Fishtech Group Completes Acquisition of Haystax
Cybersecurity firm’s capabilities include UBA and Public Safety and Security
Kansas City, MO (July 13, 2018) — Fishtech Group (FTG) has completed its acquisition of Haystax (previously Haystax Technology), an advanced security analytics and risk management solutions provider, as a wholly owned entity under the FTG umbrella. The acquisition extends the cybersecurity firm’s capabilities in new markets including User Behavior Analytics (UBA) and Public Safety and Security. Fishtech is investing heavily in taking the new venture to market in the commercial enterprise space.
Announced in May, the acquisition solidifies the cybersecurity solutions firm’s relationship with Haystax, which had been a Fishtech Venture Group partner since 2016.
The new entity furthers Fishtech’s mission of data-driven security solutions while extending Haystax’s customer reach beyond its roots in homeland security and public safety. Gary Fish, CEO and Founder of Fishtech, serves as CEO and Pete Shah will be Chief Operations Officer. Haystax will retain its base in McLean, Virginia.
“This is a 1+1=3 scenario in that our combined capabilities are so far beyond what either entity could accomplish alone,” said Fish. “We’re expanding the sales force and the brand message to a national scale. We’re already gaining traction into enterprise accounts nationally.”
Haystax’s Constellation analytics platform flexes to and delivers a wide array of advanced security analytics and risk management solutions that enable rapid understanding and response to virtually any type of cyber or physical threats. Based on a patented model-driven approach that applies multiple artificial intelligence techniques, it reasons like a team of expert analysts to detect complex threats and prioritize risks in real time at scale for more effective protection of critical systems, data, facilities and people.
“The Constellation platform has proven itself to be a versatile and effective platform for insider threat, security operation center (SOC) automation, and public safety,” said Fish. “We look forward to working closely with the Haystax team to further enhance those capabilities and develop other applications for its use.”
About Haystax
Founded in 2012, Haystax is a leading security analytics platform provider based in McLean, Virginia.
About Fishtech Group
Fishtech delivers operational efficiencies and improved security posture for its clients through cloud-focused, data-driven solutions. Fishtech is based in Kansas City, Missouri. Visit https://fishtech.group/ or contact us at info@fishtech.group.
SOAR Above Threats to your Organization
June 7, 2018Cybersecurity Insights
If you’ve ever questioned whether your SOC team is missing things or your MSSP is keeping up, you’re not alone. That’s why SOAR (Security Orchestration Automation and Response) is gaining popularity fast.
It’s an easy way to do more with less.
“Our experts deliver a force multiplier for your overworked analyst teams,” says Fishtech CISO Eric Foster.
McLean cyber company whose tech is used by the NFL is being acquired
By Robert J. Terry – Senior Staff Reporter, Washington Business Journal
Key story highlights:
- Fishtech Group is buying McLean-based Haystax Technology and will take the company to market in the commercial enterprise space.
- “People spend a lot of time and money securing their data but they’re not using their data to drive security,” said CEO Gary Fish.
- Haystax’s security analytics platform has been used by the U.S. Department of Defense and the National Football League.
A Kansas City holding company’s deal to acquire McLean-based Haystax Technology is a bid to bring advanced analytics and automation to commercial and government cybersecurity markets.
Fishtech Group plans to make Haystax a wholly owned subsidiary and invest heavily in taking the new venture to market in the commercial enterprise space, particularly heavily regulated industries such as finance and health care. It’s also planning to enhance Haystax’s presence in federal, state and local government markets beyond its roots in homeland security and public safety.
Haystax’s security analytics platform has been used by the U.S. Department of Defense to help track terrorists. The National Football League used the platform to monitor suspicious activity and prevent cyber and physical threats at the Super Bowl. And the state of California used the technology to crunch data from earthquake sensors to predict when earthquakes might occur.
Fishtech CEO Gary Fish said the Haystax mission fits well with his company’s push to use big data, sophisticated analytics, artificial intelligence and machine learning to disrupt the security integration market, where the big vendors are focused on-premises and in networks with well-defined perimeters. In an age of cloud computing and thousands of mobile endpoints, there’s no longer really a perimeter for an organization’s data, but there are reams of insights in that data to enhance an overall security posture.
“People spend a lot of time and money securing their data but they’re not using their data to drive security. If you look in the data you can find what’s causing your security issues potentially,” Fish told me Wednesday. “Haystax brings in large amounts of log data and system data and personnel data and by letting algorithms, the machine learning, the artificial intelligence, by letting the machines sift through this they can see much more than a human could possibly find in the data.”
The two companies know each other well. Fishtech invested $4 million in Haystax in December 2016. When it came time to consider additional investment, Fish decided the better course was to acquire the company, which has about $10 million in annual revenue. He wouldn’t disclose the transaction’s terms but said he expects Haystax to grow 30 percent to 40 percent annually and continue to add to its 50-employee headcount.
Fish will be CEO of Haystax while Pete Shah, the former chief revenue officer, will become COO.
Haystax was launched in 2013 when private equity firm Edgewater Funds acquired two Northern Virginia companies, Digital Sandbox Inc. and FlexPoint Technology LLC, and set out creating a cyber platform for defense, intelligence agency and commercial clients. Edgewater had linked up the year before with Bill Van Vleet, a cyber exec with ties both here and in California, to build a next-generation intelligence company. Van Vleet was previously CEO of Applied Signal Technology Inc., which he sold to Raytheon for approximately $500 million.
Fish said Edgewater will stay on as a minority owner.
Last month, two local cyber startups unveiled Series B venture funding rounds of $20 million or more on successive days, underscoring the market opportunity at a time of increasingly complex threats by well-organized nefarious actors, often state-backed. Upstarts maintain the established players can’t address cyber threats well or don’t measure up to what customers want — but it’s also, critics say, ushered in a lot of the noise in the market courtesy of companies that are long on marketing but short on technology that does what it says it does.
Who Gets In | Microsoft Conditional Access
April 23, 2018Cybersecurity Insights
The question of controlling access to an organization’s data and systems comes up often in our conversations with customers. Recently we had another customer ask how to ensure that devices being used to access their cloud environment met their security requirements.
While there are several ways to address that issue, one of the technical solutions we did some digging on was Microsoft’s Conditional Access solution that is part of Azure AD and Intune.
What follows below are some of the key findings we uncovered in configuring Microsoft Conditional Access via Intune.
Licensing Model(s)
While there are several ways to gain access to Conditional Access functionality within the Microsoft cloud platform, we decided to go down the Intune route.
This is because we wanted to be able to apply access policies based on different aspects of the device which in the Microsoft world means Intune is needed.
In addition, Intune provides ways to manage other aspects of both mobile and laptop/desktop devices which is a bonus.
So in order to get the functionality of Intune and Conditional Access you will need to look at Microsoft’s Enterprise Mobility + Security (EMS) offerings. The licensing models break down like this:
- EMS E3
- Intune
- Azure AD Premium P1
- Azure Information Protection P1
- Advanced Threat Analytics
- EMS E5
- Intune
- Azure AD Premium P2
- Azure Information Protection P2
- Advanced Threat Analytics
- Cloud App Security
- Azure Advanced Threat Protection
For the purposes of this article the minimum level needed is EMS E3 which adds Conditional Access functionality. Not to be confusing (yeah right), but in order to get ‘Risk-based Conditional Access’ the top level EMS E5 subscription is needed.
The primary difference between Conditional Access and Risk-based Conditional Access is that Conditional Access allows policies to be built based on User/Location, Device, and Application criteria while Risk-based Conditional Access adds Microsoft’s Intelligent Security Graph and machine learning to create a more dynamic risk profile to control access.
A final point about licensing. It is complex. Get your Microsoft contact involved to help figure out the licensing details for specific situations because there are many paths to the same destination.
Setting up Conditional Access
In order to configure a Conditional Access policy, there are a few pre-requisites that need to be configured. The specifics of configuring those pre-requisites is beyond the scope of this article, but the broad strokes are that you have properly set up and configured your azure account, Azure AD, and Intune.
This includes ensuring you have some Azure AD users and groups defined that policies can be applied to. Again, this is an oversimplification so my apologies if I left major pieces out.
Now we move into actually creating a Conditional Access policy. Fair warning, I will not cover every possible scenario. Instead, I will try to convey the major concepts and features of a Conditional Access policy as well as any gotchas I came across.
Open up your Azure portal and navigate to Intune>Conditional Access
Note: You can also find Conditional Access by navigating to Azure Active Directory>Conditional Access. In fact, this may be the better route to go because this path exposes additional options that you won’t find by navigating there via Intune.
For example, in the Azure AD Conditional Access portal you can create custom controls using JSON. You can also define named locations, VPN connectivity, terms of service.
In the right-hand pane, click + New Policy and a new policy window will open.
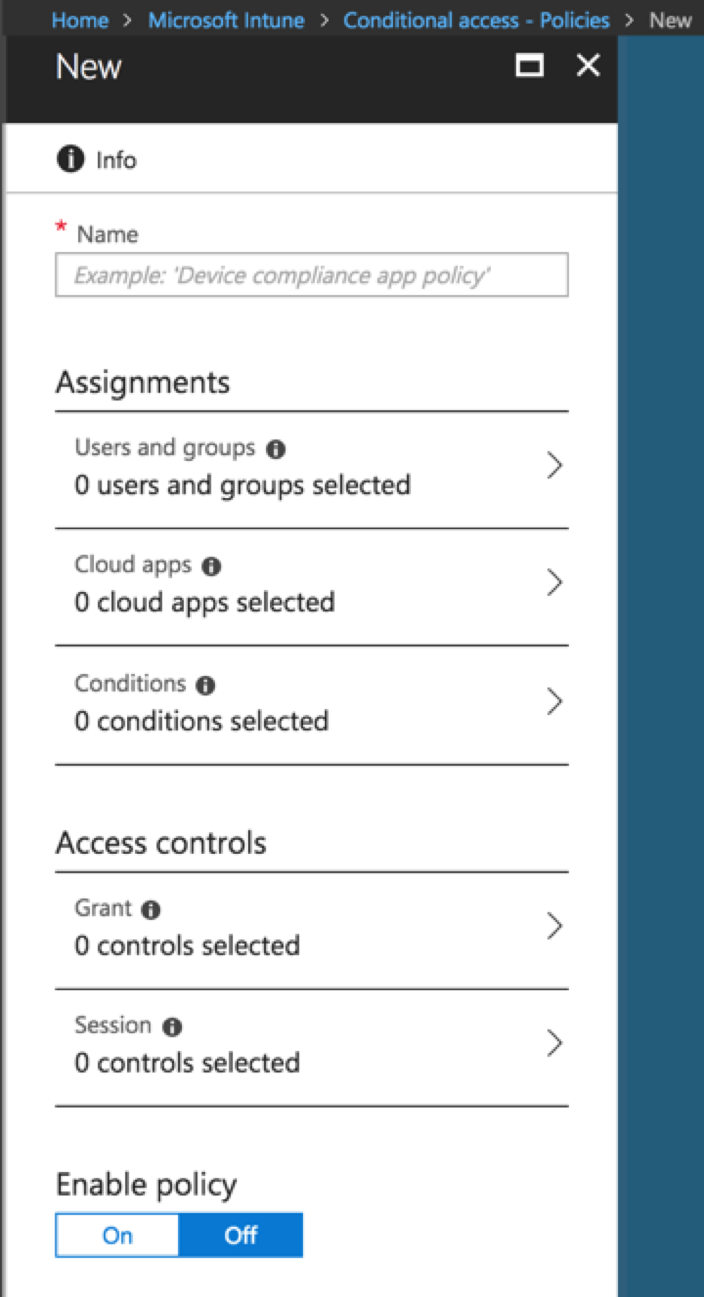
The two main sections of a Conditional Access policy are ‘Assignments’ and ‘Access Controls’
Assignments:
- Users and Groups
- Select the users and/or groups the policy will be applied to.
- Cloud Apps
- Select the Cloud Apps to be covered by the policy. O386 apps are available by default. Others can be added as needed (beyond the scope of this article)
- Conditions
- The conditions under which the policy will apply.
- The four condition areas are
- sign-in risk (Requires the EMS E5 plan I believe)
- Device platforms (ios, windows, android, etc.)
- Locations (requires configuring locations in Azure Portal)
- Client Apps (browser or client app)
Access Controls
- Grant (block or grant access based on additional criteria)
- Require multi-factor authentication
- Require device to be marked as compliant (more on this below)
- Require domain joined
- Require approved client app
- Session
- App enforced (in preview release)
- Proxy enforced (in preview release)
Once these sections have been completed the policy just needs to be enabled to take effect.
A word about Device Compliance
In order to select the ‘Require device to be marked as compliant’ option in the Grant section of an Access Control policy, you will need to create a Device compliance policy (or several depending on your needs). Device Compliance policies are pretty much what they sound like.
A set rules that indicate whether a managed device complies with your organization’s requirements. Depending on whether the device in question does or does not meet the compliance policy, it will be marked as either ‘Compliant’ or ‘Not Compliant’.
For a device compliance policy to work on a given device, it must be managed by Intune. It is beyond the scope of this article to get into the details of how devices are enrolled and managed in Intune, but at a high-level Intune can manage both personally owned and corporate owned devices.
To create a Device Compliance policy open up your Azure portal and navigate to Intune>Device Compliance >Policies and click “+ Create Policy”.
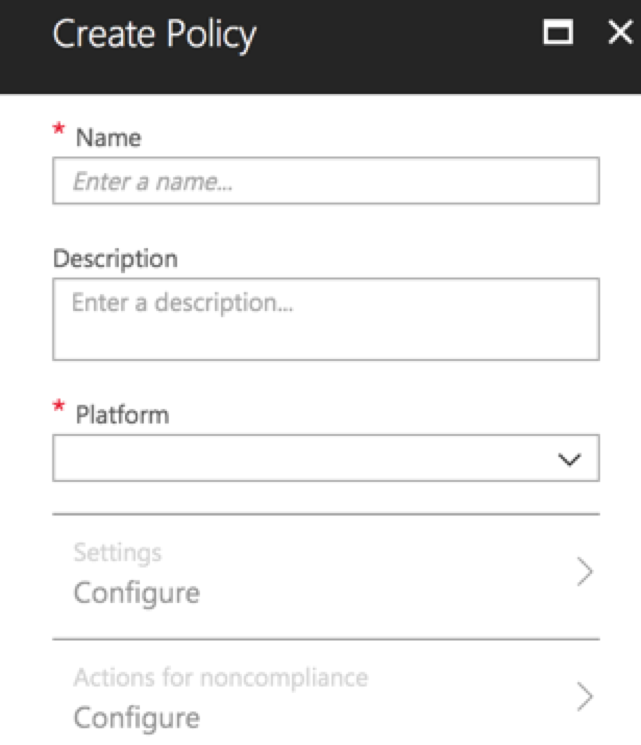 After entering a Name and selecting a platform to apply the policy to, click on Settings>Configure.
After entering a Name and selecting a platform to apply the policy to, click on Settings>Configure.
The policy settings have three categories of configuration. Note: The number of options under each category will change based on the OS platform that was selected.
- Device Health (settings vary based on OS. Examples for Win10 include Require BitLocker and Require code integrity)
- Device Properties (settings vary based on OS. Examples for Win10 include Minimum OS version and Maximum OS version)
- System Security (settings vary based on OS. Examples for Win10 include Require a password to unlock device and block simple passwords)
Once the policy is created, it must be assigned. Click on ‘Assignments’ and choose either a group or ‘All Users’. Warning, it is not recommended to apply policies to all users as there could be unintended consequences. The main point is to know who you are applying policies to so as to minimize surprises.
Now that a compliance policy has been applied it will require a check-in by the targeted user’s device(s) so that the device can run the compliance scan and return a compliant/not compliant result. This compliance assessment can then be used in a Conditional Access policy as described in the previous section.
Final thoughts
In wrapping all of this up there are a few things to keep in mind. First, the licensing aspect of Intune/Conditional Access is unclear from a non-employee standpoint. So for anyone looking to use Microsoft’s Conditional Access to address non-employee scenarios, further digging will be required.
Second, while it may seem mind-numbingly obvious, organizations that are already invested in Azure AD and O365 should take a serious look at Microsoft’s Conditional Access. With the proliferation of security tools in the market, it is sadly true that many organizations continue purchasing more tools when they may already have an adequate solution in hand.
In addition, Microsoft is taking cloud security very seriously and from what I can tell will continue to invest in improving their security solutions.
Related Links:
- Intune/EMS Subscription Levels
- Microsoft Conditional Access
- Integrating Threat Defense to Intune for compliance policies
CYDERES Announces Availability of EMDR Service
KANSAS CITY, Mo., April 6, 2018 /PRNewswire/ — CYDERES, the security-as-a-service division of Fishtech Group, today announced the availability of CYDERES EMDR, its Managed Detection and Response (MDR) service that helps organizations with detection, investigation, remediation, and proactive hunting of threats.
As security breaches continue to escalate in pace and scope, CYDERES EMDR is a human-led, machine-driven managed detection and response service that integrates security tools with exceptional experts to drive automated outcomes via a proprietary platform. CYDERES supplies the people, process, and technology to help organizations manage cybersecurity risks, detect threats, and respond to security incidents in real-time.
“CYDERES answers a problem that wasn’t being solved – how organizations can defend their data and stay focused on their core business,” said Fishtech CEO and Founder Gary Fish. “Our proprietary platform is revolutionary in the way it gathers disparate data together for effective, real-time threat detection.”
The CYDERES EMDR offering combines threat detection, investigation, remediation, and proactive threat hunting through:
- Technology independence
We believe organizations must be free to select the right security solutions for their needs. The CYDERES platform drives automated outcomes and real-time interdiction leveraging those technologies, without requiring a specific set of security tools or locking you in to a proprietary SIEM. - Coverage across modern hybrid, private and public cloud, plus on-premise environments
Our team includes experienced SecDevOps experts and Certified Cloud Security Professionals who can help secure on-premise environments as well as a migration to the cloud. - Action-oriented
We don’t route alerts. A lot of MSSPs create more work for their customers. We’re here to serve as a true force multiplier to your team and drive real-time interdiction of threats.
“Organizations are under constant attack and prevention alone is failing,” said Fishtech CISO Eric Foster, who leads the CYDERES team. “Cybersecurity today requires actively detecting threats and responding in real time. While that’s not feasible for most organizations, we are committed to offering legendary service at a fair price to enable organizations to meaningfully improve their detection and response capabilities.”
In March, Fishtech broke ground on its 20,000 square foot Cyber Defense Center, which will house the CYDERES team. Fish and Foster will demo the CYDERES platform during the upcoming 2018 RSA Conference.
About Fishtech Group
Fishtech delivers operational efficiencies and improved security posture for its clients through cloud-focused, data-driven solutions.





