices.
Don’t miss that point – 2020’s security data was like a preview of coming attractions to those who are wise enough to see it.
Organizations who can cost-effectively retain a full year of telemetry are seeing how existing problems were quickly and exponentially exposed by the onset of the crisis. Chronicling those red flags allows the proactive to get ahead of vulnerabilities that may have been slow burning but were dragged into the light ahead of schedule.
Being able to access such a large amount of data at such rapid speed, and then plan your security program’s upgrades accordingly will be a game changer in the years to come. We will continue to promote this heavily because we have seen the overwhelming benefits of threat hunting in this way.
Again, as things shift back to hybrid models, this is one thing from 2020 that should stick around.
Looking Forward
These are just a few items that we believe should carry over from 2020 and inform strategy and direction for enterprises in various industries. While we are all ready to move forward from the events of last year, we believe it is truly important to take the time to reflect on lessons learned, and this list may just be the tip of the iceberg.
Throughout a year of incredible hardship, we continued to be so moved by the resiliency of our customers, partners, employers, and community, and we know we are going to come out the other side of this collective experience stronger and ready for the future.
If you are ready to discuss how we can help turn the lessons learned in 2020 into concrete, actionable plans for 2021, fill out the form below to be connected with one of our experts.
IAM Interview with Chris Vermilya, Director of Identity and Access Management
Identity and Access Management services have quickly become a very valuable part of many companies’ security plans since the onset of the COVID-19 pandemic last year. The shift to remote work changed how many organizations looked at authentication of their users. Once these organizations started to implement more mature IAM processes, they began to see the many benefits an Identity and Access Management program could have for their overall security posture.
Now, companies are looking at what next steps they can take to further develop their Identity and Access Management programs moving forward as workforces continue to shift with each new passing development in 2021.
With all of this in mind, we recently sat down with Chris Vermilya, Director of Identity and Access Management at Fishtech Group, to discuss our IAM offerings and talk about where we’re headed next.
Hi, Chris. Thanks for taking the time to talk with us today. Tell us about what you do at Fishtech Group.
Thanks for having me. I appreciate it. My name is Chris Vermilya and I am the Director of our Identity and Access Management practice here at Fishtech.
As we have highlighted before, there are four pillars of Identity and Access Management. What are the four pillars and which pillar do you see most of your engagements landing right now?
Good question. So, the four pillars that we look at when we consider Identity and Access Management are Identity Governance and Access, or IGA, Access Management, Strong Authentication, or MFA (Multi-Factor Authentication), and then finally Privileged Access Management. Lately, we’re seeing the highest demand for Access Management, followed closely by Identity Governance.
Organizations are looking to secure their on-premises environments, cloud-based infrastructure, and SAS applications with a common platform, one that provides both robust security, and also a familiar user experience. We have a lot of demand for solutions like Okta, Ping, and Microsoft’s Azure-based solution, etc. to provide the capabilities that our customers require to meet their needs.
But as I said, coming in close second is demand for better Identity Management as a whole, you know, Identity Governance. Once customers establish their Access Management footprint, they really want to go further and more formally manage their identities that they need to trust. You can’t just open the gates as soon as the user successfully authenticates. We need to better manage the complete identity and what they should or should not have access to.
IGA solutions like Saviynt and SailPoint provide visibility, risk analysis, access certifications, and a lot more to really help us fully manage the identity and their access across the board.
How would a customer begin an engagement with the IAM team?
Sure, so in order to engage with our team, we really have a lot of different approaches that a customer could take. Fishtech sets itself apart in the IAM space by taking an advisory-first approach in really every engagement that we participate in. This looks different based on the needs of the customer, of course, but as a starting point we can provide small one-day workshops to assess the health of an IAM program across all four of the IAM pillars, again being Identity Governance, Access Management, Strong Authentication, and Privilege Access Management.
The outcome of those workshops is typically an action we’ll road map that has not only recommendations on where to take that next step, but what does the timeline look like across the next couple of years? We also provide full IAM assessments that can span several weeks and provide not only the in-depth observations and recommendations that you would expect from an assessment, but a full, strategic, road map and IAM program strategies that are going to be specific to each of the pillars that we mentioned.
It really helps provide customers with actionable milestones for their broader IAM program. We also offer implementation and delivery expertise where our engineers will come in and partner with our customers, not just to turn the wrenches and stand up a solution but provide best practices and other strategic input with that advisory hat on.
Lately, one of our more popular offerings has been a relatively small, but kind of an advisory- / architecture-type engagement. We’ll bring in an architect to work with our customers to look at, typically, one specific IAM pillar and look at the planning and then help design and scope what a potential implementation could look like to meet the needs of the organization. Understanding what should be included in that phase one, and really, what can be pushed to more phase two based on the organizational needs, and also what other considerations should be made to make that implementation successful.
Now those engagements typically result in a solution design document that we’ve worked through together with the customer and often leads to a full implementation if that’s the route that’s desired, or into a larger IAM assessment engagement depending on the needs of the customer.
How has the last year impacted organizations’ needs for Identity and Access Management?
So, the past year has been an interesting one, as you would expect, right? I mean, COVID really pushed IAM to the forefront a number of different ways, but specifically within the Access Management IAM pillar it really pushed that into the spotlight for a lot of organizations. We found our customers needing to rapidly stand-up solutions to securely facilitate access to both their on-prem resources, their cloud-based applications, any of their SaaS offerings they are taking advantage of, they really needed to get that up quickly to make an impact to securely engage with their users to be able to provide for their needs.
It’s actually still continuing, but as that the starts to settle, many of our customers are now looking to build on that modern foundation and expand into more Identity Governance-type solutions, as well as Privileged Access Management if they don’t have a footprint in the space already.
I’ll throw out Zero Trust here as well. It plays a lot into this transition, as many organizations have started down this path due to COVID, but our customers really just want to ensure that their assets are protected as the entire workforce is largely remote at this point, or at least a much broader percentage than they were in the past.
At a base level, that means we’re no longer trusting where a user is logging in from, or even the device they’re using. BYOD certainly isn’t new but having our users completely remote and on their own devices 24 hours a day has really changed things up. It’s really pushed Identity Management to that foundational level of changing how we view IT security as a whole. We really have to look at the identity to know what a user can and cannot do, and then implement their accounts and their access accordingly. Identity Governance really has to be in the picture because of that change.
Our customers are seeing the benefit of making that jump to managing the identity as a whole over just the accounts themselves. For better or worse, COVID was the spark that forced a lot of that movement over the past year.
Looking forward, what’s next for your team and the broader Fishtech Group IAM offerings?
We’re looking forward, you know, we’re always kind of keeping an eye on how we can better change our offerings to meet the needs of our customers. But Fishtech has and will continue to be a true partner with our customers. We believe strongly in our approach. It allows us to be flexible to meet the needs of our clients, even as those needs change, especially if they’ve changed pretty dramatically over the past year or so.
Identity and Access Management has established itself as the foundation of modern security, and we’re excited to continue to see organizations understand that shift and move forward securely on their own journeys.
We’re seeing more need for IAM-as-a-Service-type offerings. As demand rises for talent, and the more these solutions are being implemented, it’s hard to find people that can meet those needs.
IAM solutions need care and feeding and, realistically, IAM is not going to be a core competency for most organizations. They need to support what their business truly is doing, so we’re working to provide new services for our customers around our strategic technologies to help continue our partnership beyond just the traditional advisory and delivery that we’ve been doing, but more into the managed services space.
Our advisory-first approach will extend into those offerings as well and allow us to not only meet a need for our customers but bring the advisory mindset to what has traditionally been an operations-focused arena. So, we’re excited to see where that moves forward in the future and how we can tie that into other offerings from the Fishtech organization in terms of overall IT security management.
Interested to Learn More about IAM?
Why CYDERES is a Top MSSP (Again)
Since its inception as a modern answer to the issues that have plagued legacy SIEM and MSSPs, CYDERES has been continually recognized as one of the best Managed Security offerings on the market. CYDERES has now added another recognition to its growing list after being added as one of Cyber Defense Magazine’s 2021 Top 100 Managed Security Service Providers.
This adds to CYDERES’ impressive run on many top MSSP lists including:
- 2019 MSSP Alert Top 200 Managed Security Services Providers List
- 2020 MSSP Alert Top 250 Managed Security Services Providers List
What is it about CYDERES that makes it a step above other organizations in this space? Our mission with CYDERES was always to address shortcomings of other legacy MSSP and SIEM solutions. We’re continuing to build out our solutions to become the best MSSP on the market that simultaneously does away with the pitfalls of past MSSP offerings, while adding value with a wide array of offerings that will help protect your business from the threats of today.
As our founder Gary Fish has said “CYDERES was built to address systemic industry challenges, including a critical lack of skilled security resources, a general shortcoming of cohesion between various point products, and the continued escalation in pace and scope of security breaches.”
Let’s take a look at some of the developments that have built CYDERES into a widely-recognized top-performing MSSP.
A Look Back at How We Got Here
We opened our Cyber Defense Center in 2019 to house our world-class CYDERES team, attracting talent from across the country to be a part of a game-changing cybersecurity organization. Inside our Cyber Defense Center, you can find our state-of-the-art Security Operations Center.
Our foundation was then set with our partnership with Google Chronicle when we became one of Google Cloud Security’s initial partners worldwide trained and licensed to deliver managed detection and response services for its new Chronicle platform.
The Chronicle platform, coupled with our award-winning Managed Detection and Response offering, continues to provide our clients with unmatched capabilities for threat hunting and incident investigation.
Our offerings expanded with the development of the CYDERES Cloud Native Analytics Platform solution which provides our customers with comprehensive solutions for detection and response of information security threats, and the cost-effective storage and analytics of security data.
The proprietary CNAP platform combines comprehensive threat detection, investigation, and workflow along with reporting for compliance and operations. CNAP is powered by and built on Google Chronicle and is currently being sold through the Google Cloud Marketplace. With CNAP’s ability to combine the best of what legacy SIEM had to offer with the latest features of next gen solutions, “we have completely reimagined and created what a SIEM should have been all along” says Gary Fish.
Recent CYDERES Developments
CYDERES has continued to build off the momentum that has accumulated since the outset of the organization through strategic partnerships, and further development of features and additional services to provide a robust 24/7 Security-as-a-Service offering for any computing platform or environment.
CYDERES has partnered Fishtech Group’s Insider Threat focused company Haystax to offer Insider Threat Monitoring as a Service as a frictionless add-on to the CYDERES Managed Detection and Response solution. The offering growing the CYDERES broad data spectrum for cyber defense and response via the seamless integration of Haystax’s industry-leading Insider Threat Platform.
CYDERES continues to develop other service offering like Red Team as a Service and CYDERES Cloud Security to further add value to customers that are at any place in their journey toward security maturity.
With so many of these pieces coming together in a refined package, and many of our customers seeing success in their partnerships with CYDERES, it’s easy to see why CYDERES has continued to be named as a Top MSSP year after year. Not only that, but CYDERES is changing the conversation around Security as a Service offerings, and making people see the competitive advantages that Security as a Service providers like CYDERES can bring.
Are you ready to see for yourself why CYDERES consistently gets named as an MSSP leader in our industry? Fill out the form below to be connected with one of our CYDERES experts and let us help you on your journey toward a more secure future.
Threat Highlight: APT35 (CYDERES Technical Blog Post)

“Intelligence drives operations”
Gen A.M. Gray 29th Commandant of the United States Marine Corps
In the art of warfare, intelligence gathering on an adversary has been a long-standing practice that aids military commanders in making decisions on future operations. During the American Revolutionary War, the odds were stacked against the American army. General George Washington required a foolproof plan to even the playing field against the intimidating and larger British force. His answer to this was espionage. Washington employed ordinary people to build spy rings, turned British spies into double agents and established multiple networks of agents informing him of what the next plans were. Mail was intercepted, opened and copied without breaking the seals, making him the master of this war. With the intelligence gathered, Washington created a massive man-in-the-middle deception operation which caused confusion and disrupted British communications.
Likewise, cyber intelligence is used to gain knowledge on the adversary, disrupt its operation and prevent future attacks. How does an attacker or threat actor gather intelligence on their next target? Other than open-source intelligence, what tools, tactics or techniques do they use to gain a foothold inside their targets’ network?
Not so charming kitten
The espionage group APT35, is known for conducting long-term resource-intensive operations to collect strategic intelligence. APT35, also known as Phosphorus, Charming Kitten and Ajax Security, has been seen conducting operations dating back to 2014. This threat actor group has conducted intelligence campaigns against individuals in the United Kingdom, the Middle East and North America. Assessments have been made that APT35 works from Iran and is likely sponsored by a domestic government agency.
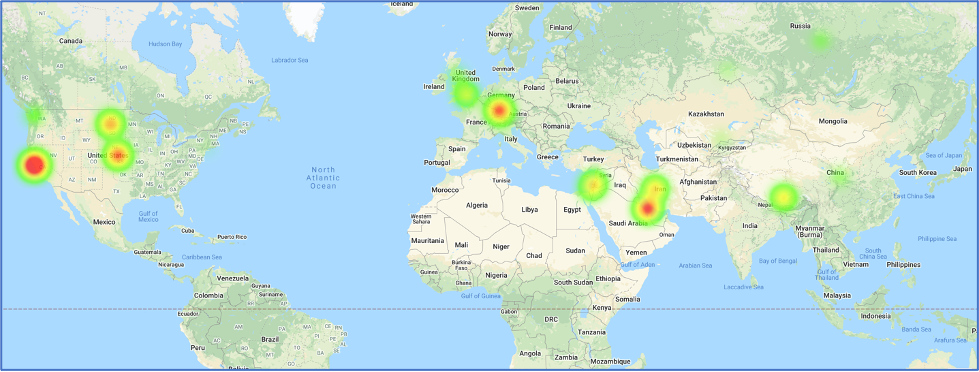
Map references related to APT35
One of the main tactics APT35 uses is Phishing, and social engineering is the usual method of executing it. In November 2019, APT35 used a fake interview scenario to target their victims. The threat actor group impersonated the New York Times journalist Farnaz Fassihi and used this identity as a Wall Street Journal reporter to send interview requests.
Trust and Reconnaissance
The first part of this phishing campaign is to gain the trust of the target. This was accomplished by sending emails from the email address farnaz.fassihi[at]gmail[.]com. The email states Farnaz Fasihi is a journalist at the Wall Street Journal Newspaper requesting an interview to share some of the victim’s important achievements” with their audience. They mention their Middle East team of the WSJ intends to introduce successful nonlocal individuals to motivate the youth in their country to discover their talents and be successful. A screenshot of the email retrieved from Certfa can be seen below.
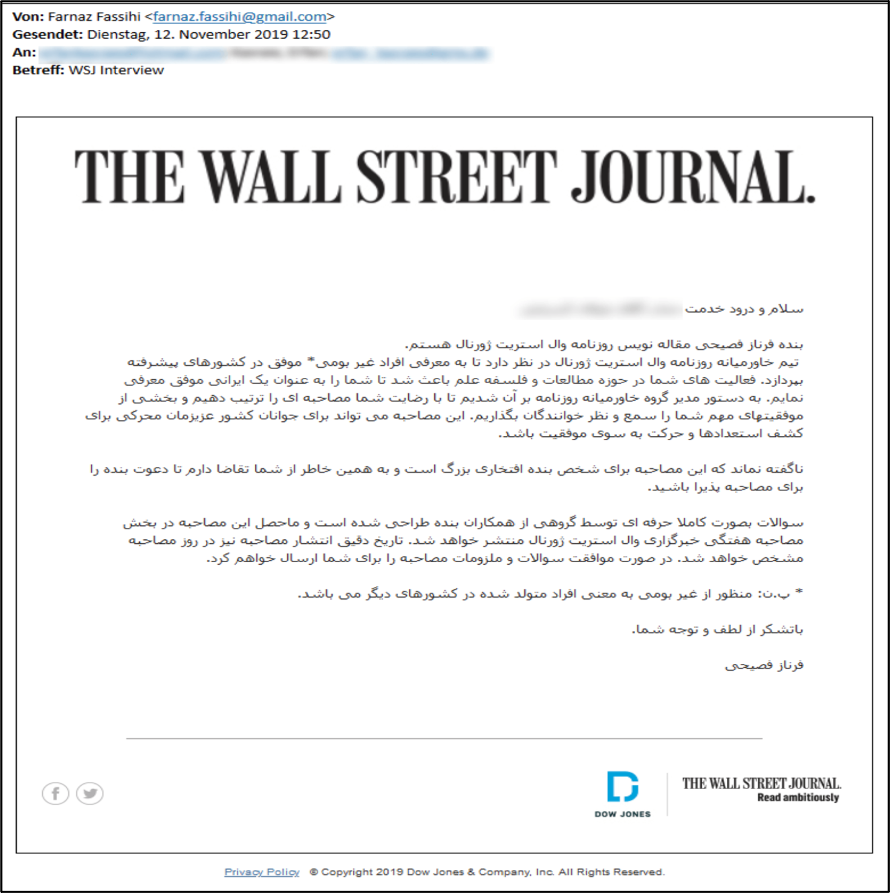 Email impersonating Wall Street journalist
Email impersonating Wall Street journalist
Other than crafting these emails to gain trust, they also serve as part of the intelligence gathering that APT35 is known for. The URLs found on these emails are all in the short URL format, which the threat actor group can use to direct the victims to legitimate addresses while gathering intelligence on their victims. The basic information that can be acquired by using a short URL service like bitly are the victim’s IP address, the type of operating system and the browser. The intelligence gathered enables the attacker to tailor future attacks based on victims’ devices.
Final Payload
Once trust is gained with the victim, the final link containing the supposed “interview questions” is sent. This link directs the victim to a phishing page hosted on Google Sites, making the victim trust the destination domain and evading spam detections. The final destination of the download link redirects the victim to a fake page in two-step-checkup[.]site domain where the credentials and the two-factor authentication (2FA) code are requested by phishing kits. One such phishing kit is Modlishka, a penetration testing tool that can bypass 2FA and automate phishing attacks. This tool, available on Github, employs reverse proxy in a way that facilitates phishing attacks.
A piece of malware with the file name pdfReader.exe was also used in this campaign. Analysis of the file shows it modifies the Registry and the Windows Firewall for it to run on the victim’s machine and also gathers intelligence from the victim’s device which gets sent to the attacker. This type of malware, known as a loader, is used to run new malware remotely on the victim’s machine.
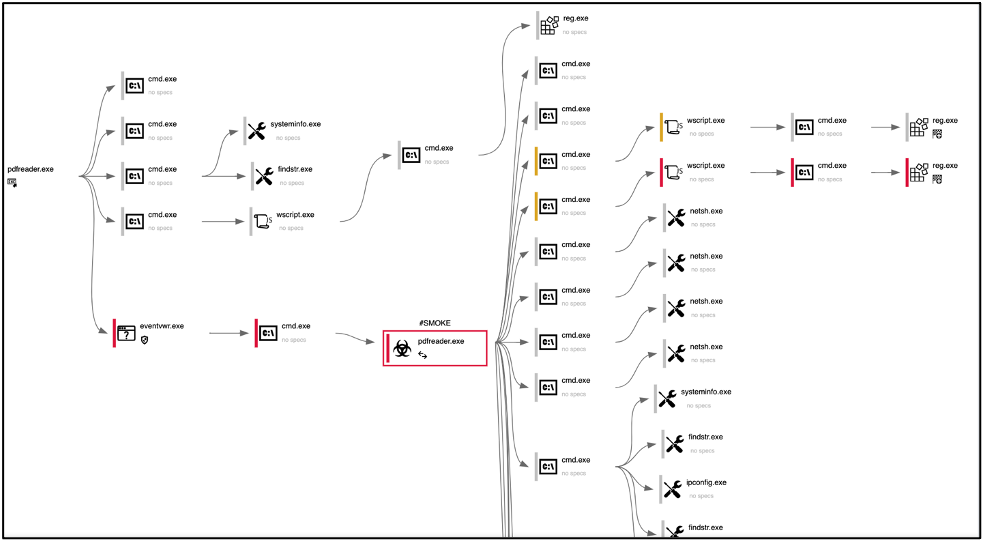
Loader Process Graph
Holiday intelligence Campaign
During the holidays in December and January, APT35 started a targeted phishing campaign of espionage against individuals to gather intelligence. The same tactics, techniques and procedures (TTPs) were used for this intelligence campaign. The campaign started during the time most offices are closed due to the holidays. This was an important step in their campaign because most IT departments were not able to neutralize this cyber event. APT35 took full advantage of this timing to execute this campaign and stack their odds in their favor.
The attack vectors in this campaign were fake SMS and fake emails. The SMS impersonated Google Account Recovery messages and required confirmation by clicking on a hXXs://www.google[.]com/url?q=https://script[.]google[.]com URL. At first glance, the URLs seem legitimate but after opening the links, they perform several redirections and finally lead to a phishing page. The emails were titled “New Year Greetings” and “Merry Xmas and My Gift” with the body of the email mentioning a book as their “gift” to friends and asking the victim’s thoughts on it after downloading it.
The intelligence-gathering tactics in these campaigns worth noting are the following:
- Attacks focused on individuals online accounts
- Gmail
- Yahoo
- Outlook
- Victims’ organizations accounts
- Targeted members of:
- Think tanks
- Political research centers
- University professors
- Countries targeted:
- Persian Gulf
- Europe
- United States
- Attack Vectors include:
- Spearphishing lures related to:
- Health care
- Job postings
- Resumes
- Password policies
- Spearphishing lures related to:
APT35 has been known to use:
- Compromised accounts with credentials harvested from prior operations
- Strategic web compromises
- Password spray attacks against externally facing web applications
- Publicly available webshells
- Associated Malware/Tools:
- Houseblend
- Drubot
- Aspxhellsv
- Pupyrat
- Mangopunch
- Tunna
- Brokeyolk
- Downpaper
- Elvendoor
APT35 Campaigns Timeline
Conclusion
Over the past couple of years, APT35 has conducted spear phishing attacks likely for conducting cyber espionage. It is expected for this threat actor group to continue using this technique as a way to gain an initial foothold into the target’s network. When APT35 was publicly identified in 2014, the targets included U.S. military and government personnel, the UK and Middle Eastern nations on LinkedIn, now the threat actor group has evolved into performing broad strategic and tactical cyber espionage activity. The initial focus of APT35 was to establish contact with the targets via social networking platforms which broaden network reconnaissance opportunities. Establishing fake news domains and personas and creating spear-phishing emails were the first TTPs discovered in 2014. These TTPs remain the foundational blocks of APT’s modus operandi while evolving to pivot into new domains, further increasing its targeting range. APT35 is still active in the cyber landscape and on social media platforms.
| MITRE TTPs: | ID: |
| Account Manipulation: Exchange Email Delegate Permissions | T1098.002 |
| Application Layer Protocol | T1071 |
| Web Protocols | T1071.001 |
| Archive Collected Data: Archive via Utility | T1560.001 |
| Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | T1547.001 |
| Command and Scripting Interpreter: Visual Basic | T1059.005 |
| Command and Scripting Interpreter: Windows Command Shell | T1059.003 |
| Command and Scripting Interpreter: PowerShell | (T1059.001 |
| Credentials from Password Stores: Credentials from Web Browsers | T1555.003 |
| Email Collection: Local Email Collection | T1114.001 |
| File and Directory Discovery | T1083 |
| Hide Artifacts: Hidden Window | T1564.003 |
| Indicator Removal on Host: File Deletion | T1070.004 |
| Ingress Tool Transfer | T1105 |
| Input Capture: Keylogging | T1056.001 |
| Non-Standard Port | T1571 |
| Obfuscated Files or Information | T1027 |
| OS Credential Dumping: LSASS Memory | T1003.001 |
| Phishing: Spearphishing Link | T1566.002 |
| Phishing: Spearphishing Attachment | T1566.001 |
| Phishing: Spearphishing via Service | T1566.003 |
| Process Discovery | T1057 |
| Screen Capture | T1113 |
| System Information Discovery | T1082 |
| System Network Configuration Discovery | T1016 |
| System Owner/User Discovery | T1033 |
| User Execution: Malicious File | T1204.002 |
| Web Service: Bidirectional Communication | T1102.002 |
| IOCs: |
| 54.37.164[.]254 |
| 109.202.99[.]98 |
| 134.19.188[.]242 |
| 134.19.188[.]243 |
| 134.19.188[.]244 |
| 134.19.188[.]246 |
| 185.23.214[.]188 |
| 213.152.176[.]205 |
| 213.152.176[.]206 |
| 146.59.185[.]15 |
| 146.59.185[.]19 |
| 185.23.214[.]187 |
| com-254514785965[.]site |
| mobile[.]verification[.]session[.]com-254514785965[.]site |
| session[.]com-254514785965[.]site |
| verification[.]session[.]com-254514785965[.]site |
| www[.]com-254514785965[.]site |
| com-5464825879854[.]site |
| mobile[.]verify[.]service[.]com-5464825879854[.]site |
| service[.]com-5464825879854[.]site |
| verify[.]service[.]com-5464825879854[.]site |
| www[.]com-5464825879854[.]site |
| benefitsredington[.]ddns[.]net |
| lonelymanshadow[.]ddns[.]net |
| mobile-activity-session[.]site |
| verify[.]mobile-activity-session[.]site |
| www[.]mobile-activity-session[.]site |
| mobile-check-activity[.]site |
| www[.]mobile-check-activity[.]site |
| com[.]recover-session-service[.]site |
| mobile[.]recover-session-service[.]site |
| news12[.]com[.]recover-session-service[.]site |
| recover-session-service[.]site |
| www[.]recover-session-service[.]site |
| hello-planet[.]com |
| mail-newyorker[.]com |
| profilechangeruser[.]ddns[.]net |
| www[.]service-verification[.]site |
| www[.]mobile[.]service-verification[.]site |
| service-verification[.]site |
| mobile[.]service-verification[.]site |
| mail[.]service-verification[.]site |
| com[.]service-verification[.]site |
| app-e[.]request[.]unlock-service[.]accounts[.]service-verification[.]site |
| instagram[.]com[.]service-verification[.]site |
| unlock-service[.]accounts[.]service-verification[.]site |
| request[.]unlock-service[.]accounts[.]service-verification[.]site |
| accounts[.]service-verification[.]site |
| identifier[.]recovery-session[.]site |
| recovery-session[.]site |
| www[.]recovery-session[.]site |
| www[.]identifier[.]recovery-session[.]site |
| identifier[.]session-confirmation[.]site |
| session-confirmation[.]site |
| www[.]session-confirmation[.]site |
| identity-session-recovery[.]site |
| uniquethinksession[.]ddns[.]net |
| recover-identity[.]site |
| session[.]recover-identity[.]site |
| www[.]recover-identity[.]site |
| securelogicalrepository[.]com |
| service-support[.]site |
| customer-session[.]site |
| planet[.]customer-session[.]site |
| accounts[.]customer-session[.]site |
| www[.]customer-session[.]site |
| www[.]service-support[.]site |
| identifier[.]service-support[.]site |
| planet[.]service-support[.]site |
| reset-account[.]com |
| google[.]reset-account[.]com |
| www[.]reset-account[.]com |
| session-customer-activity[.]site |
| verify[.]session-customer-activity[.]site |
| www[.]session-customer-activity[.]site |
| www[.]identifier-service-verify[.]site |
| identifier-service-verify[.]site |
| mobile[.]identifier-service-verify[.]site |
| challengechampions[.]ddns[.]net |
| service-verification-session[.]site |
| mobile[.]service-verification-session[.]site |
| www[.]service-verification-session[.]site |
| chn[.]archiverepositories[.]xyz |
| www[.]archiverepositories[.]xyz |
| archiverepositories[.]xyz |
| a[.]archiverepositories[.]xyz |
| wearefirefighters[.]ddns[.]net |
| basementofdarkness[.]ddns[.]net |
| heisonhisway[.]ddns[.]net |
| recover-session[.]site |
| www[.]recover-session[.]site |
| myaccount[.]recover-session[.]site |
| schoolofculture[.]ddns[.]net |
| customer[.]verification[.]com-3654623478192[.]site |
| com-3654623478192[.]site |
| customer[.]com-3654623478192[.]site |
| www[.]com-3654623478192[.]site |
| verification[.]com-3654623478192[.]site |
| enhanceservicchecke[.]hopto[.]org |
| minimumservicechek[.]ddns[.]net |
| playstore[.]com-apk-6712qw123asd8awf7[.]site |
| www[.]com-apk-6712qw123asd8awf7[.]site |
| www[.]identifier-session-recovery[.]site |
| google[.]com-apk-6712qw123asd8awf7[.]site |
| play[.]google[.]com-apk-6712qw123asd8awf7[.]site |
| identifier-session-recovery[.]site |
| com-apk-6712qw123asd8awf7[.]site |
| agentappservice[.]ddns[.]net |
| www[.]com-archive[.]site |
| com-archive[.]site |
| patchtheschool[.]ddns[.]net |
| www[.]recovery-session-service[.]site |
| mobile[.]recovery-session-service[.]site |
| homeinspections[.]ddns[.]net |
| recovery-session-service[.]site |
| deepthinkingroom[.]ddns[.]net |
| randomworldcity[.]ddns[.]net |
| bulk-approach[.]site |
| www[.]bulk-approach[.]site |
| confirm-identity[.]site |
| www[.]confirm-identity[.]site |
| dynamiceventmanager[.]ddns[.]net |
| service-recovery[.]site |
| differentintegrated[.]ddns[.]net |
| verify-session-service[.]site |
| yahoo[.]verify-session-service[.]site |
| mail[.]yahoo[.]verify-session-service[.]site |
| www[.]verify-session-service[.]site |
| mobile[.]verify-session-service[.]site |
| session[.]recovery-customer-service[.]site |
| recovery-customer-service[.]site |
| www[.]recovery-customer-service[.]site |
| homedirections[.]ddns[.]net |
| recovery-session-verify[.]site |
| www[.]recovery-session-verify[.]site |
| identifier[.]recovery-session-verify[.]site |
| service-session-recovery[.]site |
| mobile[.]service-session-recovery[.]site |
| www[.]service-session-recovery[.]site |
| planet-labs[.]site |
| mail[.]com-posts6712qw12387[.]site |
| video[.]instagram[.]service-recovery[.]site |
| insgram[.]service-recovery[.]site |
| identifier[.]service-recovery[.]site |
| instagram[.]service-recovery[.]site |
| www[.]planet-labs[.]site |
| com-posts6712qw12387[.]site |
| www[.]com-posts6712qw12387[.]site |
| www[.]service-recovery[.]site |
| planet-map[.]gigfa[.]com |
5 Reasons Why Security as a Service is a Competitive Advantage
Fishtech Group was born out of a mission to adapt to the changing cybersecurity landscape. Our Founder and CEO, Gary Fish, previously built the largest cybersecurity solutions provider in North America, but realized today’s cybersecurity challenges are not effectively addressed by those legacy solutions. Thus, Fishtech Group was born.
Data-driven and born in the cloud, Fishtech provides the people, process, and technology to minimize risk, maintain compliance, and increase business efficiency. Our cloud-focused solutions gave way to Fishtech CYDERES, our Security-as-a-Service division, which was created to be an answer to the aforementioned unaddressed challenges brought forth by legacy SIEM solutions, and a direct answer to outdated MSSP models.
Gartner has said that Security-as-a-Service is growing by 16.9% yearly, and solutions like CYDERES that are continuing to improve and drive innovation in the managed security space are a big reason why this segment of the cybersecurity industry is seeing incredible growth.
Let’s look a bit more into this growing space, and how MSSPs, and broader Security-as-a-Service offerings, have grown from being business hindrances to businesses accelerators.
Making MSSPs Better
It’s no secret that MSSPs have a bad reputation. Traditionally with managed services, other people are taking over the control of your data, and don’t always give you visibility into your own information. You’re locked-out of your data, and locked-in to legacy tools.
This has led people to think of MSSP as its own 4 letter “bad” word, regardless of the obvious benefits that MSSPs deliver. Luckily, with the help of CYDERES, this attitude is starting to shift, as more and more organizations are seeing that with the right infrastructure, tools, and personnel, MSSPs can actually be everything they should be, without the flaws of yesteryear. With forward thinking organizations like Fishtech CYDERES, the days of MSSPs as nebulous “alert factories” are beginning to wane.
Here are five competitive advantages that are arising as companies like CYDERES are beginning to reimagine MSSPs for the modern era.
#1 Mitigating Problems Around Frankenstein Tech Stacks of Unvalidated Product Purchases that Become Shelf Ware
It can be easy to get caught up in the hype when hearing about the benefits of all of the various cybersecurity products out on the market. Maybe buying a variety of these products will add up to a net positive? Unfortunately, this is not the case and can lead to overall higher costs and create unforeseen vulnerabilities through this patchwork approach to cybersecurity.
MSSPs like CYDERES already have approaches that are well-tested and well-integrated to make sure there isn’t any dead weight within the tech stack. This leads to better efficiencies, and a more powerful platform that is ready to handle the rigor of the modern cybersecurity threat landscape.
#2 Circumnavigating Costs of Building your Own Security Operations
Organizations have a lot of costs associated with doing business. Trying to add security on top of everything else can seem like an impossible task, especially when trying to go full steam ahead on building out an internal Security Operations Center.
MSSPs like CYDERES are focused on security as a core competency and put the funds forward to accommodate world class talent. Check out our Cyber Defense Center that houses our CYDERES team. We’ve received messages online from folks who have seen the images inside our in-house SOC and have said it looks fake. We assure you, it’s real. It’s just part of our commitment to our professionals that are on the frontlines protecting organizations like yours.
Rather than fighting to find the funds to build out your own SOC, why not leverage facilities that are already tailor made for organizations like yours to fight your everyday threats?
#3 Access to World Class Talent
Speaking of world class talent, the cybersecurity industry is facing a talent shortage which is making it extremely difficult for organizations to attract and retain quality employees. This can be a drain on your organization, as you can become so focused on regular onboarding and offboarding that you surely won’t be making enough progress on building out your security program to adequately protect your organization.
CYDERES can provide the resources to retain the best of the best cybersecurity professionals to add stability and peace of mind for their customers. With Security-as-a-Service, you know you’re getting a quality team with plenty of experience working together, and you’re able to leave HR woes in the past.
#4 Automating and Orchestrating Your Security Programs Increases Efficiency
A big part operating a security program in-house is needing to manage the ins-and-outs of the operation at large. This can also become a huge drain, as you are trying to manage your daily operations, along with the goings-on of your security team at large. Working with an MSSP allows for greater opportunities for automation and orchestration, which can be an enticing prospect for companies looking to streamline cybersecurity within their operations.
Many organizations struggle to keep up with the ever-changing demands of compliance regulations, a sprawling remote workforce, cost-efficient cloud architecture expansion, and much more. Whatever area of your cyber program you are looking to mature, Security-as-a-Service can help you realize cost savings, while minimizing risk and automating predictable outcomes.
#5 Returning the Focus to Growing Your Business, Not Just Managing Your Threats
Relating to the above point, when you’re working with an MSSP, you’re handing over the reins of your cybersecurity program over to the experts so you can focus on what you do best… Growing your business.
Why spread yourself thin? MSSPs like CYDERES easily integrate into your business operations to act as a seamless layer of protection for your organization, without the need to fully manage your security processes. You know your business better than anyone. Gain peace of mind that top teams are on the job while you free yourself from unnecessary distractions that take away from your core focus.
Security-as-a-Service is a Competitive Advantage
With the above points, you can start to get a glimpse into how managed security and Security-as-a-Service offerings can be a boon for your business. Your competitors may be in a position where they are stuck renewing their franken-tech stacks year after year as malicious actors refine their approaches faster than they can respond.
Leading large enterprises are augmenting their security operations with managed security and Security-as-a-Service offerings to allow for more efficient use of time, and more peace of mind. Are you ready to have a conversation about how our Security-as-a-Service offerings can give your organization that clear competitive advantage? Fill out the form below to be connected with one of our experts to see which of our offerings are right for you.
Fishtech and Missouri Career Pathways Partner to Expand Students' Career Horizons
Lights, camera, action!
In partnership with Missouri Career Pathways and local award-winning Stellar Image Studios, we were recently honored to host a visit to Fishtech Group for 7-9th grade educators, giving them a virtual tour of our facilities, including employee interviews to produce a video to teach about career paths, skill sets, and jobs in the cybersecurity industry.
It’s well known that there’s a talent shortage in the cybersecurity industry. Studies show that there just aren’t enough skilled tech force workers to fill the jobs available now, much less to meet the increasing demand of the years to come. In fact, (ISC)2 estimates the cyber workforce needs to increase by 62% to meet demand as businesses invest in technology and cyber threats become more sophisticated. The Bureau of Labor Statistics reports that the industry as a whole will experience job growth of 31% between 2019 and 2029.
Getting young people interested in cybersecurity is important to us at Fishtech, both for our company’s mission and the industry overall. Until the pandemic, we often toured school groups through our headquarters and Cyber Defense Center and held Q&A panels with our staff for students and teachers. Since those initiatives have halted, we’ve missed the interaction and opportunity to inspire and be inspired by those visits.
We were thrilled to work with the Department of Elementary and Secondary Education and its Missouri Career Pathways Program on a recent project involving a very important audience: teachers. Career education is more important now than ever. The first step for educators is to see, experience, and feel the culture of businesses across sectors.
Led by Office Manager Kristy Meyers, the tour included brief interviews with several Fishtech Group employees, all from different parts of our organization. Each was asked to describe the work they do, how their career path led them to Fishtech, what training and education helped them be successful today, and how AI or Machine Learning impacts their work. These interviewees included:
- Chuck Crawford, Chief Strategy Officer
- Ryan Couch, Chief Marketing Officer
- Jennie Hanna, Communications and PR Manager
- Jeremy Hehl, VP CYDERES Business Development
- Todd Bertholf, Contracts Attorney
- Matt Skeen, Director of Information Technology
- Andy Jones, Director of Digital Technologies
- Brandon Ramsey, Senior Software Architect
- Alex Harder, Principal Engineer
During their interviews, you’ll hear that although certifications and specialized training are great, what truly makes a candidate stand out is often more nuanced traits, such as:
- Passion and how to apply it to real-world problems
- Curiosity and how to pursue lifelong learning
- Creativity and collaboration
- Ability to troubleshoot
About Career Pathways: For seven years, Career Pathways has collaborated with Kansas City and NW Missouri region businesses to provide short externship, in-person experiences across a variety of sectors. During Covid times, the department pivoted to a virtual experience.
The theme of this externship is the impact of Artificial Intelligence (AI) in each of the various career pathways, and what it means for the workforce. And the first step to educating the students is making teachers aware so they can ultimately be a resource for their students when it comes to tech and AI-related careers. Fishtech and its security as a service division CYDERES was a successful real-world example for teachers to become more familiar with the footprint of artificial intelligence.
Thank you for this opportunity to reach out to educators and students and tell the story of Fishtech Group:
- Samantha Cole, Northwest Region Career Advisor and Career Pathways Consultant, affiliated with the Northwest Regional Professional Development Center
- Dr. Ann Starlin-Horner, Kansas City Region Career Pathways Director
- Stellar Image Studios for video creation and creative storytelling capability
We work hard, but we play hard too. Watch closely to see Pepper the robot, the nap pod, and the “Golden Bell” Masters Replica Par 3 golf hole and frisbee golf course.
Red Team Operations Interview with Chris Sterbank, Director of CYDERES Red Team Operations
Red Team services can be valuable part of any company’s journey toward ensuring a mature security posture. There have been notable Red Team operations that have made the news over the last couple of years that have painted a very complex picture about this particular practice, but we think it’s important to highlight the various levels at which companies at any point in their journey can utilize Red Team services to accomplish a number of objectives, from simply identifying vulnerabilities, to simulating attacks, and providing valuable resources to help your teams grow and become more secure in their daily activities.
We recently sat down with Chris Sterbank, Director of Red Team Operations at CYDERES, to identify the varying levels of our Red Team offerings and to help shed some light on Red Team operations overall.
—
Hi Chris, thanks for taking the time to talk with us today. Tell us about what you do at Fishtech Group.
Hi, my name is Chris Sterbank and I’m the Director of Red Team Operations at Fishtech CYDERES.
Now, within the Red Team at CYDERES, there are multiple levels at which you engage our customers. What are each of those levels?
That’s right! We offer four distinct levels of varying services to help ensure our client and customers’ security posture. The first level is Attack Surface Management. Level two is Penetration Testing. Level three is Purple Teaming. And level four is Red Teaming.
Let’s dive deeper into Attack Surface Management, and its position as a level one engagement within our Red Team.
Right, so attack surface management offers key services such as Vulnerability Management, where we provide routine discovery of new vulnerabilities and where validated patches are being applied in a timely manner. We can also scan external, internal, and cloud networks, along with web applications.
Another core component of our Attack Surface Management is User Awareness. Part of every organization’s attack surface are their people, right? So, CYDERES can perform phishing exercises on your personnel with detailed metrics and follow-up training. We can use scenarios that are seen in the wild. Ones that have been successful in previous penetration tests along with custom designed scenarios. We believe these services are foundational to any security program and help establish a good baseline in those key areas.
You Mentioned Penetration Testing is the next step within a red team engagement. What differentiates Pen Testing from Attack Surface Management?
Penetration Testing differs from Attack Surface Management in that Vulnerability Management and Attack Surface Management is kind of looking at entire possibilities where Penetration Testing actually tries to exploit those possibilities, right? And this comes after an organization has an established Vulnerability Management program, they have routine patching and upon, of course, introduction of new applications or systems into their network.
A Penetration Test will validate various technical security controls, depending on the type of engagement. So, you might be looking at things such as multifactor authentication, making sure that’s enforced, and maybe looking at enhanced password security, network segmentation, and also making sure things like your endpoint detection response are on point in detecting some of the common threats that are out there.
We do this by offering several different services. We can perform network penetration tests which are both external and internal, and against the cloud. We offer web application penetration testing, wireless, and social engineering engagements in which we will send targeted spear phishing, and vishing attacks against your users and do things such as tailgating into your environments.
Next up, we’re talking Purple Team. How does this ramp up from penetration testing?
Purple Teaming, which is a cooperative assessment between your Blue and Red Team takes organizations to the next level by ensuring your technology and staff can actually detect the most common cyberattacks. These assessments are usually recommended for organizations which have an established Security Operations Center, that centralize logging and alerting and appropriate staffing.
So, by design, these scenarios will sound the alarm and give your personnel hands-on experience with real world tactics and techniques. We will work directly with your team, hand-in-hand, to ensure that the attacks are detected, or gaps in detection are identified. This is great for validating that you have centralized logging, and that it’s in place and actually working, and also detection of common attack types and scenarios.
We offer scenarios, such as password strength, command and control exercises, phishing and vishing scenarios, and also scenarios on the inside of your network, such as information gathering, lateral movement, and privilege escalation.
Lastly, how does Red Team differentiate from Purple Team, and what makes it Level Four within the broader Red Team offerings?
So, our Red Team exercises are no notice, and they can range in size and complexity from individual scenarios, similar to the Purple Teaming, all the way up to a full blown assessment, which tests every facet of your organization to include physical security. Red Teaming will attempt to achieve specific objectives using any in scope means as necessary.
For example, if a company wants us to go after something such as PCI data, it may not require purely cyberattacks. We can always rummage the trash, or maybe find sensitive documents out in the open. The Red Team engagements typically help answer a question: how do we fair when it comes to a dedicated adversary?
Red Teaming will validate whether you have fine-tuned detection, meaning various different types of attack techniques will be deployed, and will also measure your response actions. In addition, it can help validate some threat hunting if you have that available in your organization. These types of scenarios are typically for the most postured and security heightened organizations.
The types of services that we offer there are Red Team exercises, similar to our Purple Teams, but these are no notice exercises, and we will apply different layers of evasive techniques during this, so if you team detects us, we will actually change up our tactics and come back again. Our final service that we offer there is a full-blown Red Team Assessment where there is no scope restrictions, very much objective-based and cyber and physical are all in scope, and they’re typical long duration, six week assessments.
—










