
“Intelligence drives operations”
Gen A.M. Gray 29th Commandant of the United States Marine Corps
In the art of warfare, intelligence gathering on an adversary has been a long-standing practice that aids military commanders in making decisions on future operations. During the American Revolutionary War, the odds were stacked against the American army. General George Washington required a foolproof plan to even the playing field against the intimidating and larger British force. His answer to this was espionage. Washington employed ordinary people to build spy rings, turned British spies into double agents and established multiple networks of agents informing him of what the next plans were. Mail was intercepted, opened and copied without breaking the seals, making him the master of this war. With the intelligence gathered, Washington created a massive man-in-the-middle deception operation which caused confusion and disrupted British communications.
Likewise, cyber intelligence is used to gain knowledge on the adversary, disrupt its operation and prevent future attacks. How does an attacker or threat actor gather intelligence on their next target? Other than open-source intelligence, what tools, tactics or techniques do they use to gain a foothold inside their targets’ network?
Not so charming kitten
The espionage group APT35, is known for conducting long-term resource-intensive operations to collect strategic intelligence. APT35, also known as Phosphorus, Charming Kitten and Ajax Security, has been seen conducting operations dating back to 2014. This threat actor group has conducted intelligence campaigns against individuals in the United Kingdom, the Middle East and North America. Assessments have been made that APT35 works from Iran and is likely sponsored by a domestic government agency.
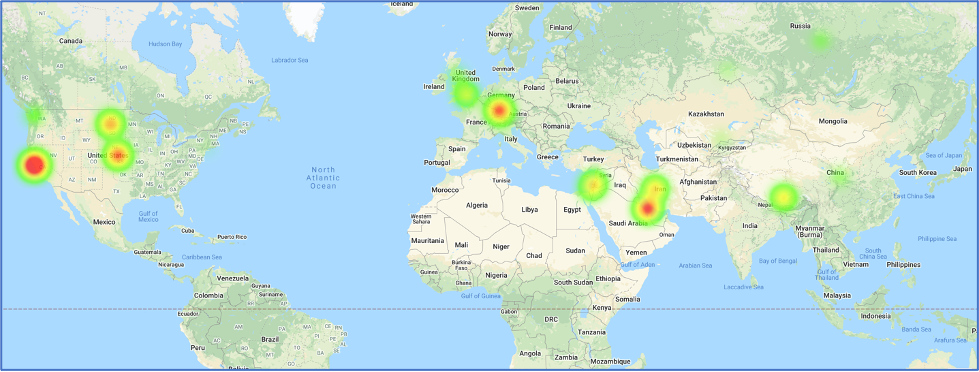
Map references related to APT35
One of the main tactics APT35 uses is Phishing, and social engineering is the usual method of executing it. In November 2019, APT35 used a fake interview scenario to target their victims. The threat actor group impersonated the New York Times journalist Farnaz Fassihi and used this identity as a Wall Street Journal reporter to send interview requests.
Trust and Reconnaissance
The first part of this phishing campaign is to gain the trust of the target. This was accomplished by sending emails from the email address farnaz.fassihi[at]gmail[.]com. The email states Farnaz Fasihi is a journalist at the Wall Street Journal Newspaper requesting an interview to share some of the victim’s important achievements” with their audience. They mention their Middle East team of the WSJ intends to introduce successful nonlocal individuals to motivate the youth in their country to discover their talents and be successful. A screenshot of the email retrieved from Certfa can be seen below.
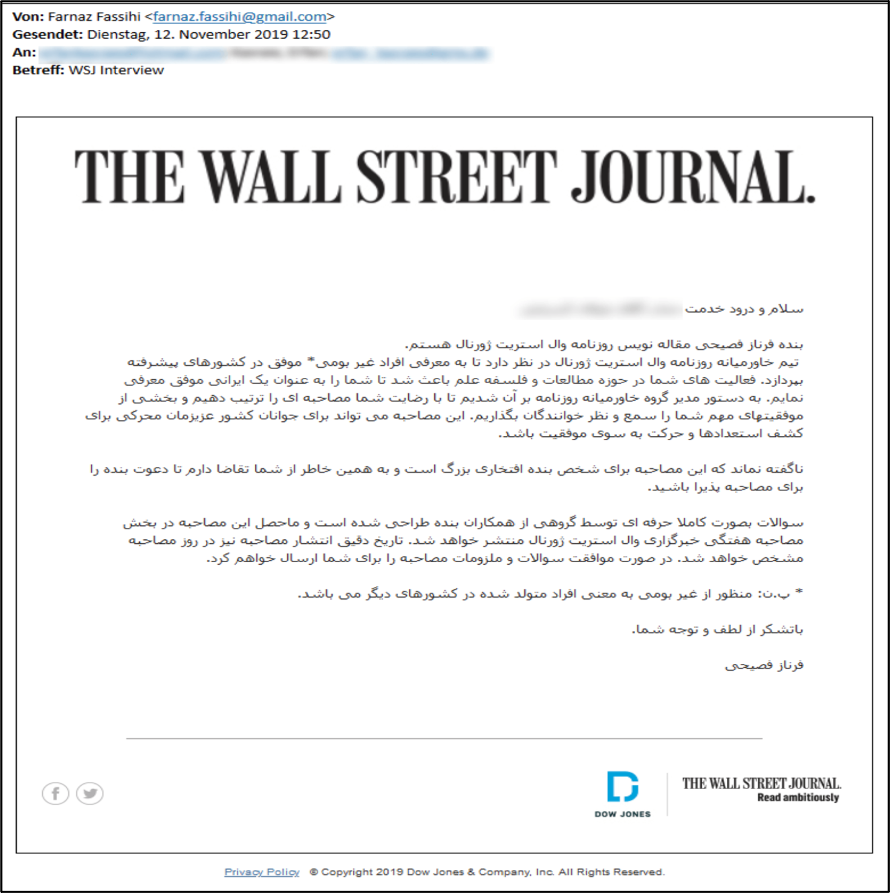 Email impersonating Wall Street journalist
Email impersonating Wall Street journalist
Other than crafting these emails to gain trust, they also serve as part of the intelligence gathering that APT35 is known for. The URLs found on these emails are all in the short URL format, which the threat actor group can use to direct the victims to legitimate addresses while gathering intelligence on their victims. The basic information that can be acquired by using a short URL service like bitly are the victim’s IP address, the type of operating system and the browser. The intelligence gathered enables the attacker to tailor future attacks based on victims’ devices.
Final Payload
Once trust is gained with the victim, the final link containing the supposed “interview questions” is sent. This link directs the victim to a phishing page hosted on Google Sites, making the victim trust the destination domain and evading spam detections. The final destination of the download link redirects the victim to a fake page in two-step-checkup[.]site domain where the credentials and the two-factor authentication (2FA) code are requested by phishing kits. One such phishing kit is Modlishka, a penetration testing tool that can bypass 2FA and automate phishing attacks. This tool, available on Github, employs reverse proxy in a way that facilitates phishing attacks.
A piece of malware with the file name pdfReader.exe was also used in this campaign. Analysis of the file shows it modifies the Registry and the Windows Firewall for it to run on the victim’s machine and also gathers intelligence from the victim’s device which gets sent to the attacker. This type of malware, known as a loader, is used to run new malware remotely on the victim’s machine.
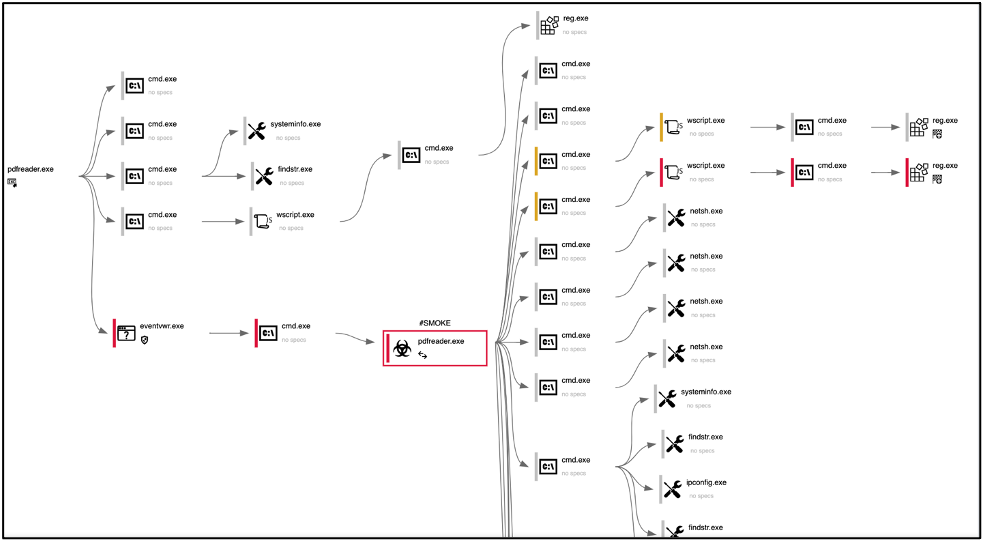
Loader Process Graph
Holiday intelligence Campaign
During the holidays in December and January, APT35 started a targeted phishing campaign of espionage against individuals to gather intelligence. The same tactics, techniques and procedures (TTPs) were used for this intelligence campaign. The campaign started during the time most offices are closed due to the holidays. This was an important step in their campaign because most IT departments were not able to neutralize this cyber event. APT35 took full advantage of this timing to execute this campaign and stack their odds in their favor.
The attack vectors in this campaign were fake SMS and fake emails. The SMS impersonated Google Account Recovery messages and required confirmation by clicking on a hXXs://www.google[.]com/url?q=https://script[.]google[.]com URL. At first glance, the URLs seem legitimate but after opening the links, they perform several redirections and finally lead to a phishing page. The emails were titled “New Year Greetings” and “Merry Xmas and My Gift” with the body of the email mentioning a book as their “gift” to friends and asking the victim’s thoughts on it after downloading it.
The intelligence-gathering tactics in these campaigns worth noting are the following:
- Attacks focused on individuals online accounts
- Gmail
- Yahoo
- Outlook
- Victims’ organizations accounts
- Targeted members of:
- Think tanks
- Political research centers
- University professors
- Countries targeted:
- Persian Gulf
- Europe
- United States
- Attack Vectors include:
- Spearphishing lures related to:
- Health care
- Job postings
- Resumes
- Password policies
- Spearphishing lures related to:
APT35 has been known to use:
- Compromised accounts with credentials harvested from prior operations
- Strategic web compromises
- Password spray attacks against externally facing web applications
- Publicly available webshells
- Associated Malware/Tools:
- Houseblend
- Drubot
- Aspxhellsv
- Pupyrat
- Mangopunch
- Tunna
- Brokeyolk
- Downpaper
- Elvendoor
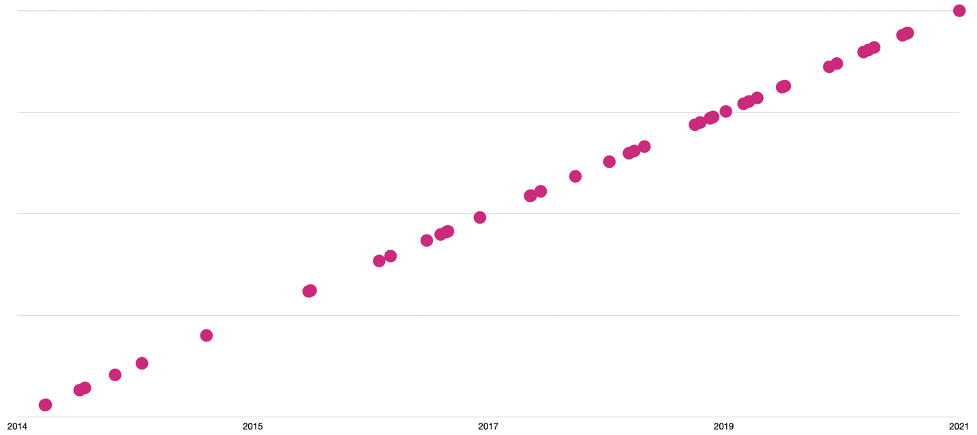
APT35 Campaigns Timeline
Conclusion
Over the past couple of years, APT35 has conducted spear phishing attacks likely for conducting cyber espionage. It is expected for this threat actor group to continue using this technique as a way to gain an initial foothold into the target’s network. When APT35 was publicly identified in 2014, the targets included U.S. military and government personnel, the UK and Middle Eastern nations on LinkedIn, now the threat actor group has evolved into performing broad strategic and tactical cyber espionage activity. The initial focus of APT35 was to establish contact with the targets via social networking platforms which broaden network reconnaissance opportunities. Establishing fake news domains and personas and creating spear-phishing emails were the first TTPs discovered in 2014. These TTPs remain the foundational blocks of APT’s modus operandi while evolving to pivot into new domains, further increasing its targeting range. APT35 is still active in the cyber landscape and on social media platforms.
| MITRE TTPs: | ID: |
| Account Manipulation: Exchange Email Delegate Permissions | T1098.002 |
| Application Layer Protocol | T1071 |
| Web Protocols | T1071.001 |
| Archive Collected Data: Archive via Utility | T1560.001 |
| Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | T1547.001 |
| Command and Scripting Interpreter: Visual Basic | T1059.005 |
| Command and Scripting Interpreter: Windows Command Shell | T1059.003 |
| Command and Scripting Interpreter: PowerShell | (T1059.001 |
| Credentials from Password Stores: Credentials from Web Browsers | T1555.003 |
| Email Collection: Local Email Collection | T1114.001 |
| File and Directory Discovery | T1083 |
| Hide Artifacts: Hidden Window | T1564.003 |
| Indicator Removal on Host: File Deletion | T1070.004 |
| Ingress Tool Transfer | T1105 |
| Input Capture: Keylogging | T1056.001 |
| Non-Standard Port | T1571 |
| Obfuscated Files or Information | T1027 |
| OS Credential Dumping: LSASS Memory | T1003.001 |
| Phishing: Spearphishing Link | T1566.002 |
| Phishing: Spearphishing Attachment | T1566.001 |
| Phishing: Spearphishing via Service | T1566.003 |
| Process Discovery | T1057 |
| Screen Capture | T1113 |
| System Information Discovery | T1082 |
| System Network Configuration Discovery | T1016 |
| System Owner/User Discovery | T1033 |
| User Execution: Malicious File | T1204.002 |
| Web Service: Bidirectional Communication | T1102.002 |
| IOCs: |
| 54.37.164[.]254 |
| 109.202.99[.]98 |
| 134.19.188[.]242 |
| 134.19.188[.]243 |
| 134.19.188[.]244 |
| 134.19.188[.]246 |
| 185.23.214[.]188 |
| 213.152.176[.]205 |
| 213.152.176[.]206 |
| 146.59.185[.]15 |
| 146.59.185[.]19 |
| 185.23.214[.]187 |
| com-254514785965[.]site |
| mobile[.]verification[.]session[.]com-254514785965[.]site |
| session[.]com-254514785965[.]site |
| verification[.]session[.]com-254514785965[.]site |
| www[.]com-254514785965[.]site |
| com-5464825879854[.]site |
| mobile[.]verify[.]service[.]com-5464825879854[.]site |
| service[.]com-5464825879854[.]site |
| verify[.]service[.]com-5464825879854[.]site |
| www[.]com-5464825879854[.]site |
| benefitsredington[.]ddns[.]net |
| lonelymanshadow[.]ddns[.]net |
| mobile-activity-session[.]site |
| verify[.]mobile-activity-session[.]site |
| www[.]mobile-activity-session[.]site |
| mobile-check-activity[.]site |
| www[.]mobile-check-activity[.]site |
| com[.]recover-session-service[.]site |
| mobile[.]recover-session-service[.]site |
| news12[.]com[.]recover-session-service[.]site |
| recover-session-service[.]site |
| www[.]recover-session-service[.]site |
| hello-planet[.]com |
| mail-newyorker[.]com |
| profilechangeruser[.]ddns[.]net |
| www[.]service-verification[.]site |
| www[.]mobile[.]service-verification[.]site |
| service-verification[.]site |
| mobile[.]service-verification[.]site |
| mail[.]service-verification[.]site |
| com[.]service-verification[.]site |
| app-e[.]request[.]unlock-service[.]accounts[.]service-verification[.]site |
| instagram[.]com[.]service-verification[.]site |
| unlock-service[.]accounts[.]service-verification[.]site |
| request[.]unlock-service[.]accounts[.]service-verification[.]site |
| accounts[.]service-verification[.]site |
| identifier[.]recovery-session[.]site |
| recovery-session[.]site |
| www[.]recovery-session[.]site |
| www[.]identifier[.]recovery-session[.]site |
| identifier[.]session-confirmation[.]site |
| session-confirmation[.]site |
| www[.]session-confirmation[.]site |
| identity-session-recovery[.]site |
| uniquethinksession[.]ddns[.]net |
| recover-identity[.]site |
| session[.]recover-identity[.]site |
| www[.]recover-identity[.]site |
| securelogicalrepository[.]com |
| service-support[.]site |
| customer-session[.]site |
| planet[.]customer-session[.]site |
| accounts[.]customer-session[.]site |
| www[.]customer-session[.]site |
| www[.]service-support[.]site |
| identifier[.]service-support[.]site |
| planet[.]service-support[.]site |
| reset-account[.]com |
| google[.]reset-account[.]com |
| www[.]reset-account[.]com |
| session-customer-activity[.]site |
| verify[.]session-customer-activity[.]site |
| www[.]session-customer-activity[.]site |
| www[.]identifier-service-verify[.]site |
| identifier-service-verify[.]site |
| mobile[.]identifier-service-verify[.]site |
| challengechampions[.]ddns[.]net |
| service-verification-session[.]site |
| mobile[.]service-verification-session[.]site |
| www[.]service-verification-session[.]site |
| chn[.]archiverepositories[.]xyz |
| www[.]archiverepositories[.]xyz |
| archiverepositories[.]xyz |
| a[.]archiverepositories[.]xyz |
| wearefirefighters[.]ddns[.]net |
| basementofdarkness[.]ddns[.]net |
| heisonhisway[.]ddns[.]net |
| recover-session[.]site |
| www[.]recover-session[.]site |
| myaccount[.]recover-session[.]site |
| schoolofculture[.]ddns[.]net |
| customer[.]verification[.]com-3654623478192[.]site |
| com-3654623478192[.]site |
| customer[.]com-3654623478192[.]site |
| www[.]com-3654623478192[.]site |
| verification[.]com-3654623478192[.]site |
| enhanceservicchecke[.]hopto[.]org |
| minimumservicechek[.]ddns[.]net |
| playstore[.]com-apk-6712qw123asd8awf7[.]site |
| www[.]com-apk-6712qw123asd8awf7[.]site |
| www[.]identifier-session-recovery[.]site |
| google[.]com-apk-6712qw123asd8awf7[.]site |
| play[.]google[.]com-apk-6712qw123asd8awf7[.]site |
| identifier-session-recovery[.]site |
| com-apk-6712qw123asd8awf7[.]site |
| agentappservice[.]ddns[.]net |
| www[.]com-archive[.]site |
| com-archive[.]site |
| patchtheschool[.]ddns[.]net |
| www[.]recovery-session-service[.]site |
| mobile[.]recovery-session-service[.]site |
| homeinspections[.]ddns[.]net |
| recovery-session-service[.]site |
| deepthinkingroom[.]ddns[.]net |
| randomworldcity[.]ddns[.]net |
| bulk-approach[.]site |
| www[.]bulk-approach[.]site |
| confirm-identity[.]site |
| www[.]confirm-identity[.]site |
| dynamiceventmanager[.]ddns[.]net |
| service-recovery[.]site |
| differentintegrated[.]ddns[.]net |
| verify-session-service[.]site |
| yahoo[.]verify-session-service[.]site |
| mail[.]yahoo[.]verify-session-service[.]site |
| www[.]verify-session-service[.]site |
| mobile[.]verify-session-service[.]site |
| session[.]recovery-customer-service[.]site |
| recovery-customer-service[.]site |
| www[.]recovery-customer-service[.]site |
| homedirections[.]ddns[.]net |
| recovery-session-verify[.]site |
| www[.]recovery-session-verify[.]site |
| identifier[.]recovery-session-verify[.]site |
| service-session-recovery[.]site |
| mobile[.]service-session-recovery[.]site |
| www[.]service-session-recovery[.]site |
| planet-labs[.]site |
| mail[.]com-posts6712qw12387[.]site |
| video[.]instagram[.]service-recovery[.]site |
| insgram[.]service-recovery[.]site |
| identifier[.]service-recovery[.]site |
| instagram[.]service-recovery[.]site |
| www[.]planet-labs[.]site |
| com-posts6712qw12387[.]site |
| www[.]com-posts6712qw12387[.]site |
| www[.]service-recovery[.]site |
| planet-map[.]gigfa[.]com |
