How CNAP 2.0 Unlocks Security Analytics at Hyperscale
SIEM and SOC operations have never been more crucial.
Organizations’ risk landscape is increasing exponentially (ransomware, business email compromise, state actors, just to name a few), exacerbating existing internal challenges of legacy architecture, outdated programs, and an all-around cyber skills shortage even further.
As we’ve said many times, hype and gimmicks, all too often the hallmarks of cybersecurity products will not solve today’s problems. Only real solutions custom-built from a deep understanding of the daily challenges organizations face combined with in-the-trenches know-how should lead the way.
That’s why we are proud to announce the latest customer-value driven upgrades to our Cloud Native Analytics Platform in CNAP 2.0.
First, let’s remember why CNAP was built in the first place from Eric Foster, President of CYDERES.
How CNAP Empowers Google Cloud’s Autonomic Security Operations
Our partner Google Cloud understands the challenges organizations face in modernizing their security operations. Recently, at their first annual Google Cloud Security Summit Series event, they unveiled Autonomic Security Operations, which they define as a combination of philosophies, practices, and tools that improve an organization’s ability to withstand security attacks through an adaptive, agile, and highly automated approach to threat management.
The goal here is to stack your defenses to manage modern threats at Cloud-scale empowering:
Accelerated Transformation
Workshops, technical content, products, integrations, and blueprints designed to help organizations kick-start their modernization journey to a state of autonomic security operations.
Increased Business Agility
Intelligent data fusion, continuous IoC matching, sub-second petabyte-scale queries, and modern YARA-L detection to conduct plaid-speed management of threats at a disruptive cost and massive scale.
Maximized Use-Case Coverage
Hunt for APTs, detect ransomware, investigate network anomalies, identify fraud signals, in-house or with detection and response capabilities of the expert team at CYDERES.
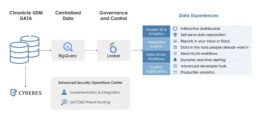
CNAP harnesses the speed and power of Chronicle while layering on vital operational functionality with threat detection rules, dashboards and reporting, investigation and hunt capabilities, ticketing system integrations, and a broad range of custom triage workflows and playbooks that scale across petabytes of customer logs in real-time.
As part of CYDERES CNAP 2.0 launch program, new and existing clients’ UDM parsed security telemetry data in Google Chronicle now leverages industry leading big data analytics tools, BigQuery and Looker, for both pre-built and customized dashboards to easily visualize data ingestion and health, IOC matches, threat detections, authentication events, and much more.
“Security operations in an increasingly digital world, facing ever more sophisticated adversaries, requires a 10X increase in capabilities. Autonomic Security Operations not only powers this improved protection but also sets the stage for ongoing transformation to stay ahead of the threat.” Phil Venables, Chief Information Security Officer, Google Cloud
Learn more about CNAP 2.0 benefits from Cassandra Varvel, CYDERES Director of Engineering.
To summarize, CNAP 2.0 enables security analytics at hyperscale with:
- Petabyte-scale detection with sub-second queries in Chronicle.
- Industry-leading data lake with unlimited ingestion powered by BigQuery.
- Rich, compelling analytics and pre-built customized dashboards via Looker.
- Continuous threat intelligence via SOCPrime’s Threat Detection Marketplace.
- Deep extensibility to a rich ecosystem of integrations.
Taking Steps to Modernize Your Security Operations with CYDERES
As we’ve seen, CNAP 2.0 augments the incredible speed and power of Google Cloud’s Chronicle with the necessary operational layers to truly function as a full-scale SIEM replacement. Similarly, CYDERES security-as-a-service tier of offerings is meant to guide organizations on a journey to full-scale 24/7 visibility, detection, and response. These can either augment your existing SOC program or serve as your primary solution.
Learn more about this tier of offerings from Jeremy Hehl, Vice President of Business Development, CYDERES.
Take a technical deep dive into CNAP 2.0
Join CYDERES and Google Cloud Security experts for a technical deep dive into winning use-cases that are equipping organizations and SOCs globally to give good the advantage and truly empower autonomic security operations, August 31st at 3PM Central.
CYDERES Announces Upgrades to Cloud Native Analytics Platform (CNAP)
Partnership with Google Cloud Continues to Revolutionize SIEM and SOC Landscape
Kansas City, MO (August 23, 2021) — CYDERES, the Security-as-a-Service division of Fishtech Group and a Top 25 MSSP, today announced significant upgrades to its proprietary Cloud Native Analytics Platform (CNAP) with a 2.0 release adding BigQuery and Looker integrations among other customer-value driven enhancements.
CYDERES 24/7/365 security-as-a-service solutions continue to enable organizations to automate and operationalize their security programs to drive unique business outcomes at a fraction of the cost of legacy solutions.
A pre-assembled cybersecurity SaaS offering built on Google Cloud Security’s Chronicle, CNAP has served as an ideal Google Cloud Platform (GCP) service for organizations looking to replace their legacy SIEM or implement Next-Gen Security Analytics, Threat Detection, and Response Capabilities.
CNAP harnesses the speed and power of Chronicle while layering on vital operational functionality with threat detection rules, dashboards and reporting, investigation and hunt capabilities, ticketing system integrations, and a broad range of custom triage workflows and playbooks that scale across petabytes of customer logs in real-time.
As part of CYDERES CNAP 2.0 launch program, new and existing clients’ UDM parsed security telemetry data in Google Chronicle now leverages industry leading big data analytics tools, BigQuery and Looker, for both pre-built and customized dashboards to easily visualize data ingestion and health, IOC matches, threat detections, authentication events, and much more.
Leveraging experience with clients across the vertical landscape, CYDERES expert team has built unique industry-specific dashboards to empower and accelerate data-driven security outcomes so that organizations can regain their focus on overall growth.
“The continued enhancements to CYDERES CNAP truly enable our customers to experience the power of security analytics at hyperscale and efficiency. The enhanced visualizations alongside the ability to perform millisecond queries across 6 months of telemetry with unmetered ingestion is a game-changer for organizations seeking to modernize their detection and response capabilities.”, said Eric Foster, President, CYDERES.
CNAP clients leverage Google Cloud’s full suite of Autonomic Security Operations, an adaptive, agile, and highly automated approach to threat management, but also additional functionality to build machine learning models, parsers, reports, and more. For CYDERES Enterprise Managed Detection and Response customers this also includes a fully dedicated backend ticketing system for the escalation and remediation of alerts.
Google Cloud Chronicle’s partner of the year two years in a row, CYDERES CNAP gives organizations a deeper, richer, and more interactive view of their security data.
About CYDERES and Fishtech
Fishtech Group is the #1 cloud native security-as-a-service solutions provider enabling secure and successful business transformation. Born in the cloud and based in Kansas City, Fishtech Group includes the 24-7 Cyber Defense and Response division CYDERES and security analytics firm Haystax in Mclean, VA.
Contact: Jennie Hanna, jennie.hanna@fishtech.group
Learn more about CYDERES award winning security as a service offerings by filling out the request form below.
Unlocking Continuous Security Intelligence with SOC Prime
24/7 threats require 24/7 diligence.
Not only does that require people, process, and technology to manage cybersecurity risks, detect threats, and respond to security incidents, it requires access to the absolute latest in real-time intelligence.
That’s exactly why we’ve partnered with SOC Prime, and their industry-leading Threat Detection Marketplace, the largest SaaS threat detection content platform in the world used by more than 12,000 security practitioners from 6,000-plus companies.
Why waste precious time building queries, rules, parsers, and other threat-detecting content when you can leverage a growing library of over 85,000 queries, rules, parsers, machine learning models, SOC-ready dashboards, and more.
What’s even better is that CYDERES customers receive customized content based on each client’s uniquely generated threat profile from our expert team via our 24/7 Enterprise Managed Detection & Response program.
Learn more of how this impacts our customers from Josh Culotta, Director of Security Operations.
Recently SOC Prime went into great detail to breakdown all the reasons why their program offered the perfect continuous security intelligence solution to complement our 24/7 Security-as-a-Service operation CYDERES.
In short, SOC Prime enables our customers to receive:
- Delivery of curated and verified detection content along with continuous support
- Proactive response to the most critical and constantly emerging threats in real-time
- Continuous threat coverage and content alignment with MITRE ATT&CK® v.9
- Seamless integration with Chronicle Security powered by Google Cloud and 20+ supported SIEM, EDR, and NTDR security solutions
Many organizations are facing the following challenges:
- How to Build Custom Behavior-Based SOC Content.
- Talent Shortage and Content Scalability Issues.
- Mass Content Migration from On-Premise SIEM to Cloud.
- Lots of SOC Team Hours on Content Development to Cover the Latest Threats.
- Continual Enrichment and Automation
Go in-depth via the case study below and learn how CYDERES and SOC Prime are overcoming these hurdles and providing continuous security intelligence for our customers.
This partnership enables CYDERES CNAP to provide advanced detection content without increasing our human capital, helping us deliver on the vision of “legendary service at a fair price” that’s been so instrumental in helping us disrupt the legacy MSSP industry. More importantly, with this incredible baseline of rules, we can repurpose our detection engineering team on creating highly customized content to optimize security protection for each of our clients. – Eric Foster, President, CYDERES
Tesseract Ventures Partners with CYDERES to Spearhead Initiatives in Cybersecurity
Partnership between these two revolutionary, award-winning cyber startups provides companies with scalable solutions to address current and future cybersecurity challenges.
KANSAS CITY, Mo. – September 2nd, 2020 – Tesseract Ventures, a Kansas City-based technology company helping organizations become smarter, better connected, and more efficient through next-generation robotics, 21st-century software, and radically connected platforms, today announced it has selected CYDERES, Fishtech Group’s Security-as-a-Service division, as a partner to assess, align and service the cybersecurity space.
This partnership will disrupt the current market, providing more cost-effective and scalable solutions to companies across all of Tesseract’s verticals including the construction, medical and military industries.
“CYDERES’ capabilities to analyze unlimited security telemetry with its Cloud Native Analytics Platform (CNAP) and the revolutionary power of Google Chronicle that Tesseract will have access to through the partnership ensures that we will have the same level of incredible insight over our security program as we bring to the table through our market expertise,” said John Boucard, founder and CEO, Tesseract Ventures. “Most importantly, the CYDERES Managed Detection and Response solution will keep our organization, employees, critical intellectual property, and our customer-facing systems safe and secure.”
This partnership contributes to Tesseract and CYDERES’ positions as leading innovators of the quietly revolutionary Kansas City business community. Aggregating CYDERES’ innovative security and analytics solution with its own advanced technology, Tesseract is able to protect its intellectual property as well as strengthen the service it provides current and future customers.
CYDERES’ skilled analysts will pilot the process of using data collected from Tesseract’s PRISM wearable robots and digital ecosystem to make insightful decisions and provide real-time alerts.
Customers can safely store all their data and have the option to receive follow up services activated by Tesseract’s Mosaic and Prism System and serviced by CYDERES.
Tesseract’s partnership with CYDERES sets sights on disrupting the cyber tech and cybersecurity industries and furthering its product and service offerings among its other verticals.
“Tesseract is enabling businesses to defy the boundaries of space and time through next-generation technologies including robots, smart spaces, wearables, and radically connected platforms,” said Eric Foster, president, CYDERES. “While it's important to protect both Tesseract and the impressive class of clients that it serves, this partnership goes far beyond CYDERES protecting Tesseract—there are many applications of Tesseract’s cyber-physical tools that are directly applicable to our clients, and we are excited to get started.”
About Fishtech Group
Born in the cloud, Fishtech Group is the leading current-generation service provider enabling secure business transformation. Our experienced cybersecurity professionals plan, produce, and implement innovative solutions that ensure security and success. We make businesses more secure while increasing productivity and visibility. We focus on threats so you can focus on your business.
Fishtech Group’s CYDERES launches Cloud Native Analytics Platform (CNAP) solution to provide enhanced SaaS SIEM bundle for Google Chronicle
CYDERES’s new platform delivers unmatched performance, scale, availability and compliance.
Kansas City, MO (July 16, 2020) — CYDERES, the Security-as-a-Service division of cybersecurity solutions provider Fishtech Group, announces the launch of its Cloud Native Analytics Platform (CNAP, pronounced ‘snap’). CNAP provides a pre-assembled cloud-native SIEM solution delivered in an as-a-Service model, designed to enhance and extend the revolutionary security analytics and unmatched data lake capabilities of the Google Chronicle platform.
“Current SIEM solutions are just repeats of past mistakes,” says Gary Fish, CEO and Founder of Fishtech Group. “With CNAP, in partnership with Google, we have completely reimagined and created what a SIEM should have been all along.”
CNAP is delivered as a product + service fusion that eliminates the overhead of customer-driven management, detection content tuning, and upgrades that can consume significant operational effort in traditional SIEM deployments. With a fixed, predictable pricing model that is decoupled from data volume and usage, CYDERES CNAP enables organizations to collect and analyze all their security telemetry.
“CNAP brings significant features to enhance and extend the Google Chronicle solution,” says Eric Foster, President of CYDERES. “CNAP customers can easily take advantage of the unparalleled data lake and analytics capability of Chronicle but also get the SIEM capabilities they need and expect, such as operational and compliance reports, dashboards, additional detection and correlation capabilities including support for Sigma rules, and incident and case management including out-of-the-box integration with all popular ticketing and SOAR platforms.”
Benefits to the customer include up to 500% total cost of ownership advantage over traditional consumption-based SIEM solutions, enhanced advanced threat detection, improved return on security investment, higher analyst productivity, and easy expansion to managed services including CYDERES Managed Detection and Response (MDR).
Based on an organization’s preference, CYDERES CNAP provides organizations the opportunity to either modernize or augment their current SIEM with a turnkey solution that has the flexibility to power an in-house security operations team, to enable a third party managed service, or with CYDERES providing end-to-end Managed Detection and Response (MDR) or 24x7x365 SOC-as-a-Service via the award-winning CYDERES Cyber Defense Centers in Kansas City, Missouri and Rogers, Arkansas.
Key features of the Cloud Native Analytics Platform include:
- Operational and compliance reporting, including custom reports
- Compliance and SOC dashboards
- Enhanced detection and correlation capabilities including support for Sigma rules
- Security workflow and select SOAR automatic actions
- Out of the box integration with third party ticketing and SOAR platforms, including ServiceNow, JIRA, RSA Archer, Onspring, Demisto, Phantom, and Swimlane.
- Support for extended SIEM data sources and use cases, including IOT, Cloud, and DPHM.
- CYDERES managed and hosted integrations to enable easy data flows from virtually any SaaS or cloud platform, including support for AWS and Azure as well as GCP.
- Native integration and bi-directional support for legacy SIEM platforms such as Splunk, Arcsight, Qradar and Logrythym, for organizations that wish to either extend their current SIEM’s capabilities and/or offload high-volume telemetry from their current platform.
CYDERES CNAP is built on Google Cloud Platform (GCP) infrastructure for unmatched performance, scale, availability as well as trust and compliance. CNAP fully leverages Chronicle’s unified security data model, high performance search/ingest APIs, and advanced rules engine (YARA-L). This combination of GCP, Chronicle, and CNAP represent a purpose-built security data lake with SIEM capabilities, supporting unlimited ingestion of an organization’s enterprise security telemetry at a low, fixed, per-employee price. All security telemetry is retained in an instantly accessible, sub-second-searchable state for a full 12 months by default. The platform can also store data cost-effectively for even longer-term retention requirements by leveraging native CNAP support for GCP Nearline, Coldline, and Archive storage.
With a rich library of pre-built data source connectors and SOC-ready content including correlation rules, operational and compliance dashboards, and pre-defined triage workflows, CNAP enables organizations to modernize their security with a cost-effective solution for storing and analyzing all enterprise security telemetry and making it useful for detecting, hunting, and responding to both current and emerging security threats.
About Fishtech Group
Born in the cloud, Fishtech Group is the leading current-generation service provider enabling secure business transformation. Our experienced cybersecurity professionals plan, produce, and implement innovative solutions that ensure security and success. We make businesses more secure while increasing productivity and visibility. We focus on threats so you can focus on your business.
Fishtech Group includes the Security-as-a-Service division CYDERES and the security analytics firm Haystax of McLean, VA. Fishtech venture partners include Perch Security of Tampa, FL, and Foresite of Overland Park, KS. Visit https://fishtech.group/ or contact us at info@fishtech.group.
Identity Governance: The Starting Point (Video)
As the global business landscape continues to shift, organizations are learning what it takes to secure and scale a remote workforce efficiently. As this “new normal” emerges, a robust identity program must align with an organization’s compliance objectives and combine to form a robust solution set that enables business growth.
In order to address the related financial, legal, operational, and reputational risks, Identity Governance combines a prescriptive blueprint for effectively identifying and converging the foundational pillars of IAM with a right-sized and resilient GRC solution/program. Importantly, this also incorporates a Zero Trust Model of relevant security and technical controls.
As a result, organizations are able to prioritize, manage, and mitigate cyber risks that align with their business goals and objectives.
In part two of our ongoing webcast series Why Identity Governance Really Matters Fishtech Group experts describe best practices and winning solutions that we are architecting for customers every day.
Missed Part 1? Catch the full replay on demand.
Virtually Tour the Fishtech Campus
Adapt and overcome.
Two watchwords we are all learning to live by in this unique season of crisis. During this time we continue to aid our clients with all manner of cybersecurity and business continuity challenges 24 hours a day / 7 days a week.
Our virtual teams are standing by to deliver assessments, workshops, and demos while helping organizations currently dealing with security incidents of all kinds. Typically we are glad to welcome enterprises, small businesses, and schools alike to tour our Fishtech Group campus, but due to the ongoing situation have limited access to necessary personnel only.
Instead, we invite you to tour our Fishtech Headquarters and 24/7 Cyber Defense Center via these videos below.
Our unwavering commitment remains leading organizations to a more secure future!
Our Unwavering Commitment
Like many of you, we are continuously monitoring the ongoing Coronavirus (COVID-19) situation and want to assure you that our primary focus is always the health and safety of our community, customers, and staff. As we continue to monitor the CDC’s guidance, our thoughts are with those personally affected by this virus and their families.
We remain vigilant to guard the integrity and security of the data, architecture, and systems you’ve placed on our watch 24/7/365 so that you can maintain focus on your business and the care of your own families and staff.
All of Fishtech Group’s divisions operate from a zero-trust architecture, meaning that all of our security controls exist at the user, application and data layers. We do not place any trust in the network layer, and this allows to continue operations uninterrupted.
Our mission remains helping organizations minimize risk, maximize efficiency, and maintain compliance in an increasingly turbulent world, and therefore we have strong disaster recovery and business continuity plans for our own organization. Fishtech was purpose-built to act as a reliable partner for companies in crisis and with every customer interaction we continuously refine protocols to serve you better.
Fishtech Group teams throughout the country are flexible, informed, layered, and able to collaborate to assist you from any location. We are accustomed to virtual work situations and are well equipped to help you with any challenges you may face with your own teams.
With the safety of your staff and ours in mind, we have limited our domestic travel and have shifted our live events to webcasts only. In addition, we are taking increased precautions at each of physical locations in Kansas City, MO, Northwest Arkansas, and McLean, VA in addition to emphasizing our existing policies. These include optional work from home for all employees, with a requirement to do so for those who feel ill or have been exposed in any way.
Thank you for your loyalty and reliance on all of us at Fishtech Group. Please reach out to us directly with any questions and let us know how we can continue to honor the trust you have placed in us. Our unwavering commitment is to serve you and your business throughout this difficult time and beyond.
To a secure future,
Fishtech Group
Haystax Strengthens Executive and Insider-Threat Teams
Contact: Jennie Hanna, jennie.hanna@fishtech.group
Kansas City, MO (February 4th, 2020) – Fishtech Group is pleased to welcome two widely respected cybersecurity industry leaders to the Haystax team.
Brett Wilson has joined Haystax as General Manager. In this critical new role he is responsible for leading the Haystax business unit of Fishtech Group, and is focused on developing, taking to market and operationalizing innovative approaches that help organizations identify threats and manage risks using the world-class Haystax platform. Brett is part of Fishtech’s Executive Team and reports directly to Fishtech Group founder and CEO Gary Fish.
David Sanders joins Haystax as Director of Insider Threat Operations, responsible for deploying the Haystax Insider Threat Mitigation Suite to the company’s enterprise and public-sector clients and supporting the optimization of their existing insider threat programs. Dave reports to Haystax’s Vice President of Customer Success, Susan Oliver.
“Brett and Dave are accomplished cybersecurity executives who bring a wealth of industry knowledge and experience to our Haystax business unit,” said Gary Fish. “With their addition to the team, we are positioned to expand and accelerate adoption of Haystax’s award-winning insider threat and physical security software platform to enterprise, federal and state government public safety and education clients.”
Brett has over 25 years of technology industry experience creating, marketing, selling and supporting information security software and risk management solutions. He has held various leadership roles at Symantec, Trustwave and CYREN. Most recently, Brett was COO of enSilo, a recognized leader and innovator in the advanced endpoint security market that was recently acquired by Fortinet. “Haystax is an innovator in the application of advanced data science and AI in solving difficult cyber and physical security problems,” said Brett. “I am excited to lead Haystax’s efforts to help enterprise and government clients manage their risks, and to deliver our solutions to a wider market.”
Dave has two decades of experience in program and project management, software development and database design, including eight years as a trailblazer in the development and implementation of advanced insider threat mitigation programs. Most recently, he designed and managed the insider threat program at Harris Corporation, now L3Harris Technologies. Previously, Dave served on the U.S. government’s National Insider Threat Task Force (NITTF). “I am impressed with Haystax’s pioneering, patented approach to evaluating behavioral and cyber indicators of insider risk, which is both game-changing and unique,” he said.
Fishtech CRO Pete Shah added: “In our pursuit of seamlessly integrating Haystax as a business unit of Fishtech Group, we are confident that Brett and Dave will have an immediate, accretive impact on our customers and partners, ensuring Haystax continues to deliver operational mission success to the dedicated safety and security professionals who are responsible every day for managing risk to people, facilities, systems and information.”
Both Brett and Dave will be based at the Fishtech Group/Haystax office in McLean, VA.
About Fishtech Group
Born in the cloud, Fishtech Group is the leading current-generation service provider enabling secure business transformation. Our experienced cybersecurity professionals plan, produce, and implement innovative solutions that ensure security and success. We make businesses more secure while increasing productivity and visibility. We focus on threats so you can focus on your business.
Fishtech Group includes the Security-as-a-Service provider CYDERES and the security analytics platform provider Haystax of McLean, VA. Fishtech venture partners include Perch Security of Tampa, FL, and Foresite of Overland Park, KS. For more information, visit our website at https://fishtech.group/ or email us at connect@fishtech.group.
On State Actors and Cyber Readiness
Update 12/16/20: Although this article was written in January, the advice herein has continued to resonate as we continue to tackle the many challenges of this year. The recent news of advanced cyber attacks have prompted many to investigate their overall cyber readiness or lack thereof, a very worthwhile exercise. Don’t go it alone – leverage Fishtech’s industry pioneer expertise, decades of experience, and what’s actually working in our customers’ environments to mature your security program and scale your business instead of being consumed fighting its threats.
For better or worse, the world of cybersecurity is increasingly intertwined with the current events of the day. As cyber criminals continue to evolve in the digital era, we will continue to see an increase in the frequency and sophistication of cyber-attacks.
In the last five years alone, there has been a 67% increase in security breaches, with a growing portion of these breaches coming from state actors. Of course, this is why we at Fishtech are so passionate about what we do. The genuinely painstaking but necessary work of cyber experts grows continuously larger in global importance every single day.
In light of several recent international incidents, most notably the recent military action in Iran, we have seen a flood of articles detailing serious cyber-attacks that will be coming our way from various state actors. We’ve received several specific questions about what to do about the potential escalation in cyber conflict.
The news cycle should not be your alert to put the proper practices into place to protect your business.
If it is, that doesn’t make you a bad business owner. At least you care enough to worry about your organization’s security maturity at all! The only thing is, these attacks aren’t new. Many state sponsored actors are operating at various levels of sophistication and have been orchestrating cyber-attacks for years.
While particular threats may be more severe than others, cyber readiness demands constant vigilance. The 24-hour news cycle will ebb and flow with reports of what could be the beginning of an even greater level of intense cyber warfare with devastating effects. Vigilance is key, but shouldn’t similarly ebb and flow, but rather maintain a constant state.
To analyze further, let’s look at some historical context: As Digital Shadow’s Rick Holland recalls, in October 2012, roughly two months after the Saudi Aramco Shamoon wiper attack, then-Secretary of Defense, Leon Panetta, gave a now-famous speech where he warned about the potential for a “cyber Pearl Harbor.” Do we have a historical reference for an actual “cyber Pearl Harbor”? Not exactly.
At the same time, we have been monitoring fresh intelligence that SOC’s have been experiencing an escalation in spear phishing, scans against companies targeting VPN vulnerabilities, and a myriad of other attack vectors in late 2019 / early 2020.
This isn’t reserved for a single state actor, but multiple at various levels of sophistication. Don’t read this wrong, there have been some clear retaliatory attacks after incidents occur, but nothing so unusual to suggest a “new” devastating cyber weapon has emerged on the scene.
All that being said, no matter your stance on the will-they won’t-they chatter, the threat risks you are experiencing are still greater than zero. Questions around availability, cloud security, and other potential vulnerabilities are very legitimate.
Therefore, the leader who is rightfully concerned about risk (continuously analyzing combinations of threat likelihood, vulnerability, and consequence) needs to be fully prepared for very unique situations and take preventive steps where possible.
So, what’s next?
Our constant focus: helping our clients build out and maintain a set of best practices for the modern enterprise. Whether it’s state actors or individual attackers, the fundamentals of modern cybersecurity still apply.
For example, as Gartner has clearly stated for years, robust detection and response capabilities are at the top of the list. Organizations of all sizes need to make sure the people, process, and technology are in place to respond to any potential attacks. With talent in short supply, and the costs of building an in-house SOC increasing, finding efficient ways to detect, respond, and even proactively threat hunt around the clock can be very difficult.
In addition to fundamentals, we recommend regular penetration testing, vulnerability management, and making sure you have a cyber readiness plan and team in place equipped to deal with every aspect of a security incident, because every second counts.
All of this can help build out a more mature cybersecurity posture moving forward and is not dependent on a single state actor or malicious insider.
Truthfully, you most likely didn’t start your business to be distracted by cyber threats. Out of necessity, many enterprises are having to use more and more resources to keep themselves afloat in this ever-swirling sea of risk.
We believe organizations should be able to spend that precious time and resource doing what they do best however possible. Whether it’s building better automobiles, saving the planet, scaling restaurant franchises, or caring for patients – we want to help.
Fishtech was built from the ground up to alleviate these worries for modern day organizations.
Your focus should be on what you do best: growing your business and running your organization to perform at its’ peak no matter what the news cycle.
These threats aren’t going away – recall the 67% of security breaches in the last five years. One way or another, a solution needs to be found. Are you in this alone? Or, are you ready to work with experts that can make sense of the chaos and use real data with your unique business situation to inform an overarching, scalable, and mature cybersecurity program.
If you are interested in learning more about helping your organization take its’ cyber readiness to the next level, fill out the form below to get connected with one of our expert consultants.