Executive Summary
CYDERES, Cyber Defense and Response, is the security as a service division of Fishtech. This division was created to help organizations with 24/7 security operations through our award-winning managed detection and response offering. This article focuses on the day to day activities of a SOC Analyst.
Thursday Morning
Through the Missouri Innovation Campus I was provided with an opportunity to learn with a position as an intern in the CYDERES SOC. With the help of analysts and other CYDERES resources, I was able to recently apply some of the knowledge I have learned to a recent Bazar loader campaign. On September 24, 2020 I started off my day by grabbing a nitro cold brew from the break room before heading though the man trap that leads into the Security Operations Center. Using face recognition for the first door and my badge for the next, I headed to my desk. Once there, I looked at the Twitter feeds which are kept on the large display and noticed reports regarding a malspam campaign being linked to Bazarloader. Since I was working the abusebox, which is a service offered to clients in which suspicious emails are sent for analysis, I started to research on what the campaign looked like and noting any similarities to previously seen campaigns.
Figure 1: SOC in the Cyber Defense Center
Thursday Afternoon
Later that day, CYDERES received multiple copies of emails being delivered to different customers with a close resemblance to the emails seen that morning. The first item that stands out is they all had the same two subjects, “Re: what time?” and “Re: debit confirmation”. The second item that stood out was that they all had the same sending email address, “mike_warner@parkshorebmw[.]com”, which appears to be a legitimate email for a BMW dealership in Vancouver that was likely compromised or spoofed. While the sender looked reputable, investigating the body of the email showed similar items to previously seen phishing campaigns that lead to credential harvesters.
Figure 2: Sample email 1
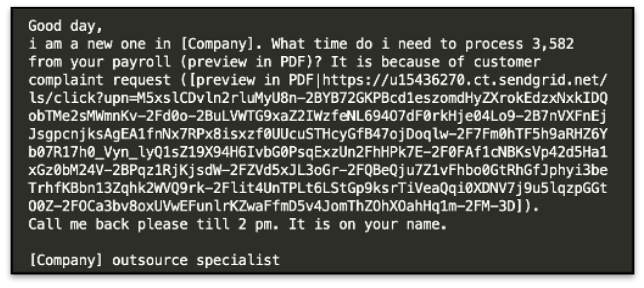
Figure 3: Sample email 2
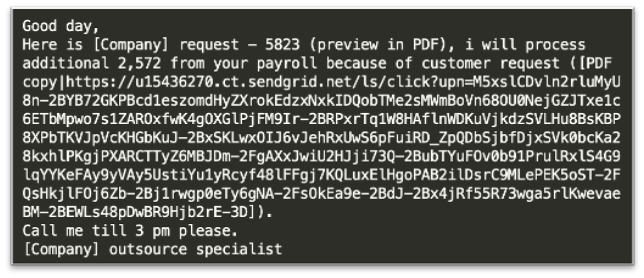
I observed that the emails contained common spear-phishing (Mitre T1566.002) techniques which address the email to the target company, while claiming to be an outsource specialist. The email also contained a sense of urgency by discussing payroll information and setting a time where a reply is needed, then requesting the user download a PDF file.
The link in the email shows it was sent via Sendgrid and contains a masked URL that will redirect to the payload. This follows the trend reported by Brian Krebs on how Sendgrid is commonly used to send out malicious emails to evade detection. The link in the email leads to a Google Document which looks very similar to ones that have been linked to Emotet malspam campaigns.
Figure 4: Screenshot of the requested download pdf
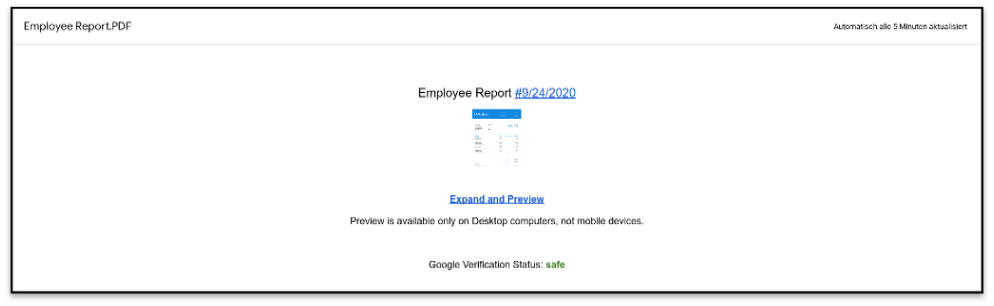 The page contains a message that claims that Google has verified this page and calls it “safe”. However, this is added by the threat actors in an attempt to make the page look legitimate. The page is hosted via Google’s cloud services which means that this document could have been created by anyone, so it should not be trusted for employee information.
The page contains a message that claims that Google has verified this page and calls it “safe”. However, this is added by the threat actors in an attempt to make the page look legitimate. The page is hosted via Google’s cloud services which means that this document could have been created by anyone, so it should not be trusted for employee information.
The link on the page was observed to download an EXE file even though the email and the website claim that the document should have been a PDF file.
Running the file command shows the following:
Figure 5: File command on suspicious “pdf” file
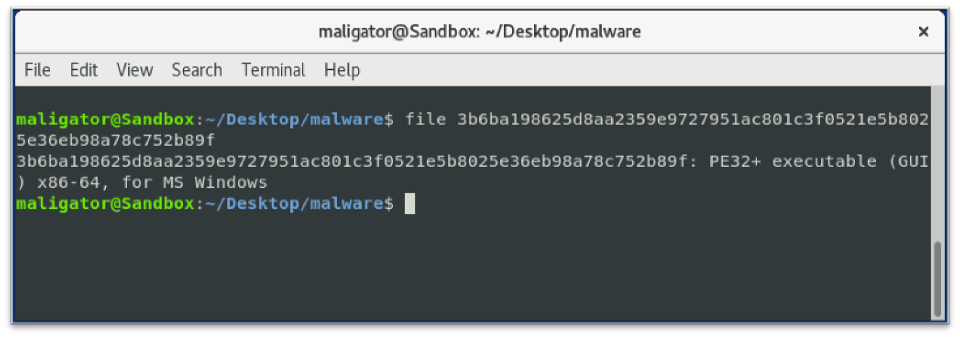 The downloaded binary had not yet been identified in Virustotal as malicious. The binary was then detonated in a sandbox environment but did not run in a Windows 10 32-bit environment. Switching to a Windows 10 64-bit sandbox, the sample loaded modules, but then after reading the GUID information it unloaded them. This appeared to be because the sample identified that it was in a VM or that it would not run on Windows 10. This is a common threat actor tactic used to try to avoid analysis which aligns with technique T1497 of the Mitre ATT&CK model.
The downloaded binary had not yet been identified in Virustotal as malicious. The binary was then detonated in a sandbox environment but did not run in a Windows 10 32-bit environment. Switching to a Windows 10 64-bit sandbox, the sample loaded modules, but then after reading the GUID information it unloaded them. This appeared to be because the sample identified that it was in a VM or that it would not run on Windows 10. This is a common threat actor tactic used to try to avoid analysis which aligns with technique T1497 of the Mitre ATT&CK model.
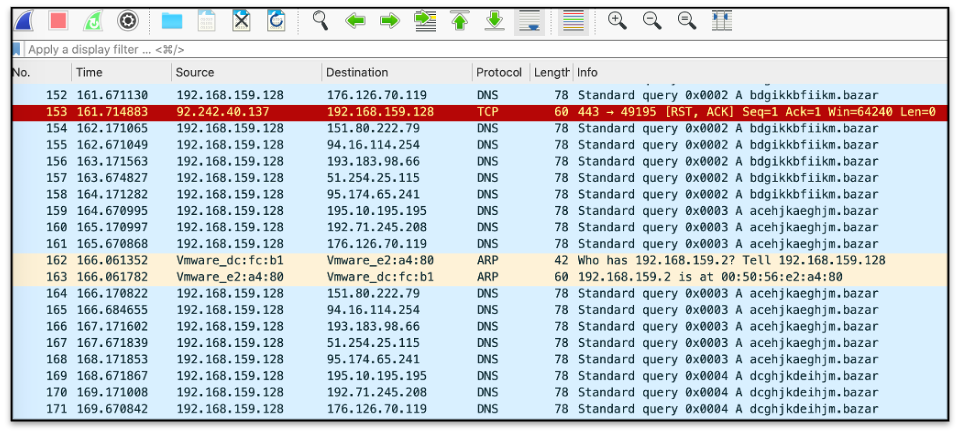
Research on the PDB path from the binary led to a github page with a theory that the binary might run on a Windows 7 VM. The referenced Github page talks in detail on how to escalate privileges in Windows 7. After detonating the sample in a local Windows 7 virtual machine, it was found that the sample was generating domains ending in “.bazar”. Similar to Trickbot, this loader evades detection by abusing the trust of certificate authorities. This loader, however, uses EmerDNS domains for command and control due to the domains being uncensorable. According to the emercoin site:
Because of Emercoin’s secure and distributed blockchain the domain name records are completely decentralized and uncensorable and cannot be altered, revoked or suspended by any authority. Only a record’s owner can modify or transfer it to another owner, and a record’s owner is determined by whoever controls the private key to the associated payment address.
Figure 6: Screencapture of bazar dns domains in Wireshark
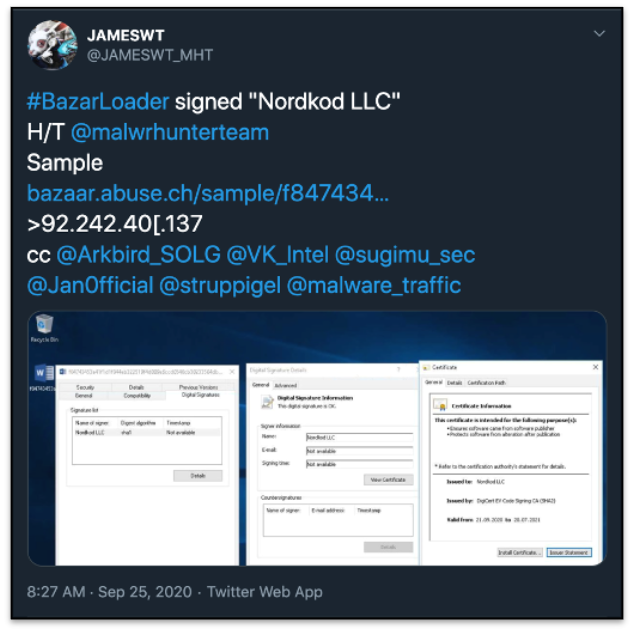
Performing OSINT review on the IP address, 92.242.40[.]137, resulted in a tweet by @JAMESWT_MHT listing this IP as “Bazarloader” signed by “Nordkod LLC”:
Figure 7: Tweet listing the ip as bazarloader
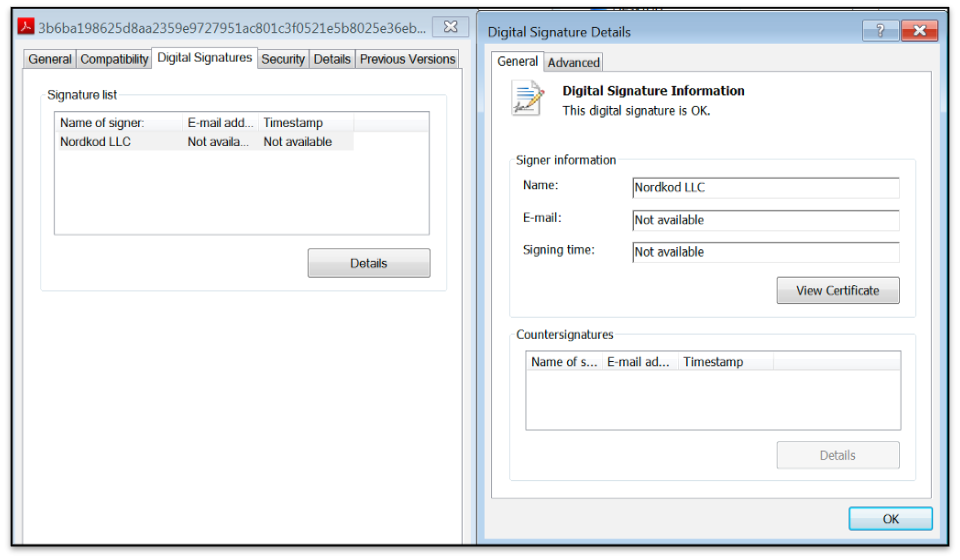
A look at the binary properties show the same signature listed on Twitter:
Figure 8: File signed as Nordkod LLC
The next steps were to follow customer specific playbooks to report and mitigate this campaign for our clients. For one customer, this included quarantining around 100 emails which had reached users but were mostly unread. Leveraging Chronicle, a search was made for any IOCs in the customer’s environment, which resulted in 0 hits. For a detailed analysis of Bazarloader, check out Cybereason’s article titled “A bazar of tricks: following team9’s development cycles”.
Leverage Fishtech’s Expertise
Analysts in the GSOC, Global Security Operations Center, provide 24×7 security monitoring, triage, and investigations across the entire security stack. From abuse box monitoring and human threat hunting to managed deception and network traffic analysis, CYDERES ultimately owns detection of threats in the client’s environment to be a force multiplier for in-house security capabilities. To learn more on GSOC or other services offered by Fishtech, fill out the form below, or check out the drop down menus at the top of the page.
References:
| https://krebsonsecurity.com/2020/08/sendgrid-under-siege-from-hacked-accounts/ |
| https://emercoin.com/en/documentation/blockchain-services/emerdns/emerdns-introduction |
| https://twitter.com/JAMESWT_MHT/status/1309469473833967616 |
| https://github.com/pauldotknopf/WindowsSDK7-Samples/blob/master/com/uac/elevationsample/ElevationManager.cpp |
| https://attack.mitre.org/techniques/T1497/ |
| https://www.cybereason.com/blog/a-bazar-of-tricks-following-team9s-development-cycles |
IOCs
| Phishing Urls: |
| hXXps://redacted[.]sendgrid[.]net/ls/click?upn=M5xslCDvln2rluMyU8n-2BYB72GKPBcd1eszomdHyZXrokEdzxNxkIDQobTMe2sMWmGk0T0fDgb82Scmnu0FhU33GfqxrVpZAf8fN |
| hXXps://docs[.]google[.]com/document/d/e/2PACX-1vSNRlZCfsXuh24McOcs7UlenV3L7e9W6BDiq48hHtm2odtzRVdXYWlU-t7Dryn_7ZqE4RVRuNFSlmqh/pub |
| Hash |
| sha256 3b6ba198625d8aa2359e9727951ac801c3f0521e5b8025e36eb98a78c752b89f |
| sha1 4e783aa0faa4a1a56d9e8b14c83b17f74bb8e31b |
| md5 62265048f49f6f22500f75ea45325603 |
| Bazar Loader’s DGA implementation (snippet) |
| acfhklaehhkn[.]bazar |
| bdehkkbfghkm[.]bazar |
| aegikmagiiko[.]bazar |
| bdfhilbfhhin[.]bazar |
| afggilahigin[.]bazar |
| ccegilceggin[.]bazar |
| bdfijlbfhijn[.]bazar |
| cdfhjlcfhhjn[.]bazar |
| dcghjkdeihjm[.]bazar |
| cdeijlcfgijn[.]bazar |
| dcfgikdehgim[.]bazar |
| cdegjlcfggjn[.]bazar |
| bdfiikbfhiim[.]bazar |
| ceegilcgggin[.]bazar |
| bcehjlbeghjn[.]bazar |
| dfggikdhigim[.]bazar |
| dehijkdgjijm[.]bazar |
| cdehilcfghin[.]bazar |
| afgiilahiiin[.]bazar |
| bdggimbfigio[.]bazar |
| bceijlbegijn[.]bazar |
| IP Connections |
| 193.183.98.66 |
| 51.254.25.115 |
| 95.174.65.241 |
| 192.71.245.208 |
| 94.16.114.254 |
| 151.80.222.79 |
| 195.10.195.195 |
| 176.126.70.119 |
| 92.242.40.137 |