
Business leaders and IT professionals have become increasingly familiar with ransomware over the last several years. Time after time, we’re exposed to high-profile stories where brands and organizations we know and love are crippled by cyber criminals encrypting sensitive data and asking for money in exchange for the “safe” return of data. We don’t have to search long to understand why we’re continually plagued by ransomware.
In 2019 alone, the top 5 largest payouts to cyber criminals made by organization’s struck by ransomware totaled over 1.6 million dollars!
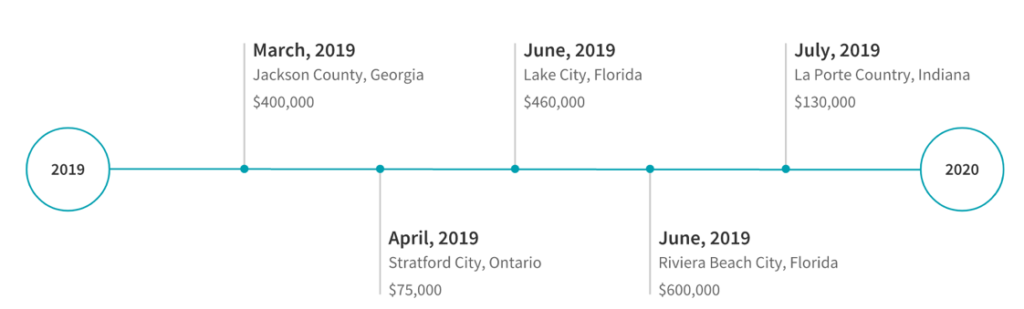
- Riviera Beach City, Florida – $600,000 [link]
- Lake City, Florida – $460,000 [link]
- Jackson County Georgia – $400,000 [link]
- La Porte County, Indiana – $130,000 [link]
- Stratford City, Ontario – $75,000 [link]
One of the biggest payouts ever made to malicious actors came from a South Korean hosting company called Nayana. During the 2017 Erebus malware outbreak, around 150 of Nayana’s Linux servers were infected causing more than 3,400 hundred hosted websites to go down. The company negotiated with the attackers, ultimately agreeing to pay 1 million dollars to release their data. [source]
There are several straightforward steps to take in helping to reduce the risk of becoming a victim; backing up and validating sensitive data, auditing and remediating accesses, and having an approved ransomware incident response plan are just a few. Undoubtedly, there are some organizations that have not begun implementing steps to reduce the impact of a ransomware event, while others recognize the risk to their business and have comprehensive systems in place to recover quickly from an attack.
|
“If you are looking for ransom I can tell you I don’t have money, but what I do have are a very particular set of skills. Skills I have acquired over a very long career. Skills that make me a nightmare for people like you. If you let my data go now that’ll be the end of it.”
|
With our best practices for recovering data loss in place, it would make sense to breathe easy and get a little extra sleep at night without worrying about losing that special project everyone has been working on, right? Not so fast…
Ever tenacious, money-hungry cybercriminals have begun a disturbing new trend aimed towards squeezing every cent out of their target, despite the organization having recovery capabilities.
Exfiltration is certainly nothing new, but some actors have started pulling this tactic out of their playbook and combining it with encrypting data to get extra leverage when demanding payment. It’s a simple scheme really, if you won’t pay to decrypt your data, then you’ll pay to prevent the data from being leaked publicly.
With the financial impact of losing data averted, organizations face additional challenges around data exfil like brand reputation, and regulatory compliance. After all, it’s one thing to lose access to your data and another to let the world know about that pending merger, research delay, ongoing litigation, or embarrassing personal matter. Some organizations may also have to contend with the possibility of regulatory fines related to the release of personal information, or financial filings. Incidents like this already have a media presence.
At the end of 2019, reports surfaced that Travelex was hit by the Sodinokibi ransomware after failing to patch their Pulse Secure VPN servers. Attackers stood to make a tremendous amount of money by reselling Travelex’s PII on the darkweb. As such, they demanded Travelex pay upwards of 4.6 million pounds for the recovery of the data and to prevent further exposure. The impact of the event also affected more than a dozen UK banks by taking down their foreign currency services. The Sodinokibi operators followed through on their threat to release information publicly after Artech, an IT staffing company, failed to pay the actor’s ransom demands on time.
The Sodinokibi actors followed in the foot steps of the Maze group who earlier released stolen data after compromising the network of security staffing firm Allied Universal. Operators demanded the company pay 300 bitcoins, or around 2.3 million US dollars, at the time of the attack to release the files. Not only did the malicious actors threaten, and subsequently follow through with, exposing company data publicly, the actors engaged directly with bleepingcomputer.com to break the story. Maze operators leaked a subset of Allied’s data, including termination agreements, contracts, medical records, and other sensitive data after the timeline to pay had expired and subsequently increased the ransom demand to 3.8 million to prevent further leaks. [source]
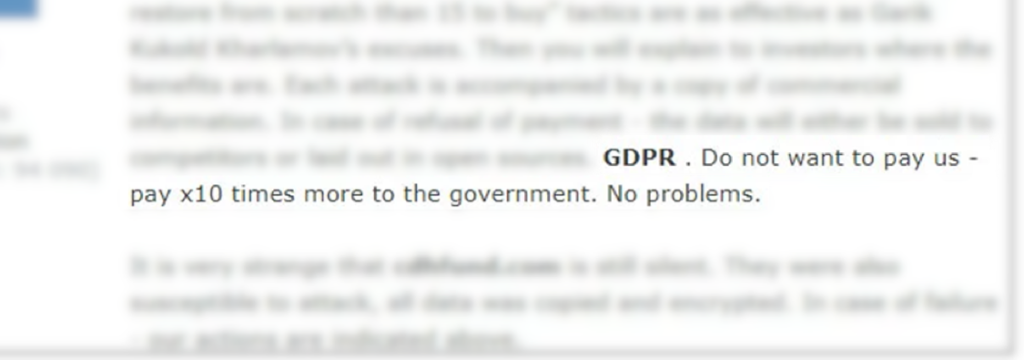
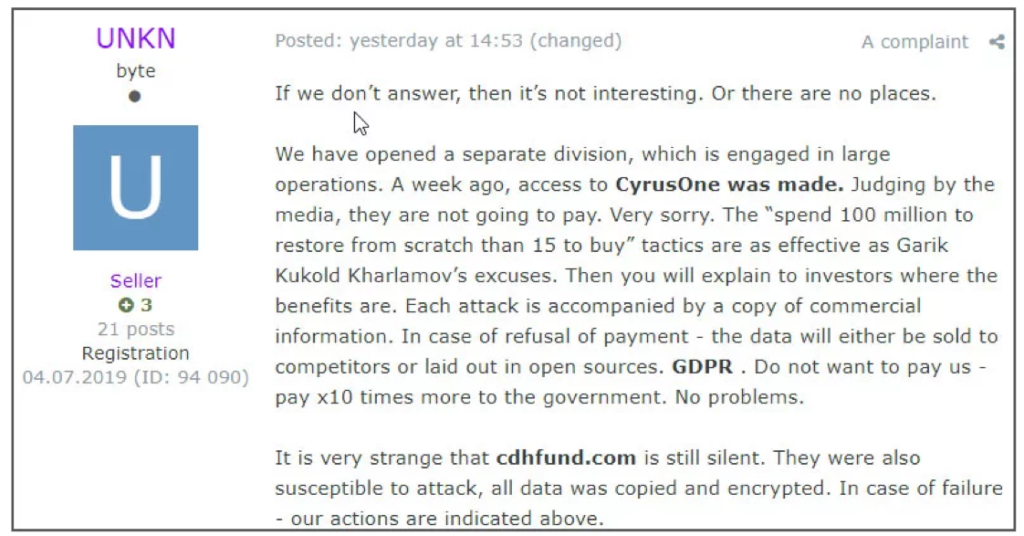 [Russian forum post]
[Russian forum post]
In a very recent incident, cyber criminals operating DoppelPaymer ransomware began to make headlines after infecting Visser Precision manufacturing. This incident is particularly interesting as some of the material published by the malicious actors exposed non-disclosure agreements between Visser and other companies such as Tesla and SpaceX. Previews of Visser’s data, released on a shaming site created by the DoppelPaymer crew, show folders and files implicating business dealings with other companies like Boeing and Lockheed Martin. [source]
As we move away from “spray and pray” attacks, it’s a fair question to ask how these malicious actors target an organization. Cursory searches online can often reveal the types of data an organization may be handling. Payment information, personally identifiable information, as well as electronic personal health information are all data types that could prove useful to an attacker when trying to extort the target organization. Additional information about cyber operations within an organization could be gathered by searching for infosec personnel on LinkedIn, looking at job postings on popular sites focused on cyber hiring, or collecting social media information from executives or cyber employees. These services can reveal clues to the security posture of an organization and may help make it a more attractive target. Attackers may also use public financial filings in addition to calculated regulatory fines for leaked data types to influence their decision in who to target, how much to ask for in their ransom demands, and how to frame the language of the demand to elicit the best response.
Whether a threat actor’s motivation is driven by financial gain, ideological difference, or nation state, they will continue to evolve their attacks in response to security’s evolution. It seems likely that these combined exfil + ransomware tactics are effective enough that they will not only persist, but continue to evolve. That evolution requires cyber professionals and business leaders alike to embrace creative thinking in combating an ever-increasing threat to your business and partners.
CYDERES is primed to help with threats like ransomware, and can help organizations in situations like those detailed above. If you are interested in finding out more about how CYDERES can help your organization combat ransomware and beyond, fill out the form below.
