Talking Security Operations with CYDERES Chief Operating Officer Mike Wyatt
November 16, 2021Cybersecurity Insights
Modern threats require modern security operations. This is a topic we have covered a number of times over the past year. In fact, we presented at the Google Cloud Security Summit on this very subject. In that presentation, our CYDERES Chief Technology Officer Tim MalcomVetter, and CYDERES Chief Operating Officer Mike Wyatt spoke broadly about the top security challenges modern organizations are facing, and how we’re developing and implementing proven, modern solutions for our customers.
For today’s blog post, we put together a few videos from our interview with CYDERES COO Mike Wyatt, including items that were outside of the scope of the original presentation, in order to give you an even fuller insight on what modern security operations look like, and how you can utilize our expertise to help you combat the modern threats of today. If you have any questions, fill out the form at the bottom of the page to be connected with one of our CYDERES experts. Let’s get started!
What are the Top Security Challenges of the Modern Risk Landscape?
Many organizations are hearing a lot of noise surrounding modern cyber threats, and can get lost trying to make heads or tails of where to prioritize their efforts. CYDERES Chief Operating Officer Mike Wyatt discusses some of the top security challenges of the modern risk landscape to help illuminate a few priorities to keep in mind.
Why Does As-A-Service Make Sense in Today’s Environment?
Once priorities have been established for organizations in the modern risk landscape, many are left wondering how to proceed with how to adequately protect themselves. Partnering with an MSSP can open up so many possibilities as you tap into the expertise and resources found within managed security that may be difficult to leverage in-house.
Unlocking 24/7 Response Capabilities
One of the key components that MSSPs can unlock for your organization is 24/7 response capabilities. It’s one thing to be able to detect threats, but are you able to respond to them in pivotal moments, even in off-business hours? Mike expands on the benefits of 24/7 response capabilities, and on the value our EMDR offering brings.
Learn More, Act Faster with CNAP 2.0
Mike dives into our CNAP 2.0 offering and all of the recent additions that have helped make our Cloud Native Analytics Platform a powerful tool for organizations looking to modernize their security operations.
Winning Solutions that Leading Organizations are Adopting
We get a lot of questions regarding our partnership with Google Chronicle and how that is being leveraged to create winning solutions for leading organizations. Mike expands on the capabilities of Chronicle and how that leads to better results for faster identification of threats to your environment.
We’re Growing!
Interested in joining our team? We’re growing quickly and would love to have you on board. Visit our Careers page to see our current job opportunities.
If you have any questions, or would like to know more about CYDERES, fill out the form below to be connected with one of our experts.
CYDERES Insider Threat Profiles: The Compromised Accountholder
November 2, 2021Cybersecurity Insights
Across the spectrum of insider threat scenarios, account compromise is in a category by itself. Unlike data theft or fraud or sabotage, employees whose email accounts have been hacked are widely considered to be negligent or unwitting victims rather than malicious perpetrators.
Still, the harm such compromises can cause is significant since they’re usually precursors to instances of actual data theft, fraud, sabotage or other malfeasance once the attacker has gained access to the network.
And when the account in question belongs to the organization’s most trusted employees, their privileged access to systems and corporate ‘crown jewels’ means the financial, legal and reputational damage will be altogether worse.
The FBI has extensively studied what it calls “business email compromise” and has created a web page with detailed definitions of the problem, a list of information resources and a section called “How To Protect Yourself.” It’s worth a read.
What’s important to keep in mind is that account compromise is not a one-dimensional problem – and nor is the solution. Instead, mitigation involves a combination of measures involving people, process and technology. Here are some tried and true recommendations for each area.
People
Account compromises are a growing problem mainly because of the weakest link: people. According to IBM’s Cyber Security Intelligence Index report, 95% of all successful cyber breaches are caused by human error. And with more employees now working remotely using a hodge-podge of devices and non-secure networks, the chances of an attack against an unwitting or negligent user will increase proportionally.
The most impactful way to reduce account compromise risk, therefore, is to focus on the human element, ensuring all staff and management remain vigilant and can recognize potential compromise attempts – for instance a spear-phishing attack. Much can be accomplished through continuous training and education programs. And practicing good security hygiene, such as strengthening passwords and keeping software up to date, will pay immediate dividends.
Process
Security policies must be clear, and repeatedly messaged across all departments. Then, the right processes must be implemented to support those policies, and relevant staff trained to carry them out. Implementing and enforcing strong access control procedures and conducting regular penetration testing and red-teaming simulations are good practices, as are requiring multi-factor authentication and even old-school phone confirmations to verify fund transfers. And a key requirement is ensuring that the security team knows how to respond to potential account compromise incidents as they emerge, since time is of the essence.
Technology
Even businesses with the most prepared workforce and sound security processes will suffer account breaches, but the right cybersecurity tools will add much-needed layers of defense. For those account compromise attempts that do succeed, however, early detection and response are crucial.
Many of the same technologies organizations use to detect external threats and malicious insiders – like user entity behavior analysis (UEBA) and security information and event management (SIEM) tools – can be employed to find compromised accounts as well.
The CYDERES Insider Threat Detection & Response (ITDR) solution is one recent entry into the field. Through the ingestion of security data into our CYDERES Cloud Native Analytics Platform (CNAP), ITDR can analyze a wealth of network and user telemetry for signals of insider threat activity, including account compromise.
Like other tools, ITDR detects the behaviors most commonly associated with credential takeovers (or insiders being managed) by outside parties, including unusual login volumes, logins from pre-defined high-risk locations and geographically/temporally impossible login sequences. These cases often lead to data exfiltration, sabotage or ransom attempts.
But ITDR takes detection and response several steps further than traditional SIEM, UEBA and SOC combinations. For one thing, it’s a 24/7 managed service, so there’s no software to buy and no learning curve for SOC staff. Another key differentiator is CYDERES’s use of so-called Bayesian models to provide additional analytic context – thus filtering out many of the false-positive alerts and other noise generated by most SIEMs. It’s the model that does the risk scoring and prioritizing, not the SOC analyst.
ITDR additionally can ingest and analyze any number of non-network data sources, enabling it to, for example, give more weight to events involving privileged vs. non-privileged users, reveal additional types of employee attitudes and stressors and even assess seemingly mundane information such as the dates an employee is out of the office – a prime time for being impersonated.
Since there is rarely malicious intent on the part of the compromised accountholder, the ITDR model also was designed to ingest and analyze more qualitative data that could reveal other potentially risky shortcomings, such as a tendency towards carelessness or even outright negligence. Such information is applied to model nodes with names like [Unwillingness to comply with established rules and procedures].
ITDR analytic results are risk-scored and prioritized using this additional context, and then triaged further by a CYDERES analyst, so that the customer knows exactly which incident alerts need the most immediate attention.
The alerts and related evidence can be used to launch investigations and recover from breaches, but they also form the basis for complying with legal and audit requirements associated with such activity – and for reducing future account compromise risk via policy and control changes.
# # #
Note: This blog post is one in a series of CYDERES insider threat profiles. We recently covered IP theft, and will address fraud and sabotage in future posts. For more information, please click on this link to view our two-minute ITDR intro video.
Cybersecurity Awareness Month 2021 Recap
October 29, 2021Cybersecurity Insights
As October comes to an end, so too does another Cybersecurity Awareness Month. All month long we have been aiming to produce helpful and fun content to help our community and clients #BeCyberSmart.
We hope you were able to catch a couple of the items we released over the last 30 days, and that it empowered you to own your role in protecting your part of cyberspace. If you missed anything, we have you covered.
In today’s blog post, we’re looking back on each of the four weekly themes from Cybersecurity Awareness Month and highlighting a few of the pieces we released along the way. If you have any further questions about how you can do your part to #BeCyberSmart, reach out to us using the form at the bottom of this blog post. Let’s get started!
Week 1 – Be Cyber Smart
We set the table for the month to come during the first week of Cybersecurity Awareness Month, with the week one theme matching the overall theme for this pivotal month. We began to solicit questions from the community to prep for our end-of-month #AskFishtech webcast (more on that below).

We wanted to keep things fun while we helped our community learn more about cybersecurity. With this in mind, we put together a quick crossword puzzle. Let us know if you solved it!
Finally, for week one, we put together a Cybersecurity Quick Refresh Guide on our blog to highlight some basic, but important tips on how you can bolster your personal security to protect your information and access to your online assets.
Week 2 – Phight the Phish
For week two, we turned our focus to phishing and ways to combat this growing threat. For context, phishing incidents more than doubled in frequency in 2020 from 114,702 in 2019 to 241,324 in 2020.
We took the theme of “Phight the Phish” quite literally, and put together a comic strip with some helpful tips to combat phishing. Check it out!
Lastly, we sat down with CYDERES Chief Technology Officer Tim MalcomVetter to get his tips for CISOs tackling phishing in 2021 and beyond.
Week 3 – Explore. Experience. Share. (Cybersecurity Career Awareness Week)
For week three, we got to focus on something near and dear to our hearts – promoting cybersecurity careers! We have long been big proponents of school age children starting to look into all of the possibilities that the cybersecurity industry offers. In fact, the global cybersecurity market size is projected to grow from USD 217.9 billion in 2021 to USD 345.4 billion by 2026. That means a lot of job opportunities on the horizon!
To get a deeper insight on what some of the careers look like at our organization currently, we talked with CYDERES Chief Operating Officer Mike Wyatt to hear about the various roles found in our organization.
To highlight even more careers at Fishtech Group, we put together a quick collage from a recent employee appreciation night at a Royals game to show some of the faces of the real people that are working every day to protect organizations around the country from cyberattacks. This includes people from our engineering, legal, account, HR, and Marketing teams. See? It takes all kinds in the cybersecurity industry. Interested in joining us? Check out our Careers page.
Lastly, we put together a blog post to highlight many of our careers initiatives, from the grade school level, all the way to the seasoned professional, to shed more light on how anyone can get involved in the field. Learn more here.
Week 4 – Cybersecurity First
Finally, we touched on our final weekly theme, “Cybersecurity First”. On average, companies take about 197 days to identify and 69 days to contain a breach. The idea of “Cybersecurity First” is to help guide people to put more priority on cybersecurity practices continue to lower the chance for hard to detect breaches to take place. This proactive approach to cybersecurity will continue to be important as the modern business landscape continues to develop.
We again sat down with CYDERES Chief Technology Officer Tim MalcomVetter to get his thoughts on what a “Cybersecurity First” approach looks like.
#AskFishtech
To wrap Cybersecurity Awareness Month up, we brought in experts from all across Fishtech Group to answer all of the questions we received throughout the month to help bring like to the thoughts and concerns from across our community. Here is a link to check out this wonderful discussion.
Thanks for joining us for a recap of this amazing month. We hope you learned a lot, and found some practical ways you can #BeCyberSmart in the year to come. Join us again next year, same time same place.
In the meantime, if you have any further questions on cybersecurity for us, fill out the form below to be connected with one of our experts. See you next year!
Explore. Experience. Share. - Cybersecurity Careers Awareness Week
October 22, 2021Cybersecurity Insights
All throughout the month of October, we have been participating in Cybersecurity Awareness Month to help guide organizations and individuals on how to #BeCyberSmart. For week three, we have shifted our focus to Cybersecurity Career Awareness to highlight the individuals that are eyes-on-glass every day as experienced InfoSec professionals, and to also put a spotlight on ways aspiring professionals can get into the field and thrive.
Even as cybersecurity concerns have increasingly dominated international news, the talent shortage in the cyber industry has only grown over the past year.
Studies show that there aren’t enough skilled tech force workers to fill the jobs available now, much less to meet the increasing demand of the years to come. In fact, (ISC)2 estimates the cyber workforce needs to increase by 62% to meet demand as businesses invest in technology and cyber threats become more sophisticated. The Bureau of Labor Statistics reports that the industry will experience job growth of 31% between 2019 and 2029.
At Fishtech Group, we have prided ourselves on our focus on cybersecurity career development, from providing challenging hands-on opportunities for seasoned cyber career men and women, all the way to hosting mentorship events for area schools to help the next generation find their footing in this growing industry.
Below you will find a mix of resources all surrounding our ongoing commitment to advancing cyber careers. Browse through and be sure to reach out if you have any questions.
#AskFishtech Panel Discusses Cybersecurity Careers
We are gradually building our way to the next installment of our #AskFishtech webcast series at the end of the month, and we’re excited to tackle more great questions after the robust and interesting conversations that were sparked last time around. In fact, here’s a clip from last year’s #AskFishtech webcast with a couple members of our executive team chiming in on cybersecurity careers.
Hear from our own Chuck Crawford, Chief Customer Officer, and Kerry Kilker, Chief Operating Officer, as they talk about their experiences in the field, and discuss ways individuals can get started in cybersecurity.
Fishtech’s Commitment to Engaging Young Learners
Fishtech Group is committed to getting young people interested in cybersecurity. Raising awareness and interest is good for both our company’s mission and the industry overall. We’ve been at it so long that we’ve even hired one of our visiting students after he graduated recently!
And our efforts are being noticed. We were thrilled last month to receive a Corporate Hero Award from the Kansas City Central Exchange for our ongoing efforts to bridge the gender gap in cybersecurity.

Inspiring Tours of Fishtech Campus
After a quiet 18 months, we are happy to once again host students and teachers through our headquarters and Cyber Defense Center. We hold Q&A panels featuring our analysts and developers for the school groups. During Covid, we truly missed the interaction and opportunity to inspire — and be inspired by — these visits.

Each tour includes brief interviews with Fishtech Group employees, all from different parts of our organization. Employees each describe the work they do day-to-day, how their career path led them to Fishtech, and what training and education helped them be successful today. Often they will tell our student visitors that certifications and specialized training are great, but what truly makes a candidate stand out are so-called soft skills that our industry values, such as:
- Passion and how to apply it to real-world problems
- Curiosity and how to pursue lifelong learning
- Creativity and collaboration
- Ability to troubleshoot
Our recent community engagement includes a diversity of initiatives such as:
- Hosted 70 adults and teens interested in a cybersecurity career with a Community Expert Panel
- Toured 20 high school students who aren’t necessarily interested in cybersecurity but are on alternative learning paths
- Counseled seven college students about next steps in their collegiate and cybersecurity career
- Explored cybersecurity career choices with a group of math teachers seeking knowledge to mentor their students
- Helped choose recipients for First Robotics grants to area schools
- Kicked off KC STEM Alliance’s Remake Learning Days with an eye toward cybersecurity
We’re Hiring!
There are so many different roles that make up the broader cybersecurity industry, and chances are… We’re hiring for most of them. So, what are those roles exactly? We have been asking many members of our leadership team to highlight roles they are looking for so we can get to work recruiting the best of the biz.
Whether you’re actively looking for a new job opportunity, or you are new to the industry and want to learn about what some of the roles in cybersecurity actually are, check out a couple of the below videos to get insight into how these positions fit into our organization.
For more information on our career initiatives, fill out the form below to be connected with a member of our team.
Talking Insider Threat Detection & Response with Kirk Cerny, Senior Director of Insider Threat - CYDERES
October 14, 2021Cybersecurity Insights
Insider threats pose a complex challenge for most organizations.
Information security and IT departments are constrained by conventional network detection systems that don’t account for the distinctly human motivations behind such threats. Meanwhile, HR, legal and physical security teams lack the means to derive useful intelligence from cyber indicators. The result is that risky insiders often go undetected until after an adverse event occurs. That’s why we created our CYDERES Insider Threat Detection & Response solution, or ITDR, to address these common challenges.
In order to illuminate more about this game-changing solution, we talked to Kirk Cerny, Senior Director of Insider Threat at CYDERES to get the lowdown on ITDR, and a broader look at insider threats.
Intro to Insider Threat Detection & Response
CYDERES Insider Threat Detection & Response, or ITDR is a first-of-its-kind solution to help organizations combat the growing number of insider activities that are affecting organizations in adverse ways. ITDR seamlessly combines technical and human behavioral indicators within a single analytics platform, providing a unique blend of cybersecurity firepower and AI-driven behavioral analytics that enable SOC teams and their HR and legal counterparts to proactively mitigate their highest-priority threats.
Starting Your Own Insider Threat Detection Program
Don’t know where to begin with starting your own insider threat detection program? Kirk breaks down a good entry point and highlights how CYDERES can help get your insider threat detection program off the ground.
The Technical & Non-Technical Indicators of Insider Threat
Many insider threat programs focus only on technical indicators, but insider threat is not just a network problem, but a human problem. ITDR focuses on both technical and non-technical indicators to provide a more well-rounded and effective insider threat solution.
What Does a Whole-Person Approach to Insider Threat Look Like?
Kirk dives deeper into how non-technical indicators factor in to our “whole-person approach” to insider threat.
The Present State of Insider Threat
Insider threats are on the rise, and 2021 has been a year where many are either starting or bolstering their insider threat programs, as Kirk explains.
The Importance of Insider Threat Deterrence
Insider threat programs need to be much more than just responding to malicious activity. It is also important to put an emphasis on deterrence to reduce the likelihood that an adverse event will occur.
24/7 Insider Threat Mitigation
Staying on top of insider threats effectively can be a daunting task. With CYDERES, you have a team that is ready to assist 24/7.
Insider Threat Detection & Response
Ready to do address the human factor of cybersecurity? The CYDERES Insider Threat Detection & Response solution is built to provide you with a frictionless way to tackle the issue of insider threat within your organization.
To learn more about ITDR and insider threats, fill out the form below to be connected with one of our experts.
Cybersecurity Awareness Month 2021 – Quick Refresh Guide
October 7, 2021Cybersecurity Insights
Cybersecurity Awareness Month was launched by the National Cyber Security Alliance & the U.S. Department of Homeland Security in October 2004 and has been a continued focus in InfoSec communities each October since. On this first full week of October, we’re turning our focus toward spreading cybersecurity awareness to help members of our community and the organizations we serve do their part to #BeCyberSmart.
Each year, Cybersecurity Awareness Month is a call to action for individuals to own their role in protecting their part of cyberspace. At Fishtech Group, our mission is to lead organizations to a more secure future, but that security isn’t achieved by some vague corporate check box, but rather an every day, ongoing commitment from each and every one of us.
We each have a role to play in making sure we follow best practices to protect our devices and data to ensure the broader security of the individuals in our organizations.
We will be putting out new content every week for all of this year’s Cybersecurity Awareness Month themes. To start off this critical month, we wanted to highlight some quick tips in a “Cybersecurity Basics: Quick Refresh Guide” that will help to inform you about some basic areas of cybersecurity and lay the groundwork for your better overall awareness and understanding on the intricacies of cybersecurity and how you can #BeCyberSmart.
—
Cybersecurity Basics: Quick Refresh Guide
Ask any cybersecurity professional what the biggest threat is to a company, and most of them will say their employees, even if the threat isn’t intentional. Basic human error is a major contributing factor to 95% of security breaches (The Hacker News). Can you remember the last time you reviewed the login information for your personal and professional accounts or checked the security of your network connection? A few small changes just might save you from an account compromise.
Ready to implement a few upgrades to protect your information and access? Here’s your handy checklist of basic security features to add to or refresh your personal and professional accounts:
- Create strong passwords.
- Ensure that your passwords contain upper and lowercase characters, symbols, and numbers. A random combination of these will make guessing your password and hacking into your personal accounts more difficult.
- Use at least two-factor authentication
- Add an extra layer of protection to your login process by implementing one extra step. Instead of only submitting your login credentials to gain access to your account, set up a second method by confirming your access on a second device. For example, have a confirmation code send to your phone or email.
- Keep your software up to date
- Ensure your operating system, applications and web browsers stay up to date by setting your updates to happen automatically. Many updates include security features, so it’s a good idea to stay on top of them!
- Backup your files
- Be sure you have your important files backed up on an external drive or in the cloud. This way, if something unfortunate happens and you lose information on your device, you have it saved in another place.
- Be careful with public Wifi and Hotspots
- Public wifi and hotspots are not secure internet connectors, so it’s easy to see the activity of others connected to the network. We recommend using a VPN and personal hotspot to access the internet instead.
We hope this handy checklist serves as a quick reminder of the basic, but necessary security practices. If you already have these in place, and we’re certain that most of you do, then a quick refresh won’t hurt. If you don’t, today is the perfect day to start!
Are you an organization looking to ramp up the basic security features you have in place? Our experts at Fishtech Group are standing by to help. Drop us a note below and our team will be in touch.
In the meantime, stay tuned through the rest of October as we continue empowering you to #BeCyberSmart this Cybersecurity Awareness Month. We’ll be back next week for a focus on phishing with ways you can better understand and fight back against these kinds of attacks.
Any questions? Fill out the form below to be connected with one of our experts.
CYDERES Insider Threat Profiles: The IP Thief
October 6, 2021Cybersecurity Insights
What motivates an individual to steal intellectual property from an organization? What types of employees are most likely to commit IP theft? How do they pull it off? And, most importantly, can they be detected and stopped by the security team before something bad happens?
CYDERES, the security-as-a-service division of Fishtech Group, thinks the answer to the last question is yes. But to succeed, the security team must first have a detailed understanding of the Who-What-When-Why-How of IP theft.
An excellent resource for understanding insider threats in all their various forms was published nearly decade ago, when researchers at Carnegie Mellon University’s Computer Emergency Response Team (CERT) Coordination Center published The CERT Guide to Insider Threats: How to Prevent, Detect, and Respond to Information Technology Crimes (Theft, Sabotage, Fraud).
The CERT authors delved deeply into the actions, attitudes and intentions of different kinds of insiders and came up with useful insights that have admirably stood the test of time. Along with the contributions of other experts in the field, these insights have influenced the design of our insider threat mitigation solutions and services.
Below is a summary of CERT’s profile of an IP thief.
- Who: Insiders who steal IP are usually current employees who are scientists, engineers, software programmers and sales personnel. The widespread perception that system administrators are among the biggest culprits, CERT found, is not supported by the research results.
- What: These individuals steal information they worked on directly, such as proprietary software and source code; business plans, proposals and strategic plans; customer information; and product information such as designs, formular and schematics.
- When: CERT found that most insiders stole at least some information within 30 days of resignation. That time frame actually encompasses a 60-day window: 30 days before leaving and 30 days after having left.
- Why: The reasons behind stealing IP can vary widely. One-third of IP thieves are looking to start their own business. Another 40% are starting a new job at a competing business. Most of the remainder represent instances of foreign governments or organizations compromising or enticing insiders to gain access to technologically- or commercially-valuable IP. Interestingly, according to CERT, very few insiders steal intellectual property in order to sell it. Rather, they seek business advantage.
- How: Exfiltration of intellectual property follows one of several tried-and-true pathways, including email, USB drives and removal of physical documents.
For companies worried they may have an IP theft problem but hesitant to launch their own insider threat program, CYDERES provides a range of capabilities through our first of its kind Insider Threat Detection & Response (ITDR) managed service.
ITDR analyzes an organization’s existing trove of user and network telemetry to find clues that an employee is behaving in a potentially adverse manner. It then uses operationally proven AI-based modeling techniques to filter out the excess noise from the data to identify the riskiest players, including IP thieves.
Buried in that telemetry is a wealth of intelligence on the insider’s circumstances and actions, which are an ideal proxy for gauging intent. The probabilistic model underlying our ITDR analytics turns each data point into a model concept and then builds a Bayesian inference network (image below) that captures the relationships between each concept as well as the relative strengths (low/medium/high) and polarities (true/false) between them.
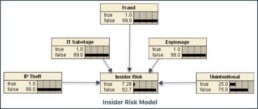
In simple terms, ITDR applies diverse data sources to the model. The data contains indicators of impactful personal or professional events plus a record of day-to-day actions – such as accessing the web or sending an email – and uses the results to assess and prioritize risk from an individual.
There are separate model indicators for behavioral characteristics, network and device activity and more. For the risk modeling component addressing use cases for ‘IP Theft,’ the strong indications relate to financial stress or impending threats to continued employment.
Medium-strength indicators can range from unwillingness to comply with established rules and procedures to anti-malware alerts. Low-strength indicators include an active social media presence or database content changes.
Our CYDERES Cloud Native Analytics Platform (CNAP) ingests the model results and a CYDERES analyst validates and triages them, delivering the results to organizations in the form of detailed incident alerts and the related evidence needed to launch an investigation, comply with legal and audit requirements associated with such activity and enhance future risk mitigation via policy and control changes.
Because it is a managed service, ITDR can be implemented far more quickly than conventional insider threat mitigation solutions, meaning organizations can start mitigating risk via their employees and contractors much sooner.
The Commission on the Theft of American Intellectual Property estimates that annual costs from the loss of IP range from $225 billion to $600 billion. And the 2021 edition of Verizon’s widely respected Data Breach Investigations Report (DBIR) says that around 22% of such incidents are attributable to an assist from or the unilateral act of a trusted insider.
Industry sectors most often targeted, according to a separate CERT blog post, are information technology (35 percent of cases), banking and finance (13 percent) and chemicals (12 percent). But few sectors have escaped the attention of IP thieves.
Given those stakes, mitigating even one act of IP theft could pay huge dividends to an organization, not just financially but also legally, operationally and reputationally.
# # #
Note: Future posts in this series will examine other types of insider threat actors, such as The Fraudster and The Saboteur. To learn more about how ITDR can help your organization rapidly deploy an insider threat capability, download our fact sheet here.
2021 Insider Threat Lessons Learned
September 30, 2021Cybersecurity Insights
National Insider Threat Awareness Month, which wraps up today, has given the cybersecurity community an opportunity to reflect on how the threat landscape has evolved in the past 12 months – and what lessons about detection, deterrence and mitigation can be learned from those changes.
As we did a year ago, let’s examine three of the key lessons.
Lesson #1: Threats Are Quickly Evolving
Disregarding the nearly 50 percent of insider events that can be ascribed to negligent and careless insiders, there are still plenty of malicious actors out there preparing the next insider attack. And they’ve been coming up with novel ways to succeed. Why bother hacking your way into an organization when, for example, you can simply bribe an insider to do it for you? That’s what recent reports say ransomware gangs have been attempting, offering a generous share of ransom payments to the insider who ‘unlocks the back door.’ Most organizations are not yet equipped to detect this and other emerging cyber-attack vectors.
Lesson #2: Vulnerabilities Have Increased
After Covid-19 arrived in early 2020, remote work took firm hold – especially among knowledge workers across a wide swath of industry sectors. With it came a dizzying array of new cybersecurity attack vectors. Along with the more plentiful ‘conventional’ external threat actors, insiders now have better odds of breaching network defenses and stealing intellectual property and sensitive data from the privacy of their own homes. Meanwhile, security teams are scrambling to secure new devices and monitor workers outside the traditional perimeter. Their latest unenviable risk management challenge: the double whammy of a rapidly evolving threat (see Lesson #1) and drastically increased vulnerabilities.
Lesson #3: Don’t Wait to Launch Your Program
Launching an insider threat mitigation program can be a long and complex affair. Detection systems must be selected and deployed, data sources must be connected and staff and management need training in governance and operations. The required commitment in dollars and labor hours before concrete results are obtained can discourage all but the most committed leaders from green-lighting such a program. That said, incidents involving insider threats increased by 47 percent between 2018 and 2020, and no is one predicting the pace will slow. Considering that statistic, coupled with the high cost of cleaning up the mess left behind by an insider attack, the best time to launch an insider threat program was yesterday.
Fortunately, CYDERES Insider Threat Managed Detection & Response managed service is empowering organizations to launch or mature their Insider Threat program very quickly, delivering immediate visibility and results. Learn more in our latest video:
Talking CYDERES Engineering with Cassandra Varvel, CYDERES Director of Engineering
September 16, 2021Cybersecurity Insights
Our Teams are Building a More Secure Future.
We have been incredibly excited by the launch of the CYDERES Cloud Native Analytics Platform (CNAP) 2.0 as we continue to bolster the already amazing capabilities of our strategic partner Google Cloud, and their Chronicle offering.
With Google Cloud’s recent announcements around Autonomic Security, the path to modernizing your security programs is clearer than ever. On their recent earnings call, Alphabet and Google CEO Sundar Pichai recently highlighted GC’s security offerings (incl. Chronicle) as their “strongest product portfolio” empowering their incredible growth.
CYDERES is proud to be one of Google Cloud Chronicle’s founding partners and preferred MSSP partners to deliver this solution.
With all of the excitement building around CNAP 2.0, we wanted to illuminate a bit more of the team that is working behind the scenes to develop these game-changing offerings. We recently sat down with Cassandra Varvel, CYDERES Director of Engineering, to talk about CNAP 2.0, the various parts of the Engineering organization, how we integrate with Google Cloud and Chronicle, and more.
CYDERES Engineering Team
Our CYDERES organization is built of many moving parts. Cassandra illuminates one of the pivotal pieces of the broader CYDERES organization: the Engineering Team. Learn about the various positions within the team, and what impresses Cassandra the most about this talented group.
CNAP 2.0 Benefits
CYDERES Recently launched CNAP 2.0, improving on the CYDERES Cloud Native Analytics Platform that has already provided so much value for our customers. Cassandra talks about some of the new benefits you can expect with this exciting launch.
How Does CNAP Utilize BigQuery?
CYDERES has been in close partnership with Google Cloud, and their Chronicle platform, to help bolster their already incredible threat hunting capabilities, and to provide one of the best answers to the issues of legacy SIEM. Learn more about how CNAP utilizes Google BigQuery and what we bring to the table to help make detecting threats easier than ever.
How is CYDERES Different From a Traditional MSSP
We pride ourselves in being different from traditional MSSP offerings. Cassandra talks about some of the reasons as to why we are a better alternative for those looking to move away from legacy managed security offerings.
The Power of TEAM
It’s important to build great teams that can trust each other and work well in collaborative environments, and we think our Engineering Team is one of the best in the business. Cassandra talks about some of the best aspects of the teams we have been building at Fishtech and CYDERES.
Work on Critical Client Solutions at CYDERES
It can be a daunting task to work in a cybersecurity company, but these challenges can be very rewarding as well. Cassandra talks about the excitement she feels when working on critical client solutions.
Join Our Growing CYDERES Team
Interested in joining our CYDERES team? Hear about some of the positions we’re looking to fill, and be sure to check out our Careers page apply for one of our amazing opportunities!
If you are ready to discuss CNAP, CYDERES Engineering, or any of our other offerings, fill out the form below to be connected with one of our experts.
Insider Threats Are Evolving - Fast
September 9, 2021Cybersecurity Insights
Ransomware gangs continue to find creative new ways of exploiting weaknesses in corporate networks. Now they’ve added a dangerous twist that is sure to make the insider threat problem noticeably worse.
In this latest move, gangs like LockBit are actively recruiting corporate insiders to help them breach and encrypt networks in return for what can amount to million-dollar payouts.
According to a recent article in BleepingComputer, ransomware gangs have traditionally consisted of a core group of developers, who maintain the ransomware and payment sites, and recruited affiliates who breach victims’ networks and encrypt devices, with the affiliate usually receiving 70 to 80 percent of the ransom paid. But LockBit and its counterparts are now “trying to remove the middle-man” by messaging trusted insiders directly rather than using affiliates. The article’s author speculates that while it may seem “counterintuitive to recruit an insider for a network [that’s] already been breached… this message is likely targeting external IT consultants who may see the message while responding to an attack.”
Separately, Brian Krebs of Krebs on Security reports on one gang that offers insiders payouts of 40 percent of the ransom payment. The gangs “seem to have done away with the affiliate model in favor of just buying illicit access to corporate networks,” he adds.
This latest recruitment drive does two things: 1) It increases the pool of likely threats by turning otherwise hesitant insiders into enthusiastic ones; and 2) It significantly heightens the risk that an organization will suffer a major (as opposed to minor) data breach, since the recruits will be seeking the largest possible payout for the unique risk they are taking.
Insider recruitment for pay is the latest in a growing list of use cases for which Fishtech Group business unit CYDERES has designed its new Insider Threat Detection and Response (ITDR) managed service (pictured below).
ITDR, which uses models and other AI-based analytics to process user and network telemetry for early indications of insider intent, is optimized for three specific use cases:
- Data Exfiltration/Sabotage: Detection of excessive file deletions or movements, unusual e-mail activities and consumer web application uploads is critical to preventing the exfiltration or sabotage of data – one of the more prevalent insider threat events. ITDR detects unauthorized or suspicious data access and activity and makes key correlations on file actions and transfers, focusing on ‘crown-jewel’ data in the cloud, apps, databases, file-shares and disks.
- Departing Employees: Individuals who plan to leave the organization or learn they are about to be off-boarded pose a substantial risk to corporate systems and data. ITDR focuses on detecting network and application access patterns that indicate job searches, outreach to competitors and data exfil intent. Response capabilities include proactive alerts on these activities plus changes in behavior and productivity, and forensic reports for use during post-termination reviews.
- Account Compromise: With the right tools, it’s possible to pinpoint behaviors that indicate a potential takeover of credentials by third-party actors via negligent or malicious insiders, at speed and at scale. By detecting unusual login volumes, logins from high-risk locations, or geographically/ temporally impossible login sequences, ITDR excels at alerting investigative teams to instances of potential account compromise – before a data exfil attempt happens.
One could argue that by offering trusted insiders a piece of the action, the LockBits of the world are touching on all three of those use cases.
Whatever the event type, it’s been clear for some time that the insider threat landscape is evolving rapidly. Organizations will need to evolve with it. And even as they address their adversaries’ current innovations, they also should count on even more insidious exploits in the future.
# # #
Note: Tune in to our recent ITDR introductory webinar to learn more about the powerful capabilities this managed service can deliver to your organization. Or simply reach out here to schedule a live ITDR demo.












