Why Cybersecurity Should Not Be an Afterthought in 2020
As organizations increasingly move their assets to the cloud, cybercrime has continued to mature, and the prominence of cyberattacks has grown. For example, check out our recent blog post on some of the biggest payouts from ransomware attacks in 2019.
Cybersecurity, once a niche faction of a few forward-thinking organizations, is now a central pillar of the modern enterprise… or at least it should be. We read some statistics recently that shocked us.
“To uncover how the world’s leading companies are leading by example to deploy cybersecurity initiatives, Bitglass researched the organizations in the 2019 Fortune 500 and analyzed public-facing information (from what is available on their websites). Here are the Bitglass report findings summarized the 2019 Fortune 500 companies:
- 38 percent of companies are operating without appointing a CISO in position.
- Only 16 percent (of 38 percent) have another executive listed as responsible for cybersecurity strategy, such as a VP of security.
- 62 percent majority do have CISOs but merely 4 percent of them have listed it on their company leadership pages.
- 77 percent of companies have no mention of any individual on their website responsible for security strategy.
- 52 percent of companies do not have any language relating to customer or partner data protection.”
Read again that these are “leading companies” on the Fortune 500. What does that mean for companies all the way down to America’s small business core? The outlook is not rosy.
Frankly, these statistics highlight how behind the times many companies are from an organizational standpoint and highlights the lack of priority security maturity holds within their organizations. Let’s face it, cybersecurity isn’t always the flashiest part of an organization, nor is it viewed as a revenue generator, which often means it becomes an afterthought to businesses with growth on their minds.
Fortunately, many organizations are quickly realizing the truth: the lost time, effort, and money spent fighting trench warfare battles with malicious actors using outdated technology is a much greater growth risk than the upfront cost of ensuring that the solutions are in place.
The choice is clear – prepare wisely and allow your teams to devote their energy into building your business, or fail to plan and risk everything fighting an uphill battle.
Our resolve to help lead organizations to a more secure future has never been stronger. Cybersecurity should NOT be an afterthought, especially in 2020. Having high-level leadership in your company that is responsible for security strategy is vital for long-term growth and success.
The COVID-19 crisis has brought a wave of cyberattacks with it, and unsuspecting companies are really paying the price. Here’s one of our recent blog posts surrounding phishing attacks that are leveraging anxiety around the COVID-19 crises to distribute malware.
As the situation surrounding COVID-19 evolves, and companies continue to find ways to effectively work from home, we suspect we will continue to see a rise in attacks like these, with companies paying hefty prices if they fall victim.
How many sales are now needed to offset the cost of incredibly pricy cyberattack remediation? The cost of preemptive cybersecurity solutions looks like small potatoes in comparison.
Many of these solutions should be getting put in place from the top, but when leadership is not in place to set strategy, as seen in the statistics above, disastrous opportunities arise. So, what can be done?
Apart from recognizing where growth needs to occur within your organization, partnering with a cybersecurity solutions provider can help provide a jumping off point on how to make cybersecurity a more central part of your organization.
Gap assessments are a great place to start. Essentially, these assessments can help identify areas in your organization that may not be fully mature, or spots where you may be more vulnerable. Being able to identify the areas in which your organization is lacking can help to guide strategy moving forward by more effectively focusing on problem areas, rather than on cybersecurity at large.
Secondly, Fishtech Group offer services like “Virtual CISO” through our Strategic Staffing services. Strategic Staffing services provide long-term, skilled resources to help organizations fill in any gaps they may have in their organization’s security team.
With “Virtual CISO” your organization can gain valuable resources like access to experienced cybersecurity and business professionals to bolster your staff for a pre-determined amount of time.
This service can quickly provide vetted leadership to bypass the hurdles that hiring in-house security leadership can bring to the fore. No need to worry about competing with other organizations for low-availability, high-demand, qualified cybersecurity professionals to make sure you can fast track your company to cybersecurity maturity and have confidence as you continue to build out your processes and your team.
There’s too much at stake in the modern business landscape to let cybersecurity and security leadership be an afterthought. Download our fact sheet on our Strategic Staffing services, or fill out the form below to get in contact with our team so we can start having discussions on how we can make cybersecurity a main focus for your organization.
Navigate the troubled waters of 2020, and beyond, with confidence.
CYDERES CNAP Intel Pack
In our ongoing mission to lead organizations to a more secure future, two things are abundantly clear: cybersecurity maturity (people, process, technology) has never been more important, and a truly modern, cost-effective, technology agnostic and reliable cyber defense platform is extremely hard to come by.
Until now.
A robust cyber defense platform that leverages both the power of traditional SIEM features with the latest next-gen practices has finally arrived.
Why? Modern organizations require both the breadth of a traditional SIEM product’s capabilities as well as cutting-edge features like thread hunting support, fast-pivoting, scalable threat intel matching, and more.
Unfortunately, the leading legacy SIEM offerings force a doomed pick between mature but outdated tools with next-gen but incomplete ones.
What if you didn’t have to choose? What if “all the above” was an actual, realizable solution?
The launch of the CYDERES Cloud Native Analytics Platform (CNAP) has brought with it a flood of press releases, videos, articles, and webcasts.
All the same, we know it can be a lot to unpack all of this information in such a piecemeal way. For your convenience, we have put all of our CNAP content below in one easy-to-access place so that you can learn about what CYDERES CNAP is all about and how it can bring unprecedented speed and value to your organization.
If you are ready to harness the power of Google Chronicle (the same tool Google uses to protect itself) with all of the tuned up add-on offerings of CYDERES CNAP, fill out the form at the bottom of this post, and we can schedule some time to talk one-on-one about how we can help your organization.
Let's get started!
1. PRESS RELEASE: CYDERES CNAP Launches
Kansas City, MO (July 16, 2020) — CYDERES, the Security-as-a-Service division of cybersecurity solutions provider Fishtech Group, announces the launch of its Cloud Native Analytics Platform (CNAP, pronounced ‘snap’). CNAP provides a pre-assembled cloud-native SIEM solution delivered in an as-a-Service model, designed to enhance and extend the revolutionary security analytics and unmatched data lake capabilities of the Google Chronicle platform.
2. FACT SHEET WITH CASE STUDY
3. VIDEO: CYDERES CNAP Interview Series
We interviewed Eric Foster, President of CYDERES, to help give you a better idea of what CNAP is, why it was built, and more. Check out a few videos from the interview series below.
https://vimeo.com/434097015/64a087bde0
https://vimeo.com/437890857/8b1958d64a
https://vimeo.com/436531530/ef6660e00d
https://vimeo.com/437887487/6a86b8579d
4. BLOG: Dr. Anton Chuvakin (aka "The Godfather of SIEM") on CNAP
Google Chronicle's Head of Solution Strategy Dr. Anton Chuvakin wrote up a great piece on how Chronicle and CNAP work together to give you the best of traditional and next-gen offerings, culminating in a truly unique and effective solution for organizations in the modern era.
5. WEBCAST SERIES W/ DEMO: How to Modernize Your SOC in a CNAP
To round out the list, we have links to parts 1&2 of the long-form webcast series, "How to Modernize Your SOC in a CNAP". These webcasts dive deeper into CNAP features and offerings, with some live demos sprinkled in as well. These recordings will give you the broadest scope on what CNAP is all about, and it's game-changing abilities.
How to Modernize Your SOC in a CNAP pt. 1
Common legacy SIEM pain points and the what and how of this modern cyber defense platform (including demo of CNAP).
How to Modernize Your SOC in a CNAP pt. 2
The future of cyber defense, the evolution of SIEM and SOC teams, and best practices.
6. Long-Form CNAP Demo with Eric Foster, President of CYDERES
Let Us Know How We Can Help
We hope these resources are a great jumping-off point to learn more about the power of CYDERES CNAP and our partnership with Google Chronicle as we pave the way toward a more secure future for organizations like yours. If you would like to get in contact with one of our professionals to talk more about CNAP, fill out the form below.
Classifying Malware (CYDERES Technical Blog Series)

With the constant rise of cyber-attacks, understanding the type of threat your organization faces is a vital step towards stopping the attack. When it comes to malicious software threats, classifying malware can help answer the following questions:
- Was this a targeted attack?
- If so, who is behind this attack?
- How can we detect and stop this type of attack?
- What is the extent of the damage?
Some sandboxes are able to classify the malware sample, but what happens when the sandbox results come back empty? Analysts can search the web for their cryptographic hash while hoping someone has already stumbled upon this specific malware. Is there a way to compare the similarity of a binary against previously analyzed samples? Yes, there is. The following techniques will help compare a binary against previously classified samples:
- SSDeep
- Imphash
- Section hash
- Yara rules
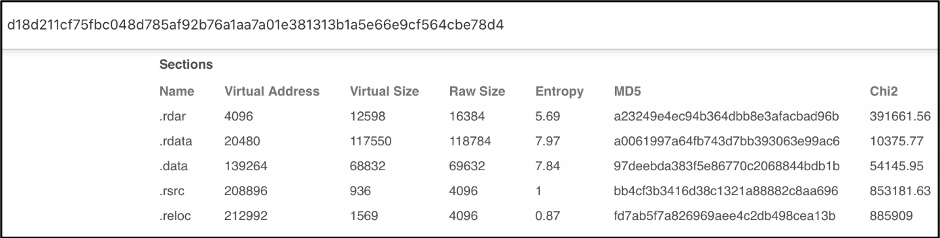
Using a combination of these will ensure the best results. To demonstrate these tools and techniques, the following sample was retrieved from VirusTotal with the hash:
d18d211cf75fbc048d785af92b76a1aa7a01e381313b1a5e66e9cf564cbe78d4
Figure 1: VirusTotal results for the listed hash
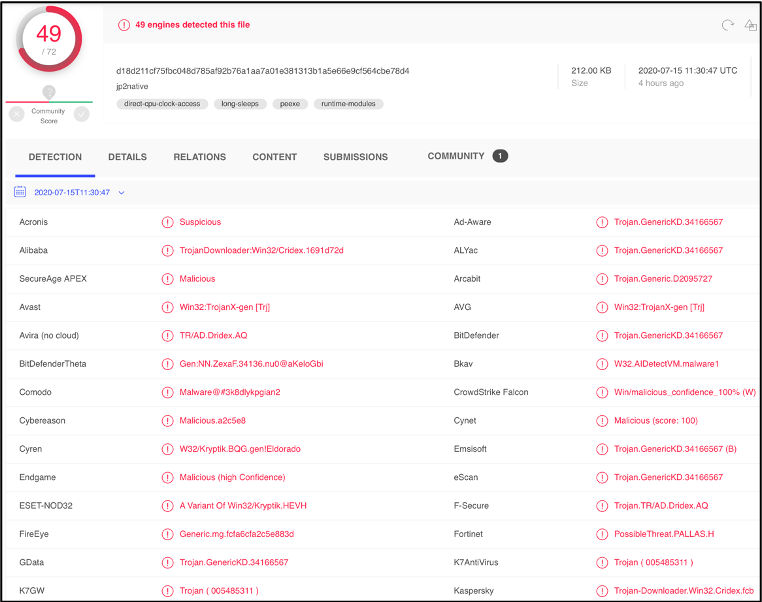
For future reference, this sample will be called Sample 1. We will first look at how these tools and techniques work and then we will compare and classify this sample to previously analyzed samples. Examining the DETECTION section in VirusTotal does not give us much information on the sample’s malware family. However, the DETAILS section lists the Imphash, fuzzy hash, and the section hash which is a great start.
Figure 2: VirusTotal Details section for the listed hash
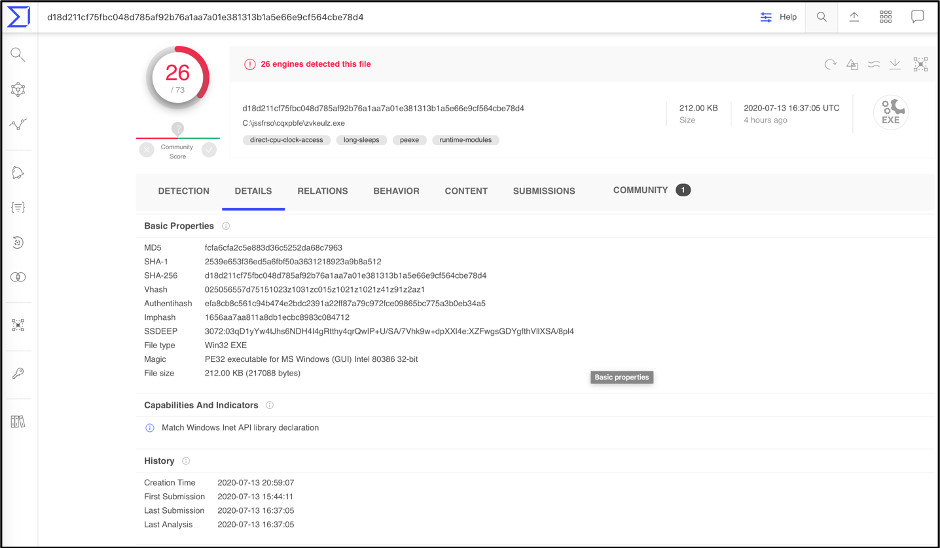
SSDEEP
SSDeep is a tool that generates context triggered piecewise hashes (CTPH), also called fuzzy hashes. CTPH can match inputs that have homologies, or similar relations. Such inputs have sequences of identical bytes in the same order, although bytes in between these sequences may be different in both content and length. The ssdeep tool can be installed locally for Windows and Linux platforms. For information on installing ssdeep, head over to their site. If you have a directory full of previously analyzed samples, the analyst can use the following commands:
$ ssdeep * > fuzzy_hashes.txt
$ ssdeep -m fuzzy_hashes.txt malware.exe
The above command first writes all fuzzy hashes in the working directory to a file named fuzzy_hashes.txt. The second command compares the fuzzy hash (using the matching mode, -m) of malware.exe to the list of previously analyzed samples. Using ssdeep -h will show all the commands that can be used.
IMPHASH
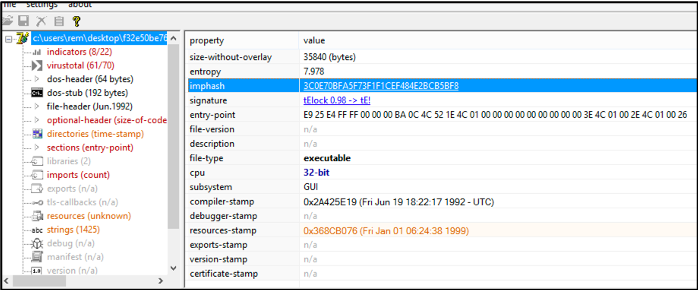
The imphash (Import Hash) is calculated based on the libraby/API names and their specified order within the executable. A quick way to calculate the imphash is to load the binary into PeStudio, as seen below.
Figure 3: PEStudio showing the imphash of a suspect binary
Section Hash
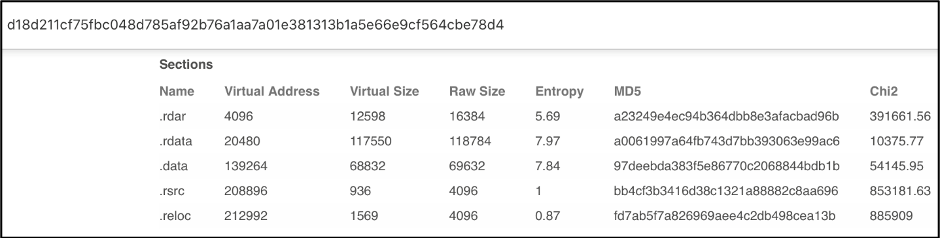
Scrolling down on the DETAILS section of the VirusTotal page, we can see the Sections hash listed. Similar to the imphash, section hash can help identify similar samples.
Figure 4: VirusTotal showing the Sections hash of Sample 1
Comparing and Classifying Sample 1
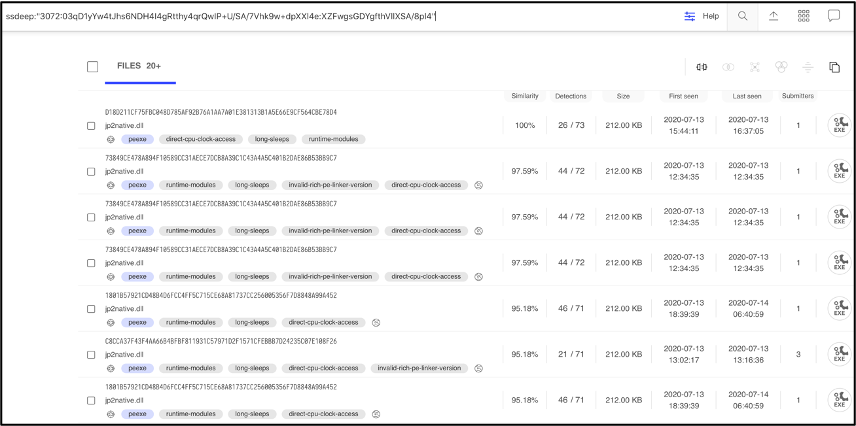
Searching for the fuzzy hash in VirusTotal, results in 20+ samples. Looking at the similarity column shows that the first sample has 100% similarity, which makes sense because this is our initial sample. The second sample has a 97.59% similarity, The higher the number the more similar the files.
Figure 5: VirusTotal showing the fuzzy hash search results
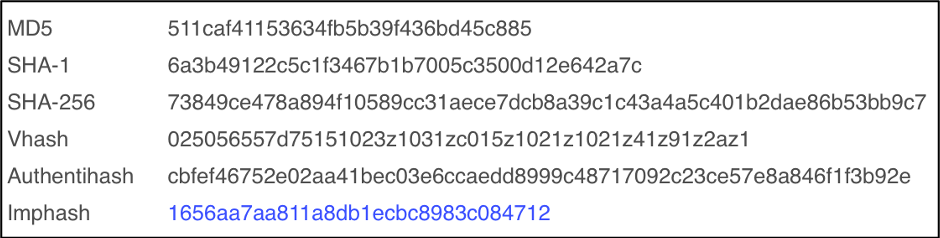
Comparing this 2nd sample to Sample 1, we can see the similarity. Both samples contain the same imphash of 1656aa7aa811a8db1ecbc8983c084712. This means they have the same import address table and were generated by the same builder kit.
Figure 6: VirusTotal showing the Imphash of Sample 1
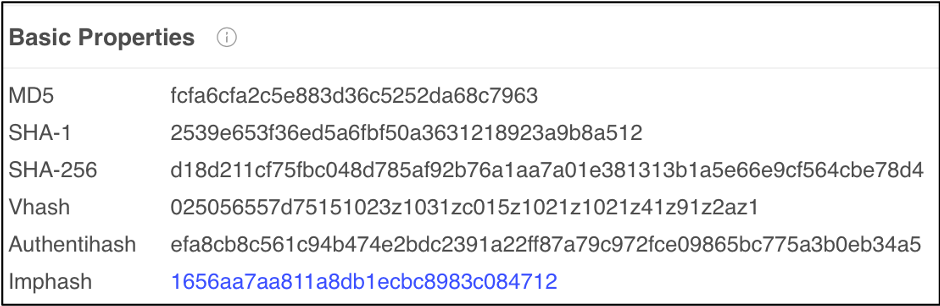
Figure 7: VirusTotal showing the Imphash of Sample 2
Several section hashes match the hashes of Sample 1, 4 out of 5 sections to be exact.
Figure 8: VirusTotal listing the Section hashes of Sample 2
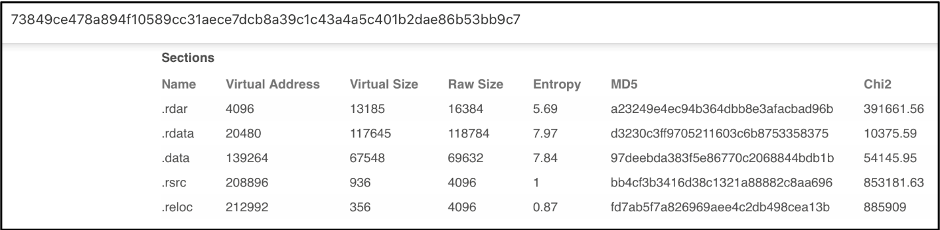
Figure 9: VirusTotal listing the Section hashes of Sample 1
At the time of this writing, a web search for Sample 1 came back empty. A google search of Sample 2 (73849ce478a894f10589cc31aece7dcb8a39c1c43a4a5c401b2dae86b53bb9c7 listed in VirusTotal during our ssdeep search) with a 97.59% similarity, resulted in the following tweet from Vitali Kremez, a well-known security researcher.
Figure 10: Vitali Kremez retweet
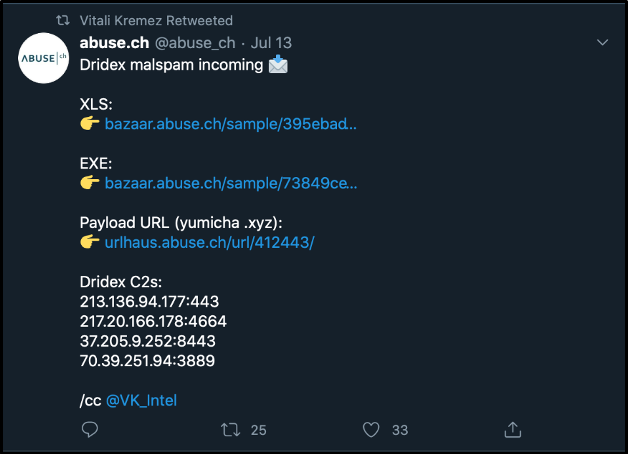
It can be seen from the screenshot that this sample was classified as Dridex. When comparing and classifying malware samples, its important for the analyst to correlate findings with various sources and tools. This brings us to our last topic: Yara rules.
Yara rules
Yara is used by security researchers as a powerful malware classification and identification tool. Once yara is installed on the analyst’s system, rules can be created based on text or binary information contained in the malware sample. A rule consists of three sections:
- Rule name – Name to identify the rule
- Strings – This section contains text or binary information. There are several types of strings the analyst can look for:
- Text strings, with modifiers: nocase, fullword, wide, and ascii.
- Hexadecimal, in combination with wild-cards, jumps, and alternatives.
- Regular expressions, with the same modifiers as text strings.
There are many more advanced conditions you can use, but they are outside the scope of this post. More information on the use of YARA can be found in the YARA documentation.
- Condition – This section contains a Boolean expression, which will specify the condition for the rule to match.
Rule Example
{
strings:
$a = “text1”
$b = “text2”
condition:
($a or $b)
}
To apply what we have learned, let’s create a yara rule that can be scanned against Sample 1. From Vitali’s retweet, we know the 2nd sample has the following indicators of compromise (IOCs):
- Dridex payload URL: hXXp://yumicha.xyz/lvkahex.exe
- Botnet ID: 40400
- Dridex C2s:
213.136.94.177:443
217.20.166.178:4664
37.205.9.252:8443
70.39.251.94:3889
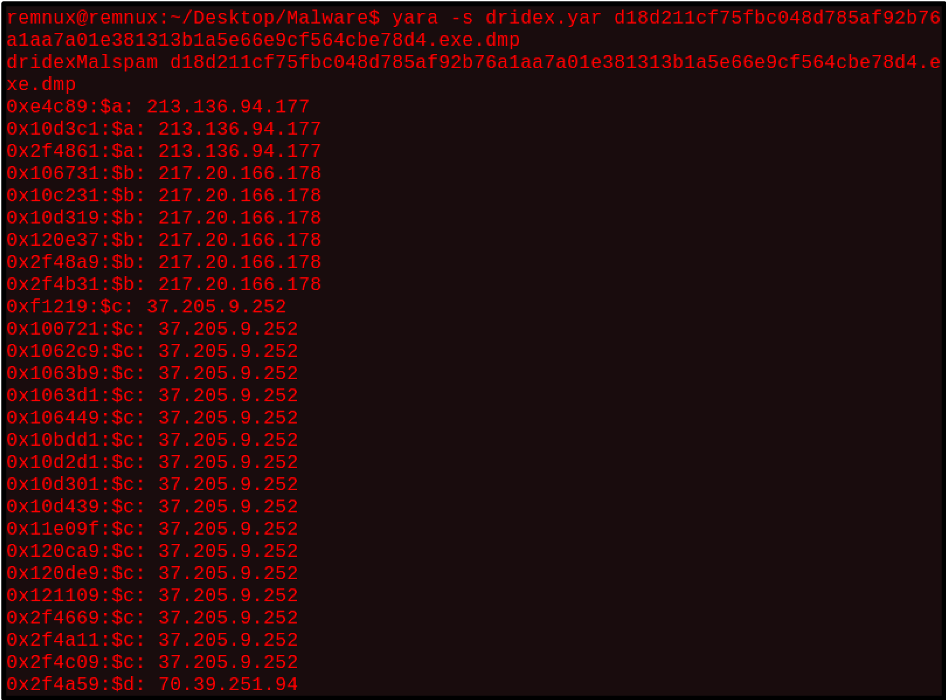
To create this rule, the known Dridex C2s will be used.
Rule dridex
{
strings:
$a = “213.136.94.177”
$b = “217.20.166.178”
$c = “37.205.9.252”
$d = “70.39.251.94”
condition:
($a or $b) and ($c or $d)
}
Running this rule in the terminal against a memory dump from Sample 1 results in a match. Running yara with the -s option, prints the matched strings. From the screenshot, the newly created rule matched on all the dridex C2s from the 2nd sample.
Figure 11: Terminal output of Dridex yara rule scan against Sample 1
As malware authors often make small changes to their samples to thwart analysis, the techniques and tools discussed in this blog will help in classifying and comparing new malware samples. It is a good practice to generate the fuzzy hash, section hash, and imphash of all malware samples you analyze and store these hashes in a repository. Storing these hashes will allow the analyst to compare a new sample and determine similarity.
If your organization needs managed detection and response across both your cloud and on-premise environment, Fishtech Cyber Defense and Response (CYDERES) can help. CYDERES offers a better, faster and scalable SOC with a managed SIEM. CYDERES solutions include:
- Enterprise Managed Detection & Response
- Global Security Operations Center
- CYDERES Cloud
- CYDERES Security Incident Response Team
- CYDERES Red Team
To find out more about what these solutions entail, head over to our services link.
References
https://ssdeep-project.github.io/ssdeep/index.html
Dridex malspam incoming 📩
— abuse.ch (@abuse_ch) July 13, 2020
XLS:
👉 https://t.co/yFguJRpz0G
EXE:
👉 https://t.co/XK9LTSSVr3
Payload URL (yumicha .xyz):
👉 https://t.co/AeXWzZBLm6
Dridex C2s:
213.136.94.177:443
217.20.166.178:4664
37.205.9.252:8443
70.39.251.94:3889
/cc @VK_Intel
The 9 Essentials for a Modern Cyber Defense Platform
A Cyber Defense Platform in 2020 looks much different than it did a decade ago. The rapid adoption of the cloud has added new challenges to the already complex task of protecting your organization's digital assets. On a recent webcast, Eric Foster, President of CYDERES, talked about the nine essential components of a modern cyber defense platform that help give organizations a holistic approach to protecting their businesses from the threats most commonly seen in the contemporary digital landscape. We have broken out each of these essentials below so that you can quickly get insight into these unique areas. Next week, we will be back on the blog with some recent developments from CYDERES, a Fishtech Group venture, and how they have been developing their offerings to help organizations achieve the protection of a modern cyber defense platform. Stay tuned!
SIEM-"NG" for Logs
In modern cyber defense, you need something to store your logs, telemetry, and signals as part of your overall integrated platform. In this first video, we're talking SIEM.
https://vimeo.com/408861997
Analytics with Machine Learning
The next component involves analyzing the telemetry that you have stored. There are certain things that machines are really good at analyzing at scale and at speed, and the integration of analytics with machine learning will allow you to take advantage of the strong suits of this technology to better detect threats to your organization.
https://vimeo.com/408866527
Orchestration & Automation (SOAR)
We've been doing orchestration and automation for as long as we have been doing security. This component is important to make sure your security team can do things better and more efficiently, especially in regard to the most common use cases of your security team.
https://vimeo.com/412447857
Network Traffic Analysis
We are big believers in network traffic analysis as a fundamental component of cyber defense. Someone just coming at things from an endpoint perspective is missing a lot of signals, and missing the ability to put endpoint signals in context. Network traffic analysis helps fill in those gaps.
https://vimeo.com/412455559
User / Entity Behavior Analytics
User- and entity-based signals are important to quickly catch policy violations or the potential that a user's credentials have been stolen, and help to bolster your overall analytics engine.
https://vimeo.com/412457201
Endpoint Sensing
The next piece involves technology that can both sense signals from your endpoint, and then put that signal into your cyber defense platform/analytics engine.
https://vimeo.com/412460201
Threat Intel Enablement
Now that you have all of these signals, all of these logs, and all of this telemetry, being able to analyze all of these for threat intelligence is absolutely critical, especially being able to bounce this intelligence against your historical security telemetry.
https://vimeo.com/412464645
Deception Integration
Deception is one of the single highest-ROI technologies in cybersecurity right now, according to Eric Foster. Deception becomes a high fidelity alert source for detection when threats bypass your other controls.
https://vimeo.com/413279331
Cloud + On-Prem
https://vimeo.com/414814955
Cybersecurity is looking to solve "big data" problems with the modern adoption of the cloud. Everything that you put in place has to be built on a scalable architecture and operate at scale.
Thanks for watching these videos in our cyber defense platform video series, and stay tuned to the blog next week as we dive deeper on some recent developments with CYDERES that you won't want to miss. In the meantime, fill out the form below, and we can get you connected with one of our CYDERES experts to talk more about how we can bring world-class cyber defense to your organization.
What Businesses and Executives Should Know About Their Digital Footprint and OSINT

For the fourth entry in the CYDERES Technical Blog Series, we’re going to be talking about what businesses and executives should know about their digital footprint and OSINT. Open Source Intelligence (OSINT) is the practice of using publicly available resources to gather information (i.e., intelligence) about persons or entities. The information gathered ranges from the relatively harmless, such as information from social media accounts, to more severe data like critical vulnerabilities on public-facing servers, and even login credentials.
This information gathering can take many forms and utilize multiple resources, but the most common method is the use of publicly available information from the internet. Mind you, performing OSINT is perfectly legal. It’s what is done with the data after it has been collected that determines if any laws have been broken, among other factors, i.e., your country’s laws, etc.
The reasons behind performing OSINT vary as much as the methodologies behind it. Still, one of the more common methods is reconnaissance for monetary gain through nefarious means. For example, an adversary can impersonate an employee or business partner requesting the transfer of funds to a specific account perpetrating a business email compromise (BEC) attack. They can also gain (unauthorized) access to a business’s computer network (cloud or on-premises) to steal proprietary or intellectual data, employee PII, credit card/banking information, or even employee credentials. All of this data can be sold in underground markets for monetary gain.
Before an adversary can do this, they must perform reconnaissance utilizing OSINT resources found on the internet to get an understanding of their target – your company. And there’s no shortage of OSINT tools available on the internet; try Googling “OSINT tools” and look at the number of results. The OSINT Framework provides several tools that can be used by anyone to gather information on an individual or company.
Google itself is probably the first OSINT tool that an adversary may use to gather intelligence about your organization. Try Googling your company and see how many hits return. Aside from your company’s web site, there may be results from LinkedIn, Twitter, Facebook; etc., etc. From there, it just becomes easier for the adversary to begin profiling your business, the employees, and other potential avenues that can be exploited to gain access to your network.
One vector of attack that adversaries employ is spear-phishing, and this targets specific employees within an organization. Using the search functions on LinkedIn, adversaries can quickly identify a particular company’s employees by searching for job titles like ‘Accountant’, ‘Payroll Specialist’, ‘HR Representative’ or ‘System Administrator’.
In the example below, an adversary can search for “Fishtech Group” on LinkedIn and then scroll through the employees until individuals with the job title of interest, such as ‘Accountant’ are found.
From there, adversaries can use tools within the OSINT Framework, which includes resources that can either provide specific email addresses for employees or provide typical naming conventions for given businesses.
The information below is found using mailshunt.com via the OSINT Framework web site. Simply typing in ‘fishtech.group’ returns several hits, including an employee’s email address. Now the adversary has names of individuals that can be targeted in the Accounting Department, along with the email format for those employees.
Along with additional information collected from social media sites, company web sites and the like, it’s not hard for an adversary to craft a realistic email impersonating an authority figure in the organization (or a business partner) and request fund transfers or other forms of payment from the targeted employee(s).
In 2019, the FBI recorded 23,755 instances of business email compromises that resulted in more than $1.7 billion in losses to targeted businesses.
Another common technique is looking for leaked credentials. It’s not uncommon for individuals to use the same passwords for both their business and personal accounts, and an adversary will use OSINT to collect leaked credentials associated with an organization, or from the social media accounts of its employees as a potential avenue for compromise.
If the intellectual property or other sensitive information of a business is stored in a cloud service like Concur, Paylocity, Atlassian, etc., it’s not difficult for an opportunistic adversary to identify individuals with access to those sites via social media and use their leaked credentials to gain access to the company’s data.
These are simple examples of how adversaries use OSINT techniques to perform reconnaissance and enumerate your business’s digital footprint. Other potential data sources could include internet-facing servers or applications that have system information posted on sites such as SHODAN, poorly managed cloud assets/applications hosting sensitive data and even a company’s web site “About Us” page could contain useful information for an adversary!
We live in an age where the internet has become ubiquitous and information is just a mouse-click away. Companies are quick to take advantage of this and develop their brand, but in doing so, can expose themselves to opportunistic hackers unwittingly by sharing too much information. The same can be said about a company’s employees. We are all too willing to showcase our skills by posting job titles and responsibilities on sites like LinkedIn to get the attention of future employers.
Sometimes information sharing is necessary; however, companies and their employees should try to limit what is being shared and consider how their digital footprint may empower malicious actors. The good news is that these tools are available to you as well and should be used to profile your company’s exposure for potential threats. Having a process in place to periodically review your company’s online presence can also help to identify sensitive data leaks, risks to brand reputation, and adversary targeting of executives. Whether your organization chooses to perform the research, or employs third-party services, understanding your threat surface is key to protecting your company’s assets.
At CYDERES, we can help you understand your threat surfaces, and secure your business. We will continue to post these technical blog posts on the third Thursday of every month to continue to increase your knowledge on the threats facing your business today, but if you’re ready to talk to us more in depth about the specifics of securing your own business, fill out the form below, and we will put you in contact with one of our experts. Stay tuned for our next article in July!
Identity Governance: Putting It All Together (Video)
As the global business landscape continues to shift, organizations are learning what it takes to secure and scale a remote workforce efficiently. As this “new normal” emerges, a robust identity program must align with an organization’s compliance objectives and combine to form a robust solution set that enables business growth.
In order to address the related financial, legal, operational, and reputational risks, Identity Governance combines a prescriptive blueprint for effectively identifying and converging the foundational pillars of IAM with a right-sized and resilient GRC solution/program. Importantly, this also incorporates a Zero Trust Model of relevant security and technical controls.
As a result, organizations are able to prioritize, manage, and mitigate cyber risks that align with their business goals and objectives.
In part three of our ongoing webcast series Why Identity Governance Really Matters Fishtech Group experts flesh out the ideas covered in the first two webcasts and show practical and relevant examples on how Identity Governance can help you protect your business with modern strategies.
Missed Part 1? Catch the full replay on demand.
Highlights from Recent Webcasts
As organizations across the world have adapted to large-scale remote workforces, our teams continue to work hard to virtually help our clients minimize risk, maximize efficiency, and maintain compliance. As we do, we’ve made it our aim to grow the amount of education and demonstration about these real-world solutions via our live webcasts.
To make it easier to parse through each webcast to find the discussions that provide the most value to you, we’ve put together a few highlight clips from the four most recent webcasts to help you get a feel for the discussions and subject matter. We will provide links to each webcast under each clip, or you can visit the full page of all of our recent webcasts here.
Enable Your Business to Move Faster & More Securely with Governance As Code
Whether you are in development, operations, or security, DevOps is no doubt on your radar. As enterprises increasingly leverage the cloud to host business applications as part of their digital transformation, security and development teams need to transform how they work together.
In this moderated webinar panel discussion, hear from cybersecurity experts as they address best practices to bridge the gap between InfoSec and DevOps and the principles of security being part of the DevOps evolution. In addition, this webinar will address the following questions:
- How do you ensure compliance controls into your cloud native infrastructure?
- How do I ensure my developers can move quickly while remaining compliant and secure?
- How do you bring all the right technologies together successfully as you go down the automation journey?
- What are the best practices around Governance as Code to spin up resources and configure and manage them on day one, day two, and beyond?
Back to the Office: Solutions for the New Risk Landscape
After an incredibly quick shift to support remote workforces on a massive scale, businesses are now beginning plans to allow their teams back into corporate offices.
As this planning occurs, it is vital to understand what reactionary changes had to be made to accommodate the business needs of remote workers. Fresh strategies and opportunities MUST be identified in order to improve security, governance, and architecture.
This webinar sponsored by Fishtech Group, CyberArk, Ping, and SailPoint focuses on the potential risks that were allowed to accommodate remote workers, how to identify improvement opportunities, and how to apply those solutions from a Strategy, Governance, and Architecture perspective.
Link to full webcast here.
Insider Threat Mitigation: How to Identify, Prioritize and Protect Critical Assets
One of the most overlooked aspects of effective insider threat mitigation is the identification of an organization’s critical assets, which can include intellectual property, people, facilities, systems, customer data, and more.
This webinar will explain why and how to identify the critical assets in your company. We will present a step by step approach to identifying and validating critical assets, identifying and assessing the threats to those assets, evaluating risk appetite and tolerance, and prioritizing the most critical assets.
Participants in the webinar will learn:
- The importance of defining critical assets
- An approach to identify critical assets
- An approach to identify threats to critical assets
- The impact of critical assets on deterrence and protection activities
- The impact of critical assets on detection activities
This approach will help you establish a consistent and recurring process to protect your company’s critical assets against insider attacks.
Link to full webcast here.
Demand More From Your Cloud PAM
Attend this webinar to learn how Cloud PAM differs drastically from a traditional on-premise solution. Saviynt and Fishtech will discuss client use cases and why a PAM solution needs to be cloud-architected and cloud-delivered to reduce risk, contain cost, and secure identities for applications, data, and infrastructure.
In addition, join us to discuss the following topics:
- How the risk of privileges in the cloud differs from traditional PAM and how to manage the velocity and scale of those changes
- How gaps in legacy PAM solution fail to accommodate the volume of change in the cloud
- How a single solution can meet PAM needs for both IaaS and SaaS
- How to meet the challenges of a multi-cloud ecosystem
- How to secure next-generation cloud workloads including instances/containers, cloud databases, serverless functions and APIs.
- Governing privileged access in your Hybrid Enterprise
Link to full webcast here.
Business Continuity Planning – A Global Case Study
Paying lip service to business continuity planning when times are calm and uneventful is one thing – who’s going to call you on that? It’s a completely different thing when there is a global pandemic that’s providing a true test across the board for organizations’ business continuity plans around the globe.
The impact may feel slightly lessened now that we have been in middle of the COVID-19 pandemic for the last few months, but to drive home the obvious, this was a truly unexpected event that shook many businesses to the core. “But, how could we have planned for a global pandemic?” That is a valid question. Ask anyone a year ago about what the greatest challenges to their business would be in 2020, and very few (if any) would mention anything even slightly resembling the word “coronavirus”.
The more apt question to consider is “how can we plan for future disruptions to our business?” To answer it, let’s start with a question of our own – when was the last time your senior leadership conducted a run through of various scenarios to strengthen the readiness of your corporate assets? Maybe it was pre-COVID-19. If so, that likely had a direct effect on how your organization has adapted to this crisis.
Making Your Business Continuity Plan Work for Your Business
At any time, unforeseen circumstances beyond a company’s control can influence the operational status of a business. To wait until these circumstances are knocking at your door is to throw caution to the wind, at potentially great costs to your organization and employees. The most successful businesses have a series of plans and strategies ready for any challenges that may come their way.
To start, key stakeholders should regularly monitor incidents that may cause a business disruption and/or have a serious impact to operations. It does no good to take a “set it and forget it” approach. The crucial word to look at for business that are ready pre- and post-disruption is “adaptability”. If you put a plan in place that does not adapt to your environment, or to changes in your organization, you will not be adequately prepared to weather the huge challenges that can occur at the drop of a hat.
A business continuity program should ensure Business Continuity Plans are applicable to relevant, realistic risks, and threats to their critical operations. This means adapting more of a playbook mentality, rather than a rigid series of step-by-step protocols. Several companies we have worked with already have business continuity plans in place, but they are oftentimes untested or ill-suited for evolving conditions and potential threats.
Business Continuity management should include strategies and playbooks around:
- Comprehension of basic Business Continuity principles and methods
- Ensuring consistency in business impact analysis to identify critical business functions
- Understanding of the correlation between operations, business continuity, IT disaster recovery, and emergency planning
- Ensuring that the Business Continuity Plan reflects the current hazard risk analysis, mitigation processes, business impact analysis, response management, and recovery strategies
- Encouraging coordination between all company staff while implementing a Business Continuity Plan
- Identifying and initiating appropriate, cost-effective strategies and procedures to recover critical business functions and information assets
- Formally assigning Business Continuity responsibilities to appropriate leadership and ensuring each receives proper training to implement the Business Continuity Plan
- Ensuring that necessary contractual agreements exist for recovery of critical business functions and information resources
- Reviewing, updating, and communicating Business Continuity content changes
- Continually improving the Business Continuity Plan as required
- Testing Business Continuity plans at least annually.
- Conducting Tabletop exercises with senior leadership, so that your business knows what to do in the event of a national, global, or disrupting event.
A list of that caliber can seem daunting, but so are the emergencies they are in place to mitigate. If the strategies above are taken correctly, you can move forward confidently with your organization knowing that you have a plan in place for the next “COVID-19” caliber surprise.
Even a cursory look at the impact this crisis has had on the global business landscape reveals the shocking truth – some organizations have adapted well, and others have failed spectacularly. There are so many examples to show the power of a solid Business Continuity Plan, or lack thereof. It truly is a global case study with a single event as the control. The value of Business Continuity Planning, especially during the digital era, has never been more apparent.
Many organizations rely on us to help them navigate these troubled waters into secure digital transformation. If you are looking for a seasoned guide, let our experts at Fishtech Group help you begin the next steps toward a robust Business Continuity Plan with a number of exercises and actionable steps to help lead your organization to a more secure future. As your team continues to discuss this critical issue, fill out the form below and let us know how we can help.
COVID-19 Phishing and Malware Distribution - CYDERES Technical Blog Series

Executive Summary
“Flattening the curve” refers to efforts to implement community isolation and personal hygiene measures that help keep COVID-19 cases at a manageable level for medical practitioners. In the digital world, you can flatten the curve of COVID-19 phishing incidents by staying vigilant and practicing good email security hygiene. Attackers have adapted to this pandemic by using COVID-19 lures to deliver malware and direct victims to phishing sites, taking advantage of the current global situation and how humans react during stressful times.
The purpose of this blog is to keep you informed on the current phishing emails being delivered to your inbox. Staying updated on trends in the usage of COVID-19 and other lure themes will help your organization stay protected.
COVID-19 Phishing and Malware distribution
Attackers have long taken advantage of public anxiety surrounding global and regional crises and the current pandemic is no exception. During the 1st quarter of 2020, we have observed a significant number of phishing emails leveraging COVID-19 themes. These emails have included attachments or URLs commonly leading to phishing sites or malware such as Lokibot, NanoCore, and other Remote Administration Tools (RATs). Some recently observed email subjects include the following:
- You missed a call Corona Update
- CDC HEALTH emergency coronavirus COVID-19 Pandemic
- COVID Report
- COVID-19 Payroll Adjustment
- Security Update Stimulus Check Failed
Conducting analysis on an example phishing email resulted in some interesting findings. The following screenshot shows the email subject and attachment but no content. The “From:” section shows “+1917-3757-6473 Notice@nhaschools.com”. “Nhaschools[.]com” is the site for a US National Heritage Academy charter school. At first glance a victim with children attending this school might open the attachment if they see the school’s name and the phrase “Corona update” on the subject line. Other victims might open the attachment to read any information related to the current pandemic.

Looking at the headers, specifically the sender “IP” and “Return path”, we see the following information:
Sender IP: 52.231.152.110
Return-Path: r-nishikawa@ecru-color.com
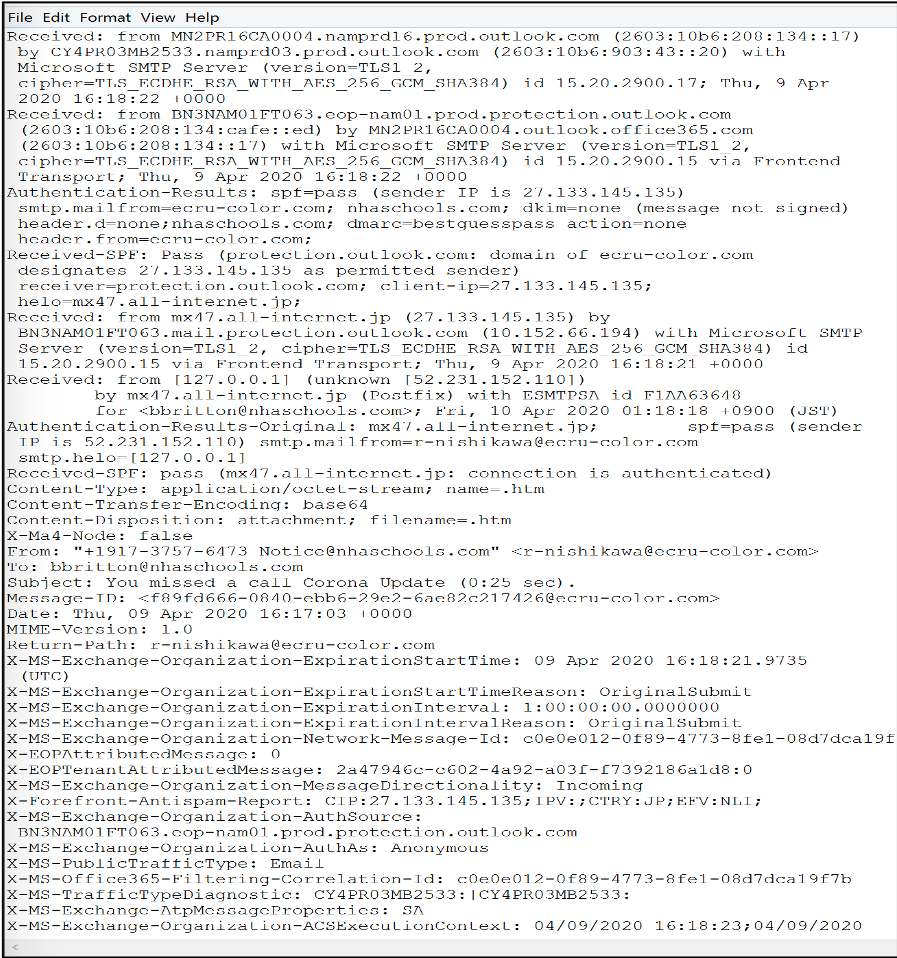
“You missed a call Corona Update” Email headers
The sender IP can be traced back to South Korea and ecru-color.com appears to be a Japanese styling salon school.
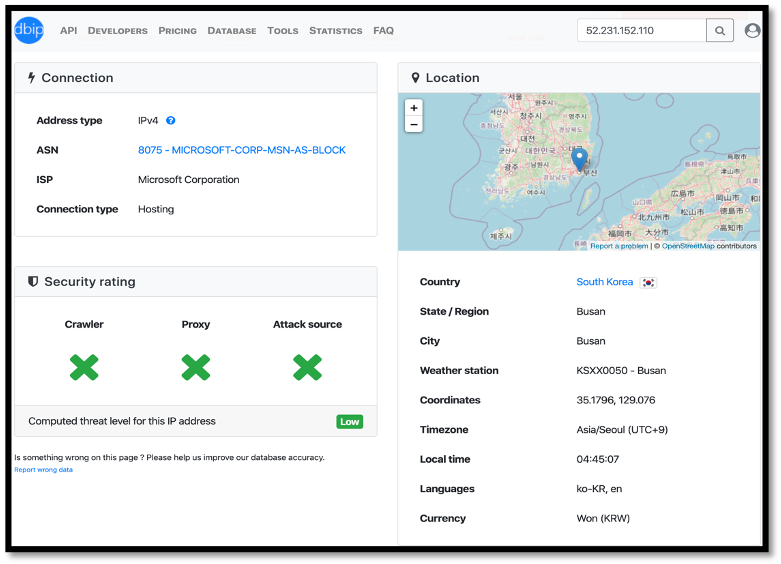
Sender IP Geo Location
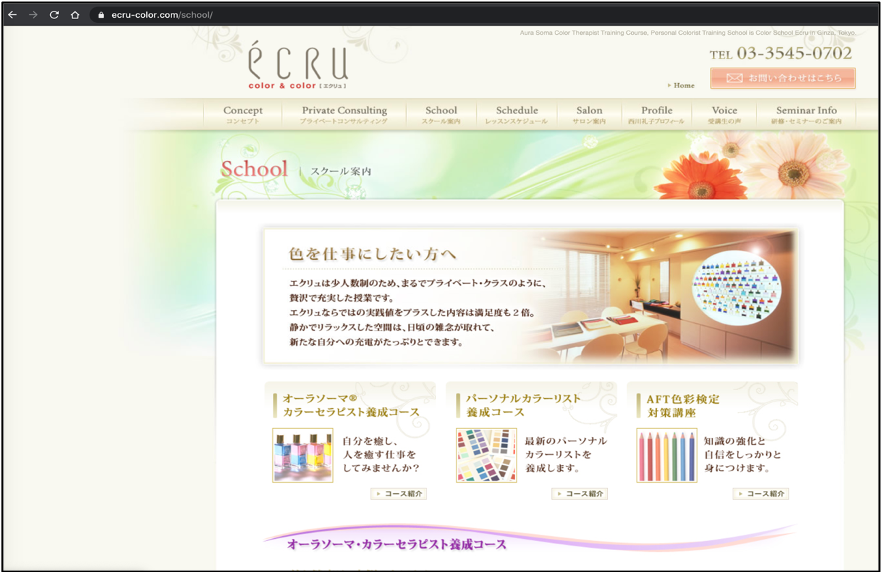
Domain from the Return path address
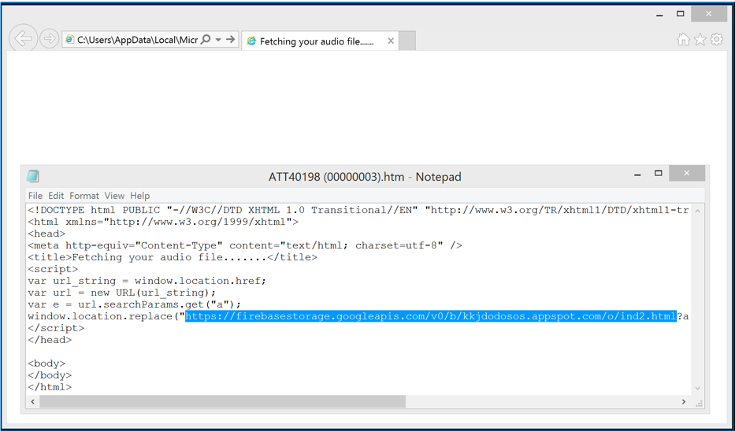
Returning to the email and opening the attachment in a virtual machine, shows the attachment opening a .html document from the email which pretends to be an online web page. These types of phishing emails play a vague voicemail message before the victim is redirected to a phishing page. Performing a right click and selecting view source, shows us the script being used.
Performing a quick google search shows it’s been scanned by the site urlscan.io, 10 times. As we can see, it is an Outlook Web App phishing page which was still active at the time of this writing.
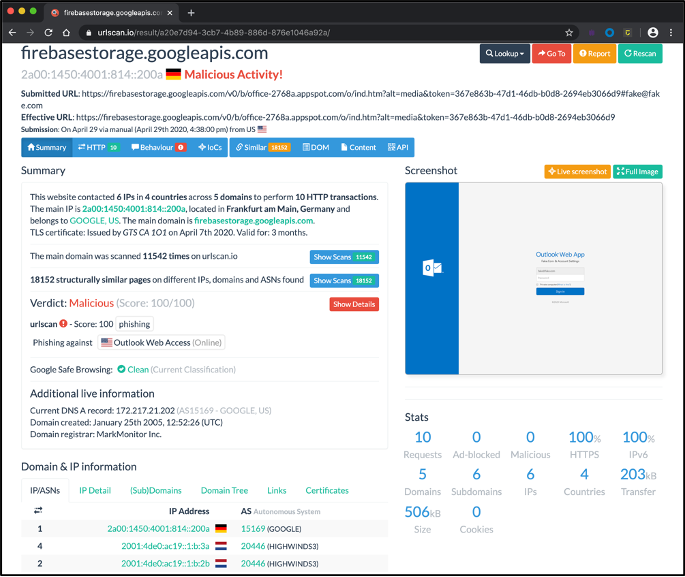
Attackers leverage free, compromised, and dedicated infrastructure to host COVID-19-themed phishing content.
Some examples of recently observed URLs include the following:
- hXXps://cnncoronavirus[.]000webhostapp[.]com/
- hXXps://c0vid19-aid-ca[.]org/
- hXXps://cecollc[.]com/infrastructure/covid/FBG/
- hXXp://coronana[.]000webhostapp[.]com/
- hXXp://gift-covid19[.]000webhostapp[.]com/
How you can stay safe:
While email spam using COVID-19 themes are a relatively new and increasingly prevalent phenomenon, these lures ultimately leverage common social engineering tactics capitalizing on sentiments of fear, anxiety, and curiosity. Once this theme runs its course and dwindles in popularity, it will undoubtedly be replaced by a mix of themes related to current events and common phishing themes like financial transaction, parcel delivery, and file sharing. The positive news is that users can protect themselves from these tactics by improving their awareness and practicing basic security hygiene.
Technology can help to protect users from many of the attacks that attempt to reach inboxes; however, education is the best defense against the phishing attacks that inevitably make it past these defenses. Staying up to date on phishing lure themes that are currently being used and learning how to spot a phishing email will help you flatten the curve.
When reading your emails, ask yourself the following questions:
- Does this email contain a personalized greeting?
If not, it’s likely unsolicited and may be a phishing email, so proceed with caution.
- Is this email attempting to instill fear or a sense of urgency to convince me to act?
If yes, it may a phishing email, so proceed with caution.
- Are there basic grammatical or spelling errors in this email?
If yes, it may a phishing email, so proceed with caution.
- When hovering over links, do I see any signs that they may be malicious?
If you cannot identify the link as a trusted resource, it may be a phishing email, so proceed with caution.
- Do I recognize the sender and was I expecting an email from them?
If not, it may be a phishing email, so proceed with caution.
- Are any brand names being used in the email?
Attackers often use logos to create convincing phishing email, so proceed with caution.
We can help your organization flatten the curve
What is better than technology and education? A combination of human-led and machine-driven security as a service. CYDERES’ 24/7 security as a service gives you the people, process, and technology to help organizations manage cybersecurity risks, detect threats, and respond to security incidents in real time. Take a look below at some of the benefits of having a team of security professionals detecting and mitigating your organization’s threats. For more information, visit our site and download the full services factsheet at: https://fishtech.group/solutions/security/
- Managed 24x7x365 Security Operations Center (Tiers 1-4)
- Threat detection and triage for all technologies
- Security incident response
- Proactive threat hunting
- Build playbooks (phishing, malware, lateral movement)
- Endpoint detection & response management
- Sole EMDR 100% powered by Chronicle Backstory
- Backstory forwarder 24×7 management and monitoring
- Custom Backstory integrations/parsers
Identity Governance: The Starting Point (Video)
As the global business landscape continues to shift, organizations are learning what it takes to secure and scale a remote workforce efficiently. As this “new normal” emerges, a robust identity program must align with an organization’s compliance objectives and combine to form a robust solution set that enables business growth.
In order to address the related financial, legal, operational, and reputational risks, Identity Governance combines a prescriptive blueprint for effectively identifying and converging the foundational pillars of IAM with a right-sized and resilient GRC solution/program. Importantly, this also incorporates a Zero Trust Model of relevant security and technical controls.
As a result, organizations are able to prioritize, manage, and mitigate cyber risks that align with their business goals and objectives.
In part two of our ongoing webcast series Why Identity Governance Really Matters Fishtech Group experts describe best practices and winning solutions that we are architecting for customers every day.
Missed Part 1? Catch the full replay on demand.










