
Executive Summary
“Flattening the curve” refers to efforts to implement community isolation and personal hygiene measures that help keep COVID-19 cases at a manageable level for medical practitioners. In the digital world, you can flatten the curve of COVID-19 phishing incidents by staying vigilant and practicing good email security hygiene. Attackers have adapted to this pandemic by using COVID-19 lures to deliver malware and direct victims to phishing sites, taking advantage of the current global situation and how humans react during stressful times.
The purpose of this blog is to keep you informed on the current phishing emails being delivered to your inbox. Staying updated on trends in the usage of COVID-19 and other lure themes will help your organization stay protected.
COVID-19 Phishing and Malware distribution
Attackers have long taken advantage of public anxiety surrounding global and regional crises and the current pandemic is no exception. During the 1st quarter of 2020, we have observed a significant number of phishing emails leveraging COVID-19 themes. These emails have included attachments or URLs commonly leading to phishing sites or malware such as Lokibot, NanoCore, and other Remote Administration Tools (RATs). Some recently observed email subjects include the following:
- You missed a call Corona Update
- CDC HEALTH emergency coronavirus COVID-19 Pandemic
- COVID Report
- COVID-19 Payroll Adjustment
- Security Update Stimulus Check Failed
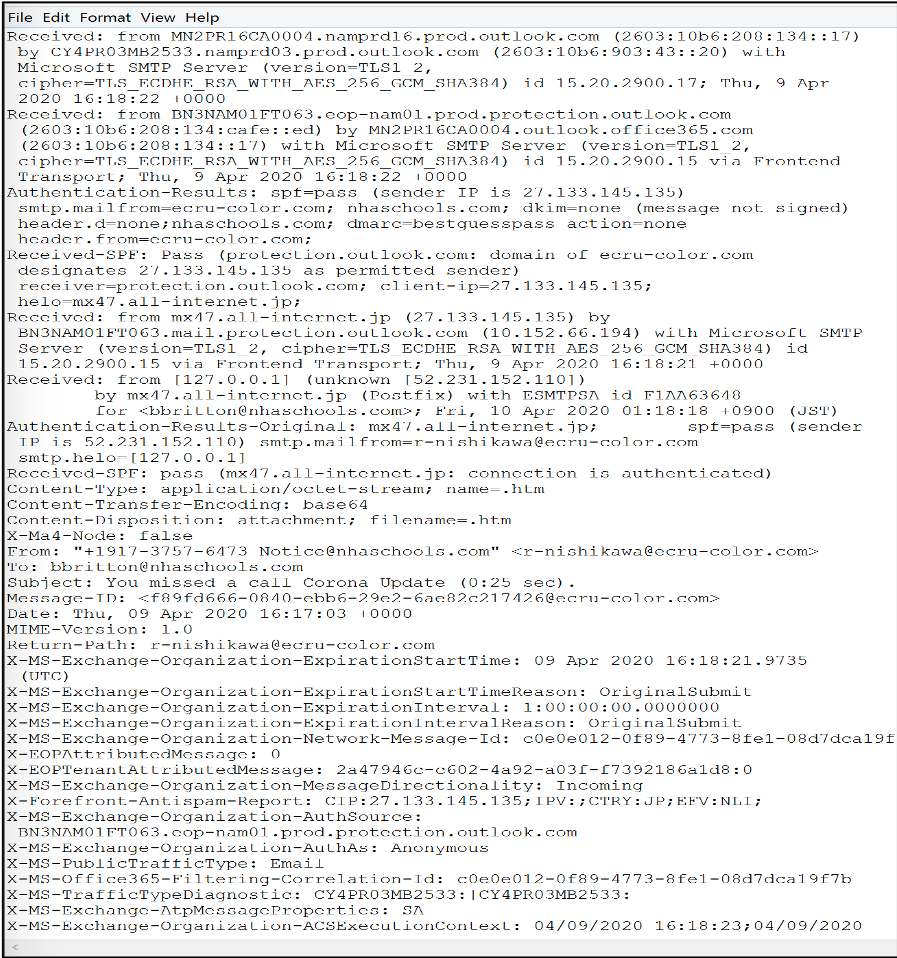
Conducting analysis on an example phishing email resulted in some interesting findings. The following screenshot shows the email subject and attachment but no content. The “From:” section shows “+1917-3757-6473 Notice@nhaschools.com”. “Nhaschools[.]com” is the site for a US National Heritage Academy charter school. At first glance a victim with children attending this school might open the attachment if they see the school’s name and the phrase “Corona update” on the subject line. Other victims might open the attachment to read any information related to the current pandemic.

Looking at the headers, specifically the sender “IP” and “Return path”, we see the following information:
Sender IP: 52.231.152.110
Return-Path: r-nishikawa@ecru-color.com
“You missed a call Corona Update” Email headers
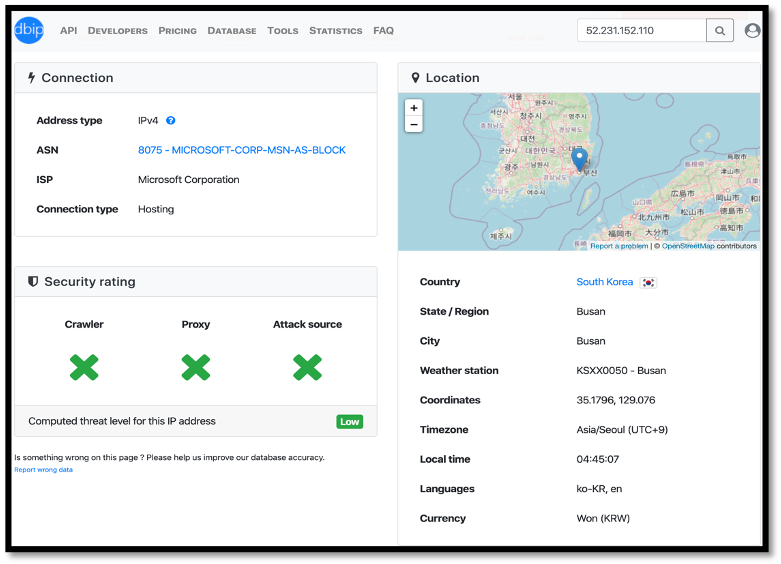
The sender IP can be traced back to South Korea and ecru-color.com appears to be a Japanese styling salon school.
Sender IP Geo Location
Domain from the Return path address
Returning to the email and opening the attachment in a virtual machine, shows the attachment opening a .html document from the email which pretends to be an online web page. These types of phishing emails play a vague voicemail message before the victim is redirected to a phishing page. Performing a right click and selecting view source, shows us the script being used.
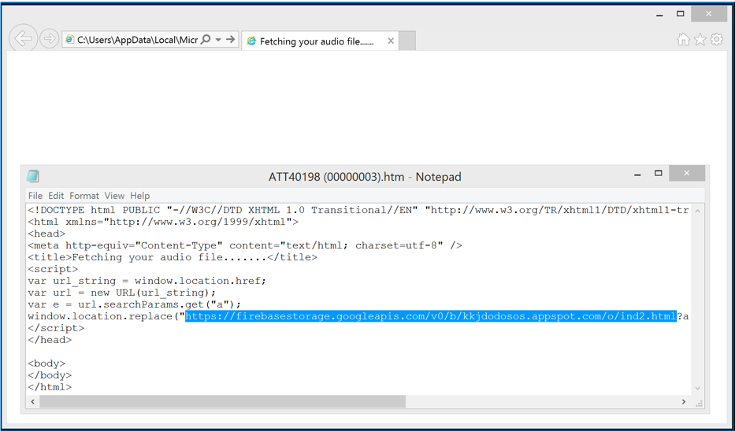
Performing a quick google search shows it’s been scanned by the site urlscan.io, 10 times. As we can see, it is an Outlook Web App phishing page which was still active at the time of this writing.
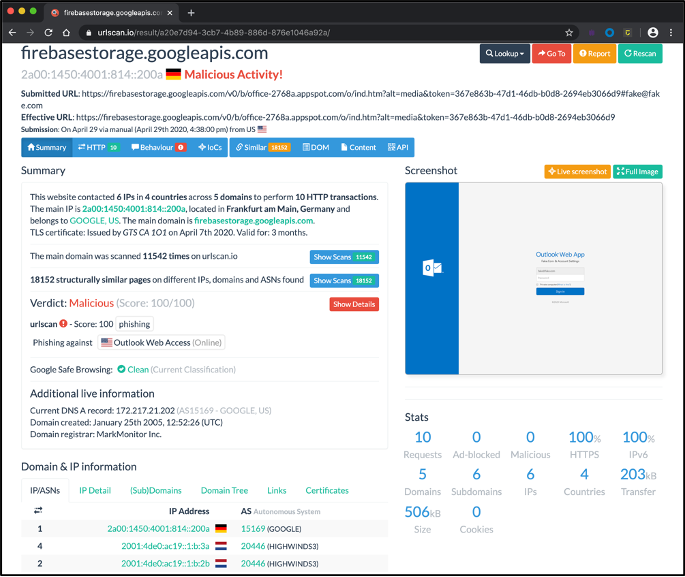
Attackers leverage free, compromised, and dedicated infrastructure to host COVID-19-themed phishing content.
Some examples of recently observed URLs include the following:
- hXXps://cnncoronavirus[.]000webhostapp[.]com/
- hXXps://c0vid19-aid-ca[.]org/
- hXXps://cecollc[.]com/infrastructure/covid/FBG/
- hXXp://coronana[.]000webhostapp[.]com/
- hXXp://gift-covid19[.]000webhostapp[.]com/
How you can stay safe:
While email spam using COVID-19 themes are a relatively new and increasingly prevalent phenomenon, these lures ultimately leverage common social engineering tactics capitalizing on sentiments of fear, anxiety, and curiosity. Once this theme runs its course and dwindles in popularity, it will undoubtedly be replaced by a mix of themes related to current events and common phishing themes like financial transaction, parcel delivery, and file sharing. The positive news is that users can protect themselves from these tactics by improving their awareness and practicing basic security hygiene.
Technology can help to protect users from many of the attacks that attempt to reach inboxes; however, education is the best defense against the phishing attacks that inevitably make it past these defenses. Staying up to date on phishing lure themes that are currently being used and learning how to spot a phishing email will help you flatten the curve.
When reading your emails, ask yourself the following questions:
- Does this email contain a personalized greeting?
If not, it’s likely unsolicited and may be a phishing email, so proceed with caution.
- Is this email attempting to instill fear or a sense of urgency to convince me to act?
If yes, it may a phishing email, so proceed with caution.
- Are there basic grammatical or spelling errors in this email?
If yes, it may a phishing email, so proceed with caution.
- When hovering over links, do I see any signs that they may be malicious?
If you cannot identify the link as a trusted resource, it may be a phishing email, so proceed with caution.
- Do I recognize the sender and was I expecting an email from them?
If not, it may be a phishing email, so proceed with caution.
- Are any brand names being used in the email?
Attackers often use logos to create convincing phishing email, so proceed with caution.
We can help your organization flatten the curve
What is better than technology and education? A combination of human-led and machine-driven security as a service. CYDERES’ 24/7 security as a service gives you the people, process, and technology to help organizations manage cybersecurity risks, detect threats, and respond to security incidents in real time. Take a look below at some of the benefits of having a team of security professionals detecting and mitigating your organization’s threats. For more information, visit our site and download the full services factsheet at: https://fishtech.group/solutions/security/
- Managed 24x7x365 Security Operations Center (Tiers 1-4)
- Threat detection and triage for all technologies
- Security incident response
- Proactive threat hunting
- Build playbooks (phishing, malware, lateral movement)
- Endpoint detection & response management
- Sole EMDR 100% powered by Chronicle Backstory
- Backstory forwarder 24×7 management and monitoring
- Custom Backstory integrations/parsers
