Black Friday / Cyber Monday Safety Tips
November 25, 2020Cybersecurity Insights
The Black Friday phenomenon has grown exponentially over the years. So much so that new big deal days like Cyber Monday have been tacked on to extend the shopping season. Not only that, businesses have started advertising Black Friday deals at the beginning of November, if not outright start the Black Friday sales around the first of the month.
This year, Black Friday has been even more pervasive in the Year of the Quarantine, with new cyber deals popping up every day, and discount codes urging you to “STAYINSIDE”. In what is sure to be a more cyber-heavy shopping year, it is more important than ever to take steps to ensure your money and your data stay safe this holiday season.
In today’s blog post, we’re putting together a few tips to help you protect yourself as you shop from the comfort of your couch. Here are a few Black Friday / Cyber Monday Safety Tips:
1) DON’T USE DEBIT CARDS
Using a debit card allows cyber criminals direct access to your bank accounts. Using payment options with added layers of protection is key to reduce your risk while you shop. Try using a credit card or a third party like PayPal or Venmo.
2) DON’T CLICK ON LINKS OR OPEN ATTACHMENTS IN EMAILS
Many cyber criminals are using the flood of Black Friday emails from retailers to send their own copycat versions with malicious links. Beware of links and attachments in the emails you receive. Hovering over links can help show you where exactly each link is sending you to.
3) DON’T SHOP ON PUBLIC WIFI
Make sure you are only shopping on a secure connection. Shopping online requires you divulge sensitive information, like credit card numbers, addresses, and more. You don’t want this information visible to outside eyes. When you are shopping online, make sure you are on a private network, or are using your cellular data plan to stay secure.
4) USE A VARIETY OF PASSWORDS
Many online retailers require you to create an account to purchase items, which includes creating a password. It may be easier to use the same password everywhere, but should that retailer be breached in the future, many of your other accounts are now susceptible. Use a variety of passwords to mitigate your overall risk.
5) ENSURE YOUR SOFTWARE IS UP TO DATE
Before shopping til you drop, make sure your device’s software is up to date. From your operating system to your web browser to your password manager and beyond, take some time to ensure you have the latest versions for security’s sake. Outdated systems are often littered with vulnerabilities, so you’ll want to fully update to block cyber criminals from gaining access.
6) ENABLE 2-STEP VERIFICATION
We’ve recently covered how to achieve better security for your organization through 2-step or multi-factor authentication, but many online retailers give individuals the option to ensure all logins (and even final order submissions) are secured through confirmation via a secondary device. Sending an authorization code to your phone or email may be a momentary inconvenience but compared to dealing with stolen credentials is a very worthwhile use of time.
With so much excitement surrounding Black Friday, Cyber Monday, and the holiday season in general, it can become easy to overlook the basic tenants of cyber safety. Follow these tips, and use common sense to stay safe as you shop. Have a happy Thanksgiving, and stay safe this weekend!
DDoS Extortion (CYDERES Technical Blog Series)
November 24, 2020Cybersecurity Insights
After years of ransomware wreaking havoc on victims worldwide, threat actors doubled down with their extortion tactics earlier this year by introducing a new technique. This was previously described in the “2020: Not Your Father’s Ransomware” CYDERES technical blog post. It’s a relatively simple concept, with an innovative and ingenious spin on the traditional ransomware attack. Rather than just encrypting a victim’s sensitive data, the operators behind the attacks added the additional step of exfiltrating that sensitive data and threatening to leak the data if the requested ransom is not met. In the past, victims with access to system backups might be able to sneak by without paying the ransom. However, now they may have to consider paying because they are faced with the threat of their data being leaked. The risk of public disclosure and potential brand damage being leveraged in these attacks can be very lucrative for the operators behind these attacks.
While the concept of double extortion might have been the first significant twist relating to ransomware we would come across the year; it would unfortunately not be the last. Adversaries have proven that they are opportunistic in nature and will exploit any avenue they can. COVID-19, perhaps being the most significant opportunity of all, has drastically impacted the cyber landscape. The shift to remote working has opened up a new assortment of security vulnerabilities and has left users increasingly vulnerable to phishing emails and malware-involved attacks as they perform work-related tasks on their home networks, which often have minimal security measures in place.
The shift instigated by COVID-19, along with the opportunistic nature of malicious operators and other uncertainties in today’s world, has had a damaging impact on the cyber landscape worldwide. Research conducted by Check Point concluded that during the third quarter of 2020, there was a 50% increase in the daily average of ransomware attacks when compared to the first half of 2020. Additionally, the number of ransomware attacks that have plagued the United States has approximately doubled in the third quarter of 2020, making it the most targeted country for ransomware attacks. [source]
Figure 1: Check Point Research showcasing the rise of ransomware incidents
Now it is time to introduce the tried-and-true concept of distributed denial of service, or DDoS, extortion. The idea of this form of digital extortion is relatively straight-forward; if the victim gives the adversary what they request, then the adversary will not attack the victim. Victims will often receive communication from the adversaries threatening to unleash a wrath of junk traffic in a DDoS attack if the victim does not supply the adversaries with the ransom amount they request.
In a recent example of DDoS extortion, adversaries claiming to be affiliated with the Lazarus Group sent an extortion letter to Travelex in which they demanded 20 bitcoins, or approximately $200,000 at the time, and stated that the ransom would increase by 10 bitcoins every day that elapsed after the initial deadline. Travelex did not pay the ransom and instead chose to face the DDoS attack. The DDoS attack did not prove to be effective and is indicative of its spotty effectiveness. [source]
Similar to exfiltration, DDoS extortion on its own is nothing new or fancy. However, it is a means to add some extra leverage when demanding a ransom payment, which is all an adversary needs. If an organization is not willing to or does not need to pay to decrypt their data, they will perhaps pay to prevent a DDoS attack that could result in service downtime. Not to mention the downtime organizations may face from other consequences, such as further impacting their brand reputation.
At the beginning of October 2020, the security community observed one of the first attacks that leveraged the technique of combining ransomware and the threat of a DDoS attack. When negotiations stalled in a SunCrypt ransomware attack, the operators and its affiliates initiated a DDoS attack against the victim’s website. Upon logging back into the ransomware’s Tor payment site where the negotiations were being conducted, the victim was provided with an explanation that SunCrypt was responsible for the DDoS and threatened to continue the attack if negotiations did not resume. In this scenario, the SunCrypt operator’s use of this tactic to force negotiations was successful, as it ultimately led to the victim paying the demanded ransom. This technique was especially effective because the victim was a smaller organization. The combination of data theft, the threat of a data breach, a lack of access to encrypted files, and a DDoS attack could have completely caused them to shut down. [source]
Figure 2: Communication between SunCrypt operators and their victim
The effectiveness of this technique boils down to simple principles. First, the adversaries must present a threat that introduces unacceptable consequences. It must be drastic because if it is not, no victim is going to pay the demanded ransom. In the case of DDoS extortion, it is the system and resource downtime, along with the consequences that come with it, that are unacceptable. Secondly, adversaries are going to have a much better shot of being successful if they can force the victim to react with emotion rather than logic. DDoS extortion attempts to accomplish this by setting deadlines, such as threatening to continue to increase the ransom demand as more and more time passes. This is more likely to elicit an emotional response from the victim because they might not have the opportunity to think rationally or even engage law enforcement.
While the introduction of data exfiltration and DDoS extortion makes preventative efforts less cut-and-dry, there are still many measures and best practices that can and should be implemented to help mitigate these threats. Best practices for mitigating ransomware include network segmentation, the principle of least privilege, anti-malware software, up-to-date systems, and most importantly, backup solutions that are not only implemented but also practiced to ensure a smooth recovery. Besides using unique, complex passwords, enabling multi-factor authentication (MFA) where possible, and regularly applying security updates and patches to maintain a strong network security posture, knowing what a DDoS attack looks like and having a plan to react to it are important steps to take for mitigation.
Now that there are use cases and evidence to suggest that both the threat of data exfiltration and DDoS extortion are effective when it comes to providing additional leverage to persuade the victim to pay the ransom, it will likely be increasingly adopted. Not only that, but these tactics and techniques will continue to evolve in an attempt to stay one step ahead of defensive measures that could stand in the way of raking in a profit. Coupled with the additional challenges of a rushed transition to a remote workforce and everything else that has come along with the COVID-19 pandemic, some companies have been left in a vulnerable position. Combating the ever-changing cybersecurity threat landscape will require an extraordinary amount of creativity, perseverance, and collaboration from cyber professionals, business leaders, and organizations worldwide.
CYDERES is primed to help with threats like ransomware and can help organizations in situations like those detailed above. If you are interested in finding out more about how CYDERES can help your organization combat ransomware and beyond, fill out the form below.
Two Essential Tools for Successful Insider Risk Mitigation – Parts 1 & 2
November 19, 2020Cybersecurity Insights
By David Sanders
Part 1
A common question among companies seeking to mitigate the risk of an insider attack is: “What tools should we buy for our mitigation program to be successful?”
Our view is that every effective insider threat program must have two tools. One is a user activity monitoring (UAM) system and the second is artificial intelligence-based analytics software.
It’s important to understand that these tools perform distinctly different functions, and that no single technology will meet the breadth of requirements that UAM and AI analytics do when combined.
UAM is a structured, consistent and continuous collection and reporting process across the whole of an organization at the device level. It helps users identify, assess, decide on responses to and act on specific analysis of employee behaviors.
The purpose of UAM is to gather detailed and substantive activity information (e.g., screen captures, text content, keystrokes, etc.) in the digital realm that may be indicative of an insider threat. UAM tools gather a level of detail not available from other tools, including data loss prevention (DLP), security information and event management (SIEM) and user and entity behavioral analytics (UEBA).
Some UAM tool vendors are adding dashboards and scoring to help focus analytical attention on users generating the most severe and frequent alerts. This is a helpful and positive development within the context of user activity on networks and devices, but it fails to include other data sources not generated by the UAM tool. It is important to remember that UAM systems provide only a limited digital view of the user, which precludes a broader understanding of the user’s full range of activities and behaviors.
Therefore, insider threat programs need to integrate data from across the organization into a separate tool that can perform advanced analytics, with the goal of creating a continuous, comprehensive and accurate assessment of insider behaviors to determine if a trusted individual has conducted or is likely to conduct acts of concern.
The analytical tool must be able to make sense of an abundance of data from technical (i.e., digital) and non-technical sources, and then transform the results into actionable risk intelligence for purposes of detection, risk prioritization and response.
Technical data includes voluminous raw feeds from DLP, web proxies, access management systems, UAM, printers, scanners, email and firewalls. Non-technical data includes information about the individual from multiple departments within the organization, including:
- Human Resources (e.g., role, location, performance, incidents, status, leave patterns, projects, objectives, training records);
- Finance and Accounting (credit card activity, travel and expense records); and
- Security (badging activity, incidents, special access).
Prior to the advent of structured insider risk/threat programs, this broader non-technical data set was rarely integrated and analyzed. That said, there are some tools that were built specifically to conduct this type of multi-source analysis.
Within the CIO or CISO departments, SIEM and UEBA (now known as SIEM 2.0) are used predominantly for this purpose. Without question, the strengths of these two classes of tools are their ability to connect to multiple data sources (i.e., ingest, format, correlate and process data); search and report; and apply advanced analytical processes (e.g., rules, machine learning and other artificial intelligence techniques) to generate alerts.
However, SIEM/UEBA tools are not good at generating actionable risk scores, which are vital to identifying insider threats in a proactive, even predictive, manner. There are several reasons for this:
- Scoring is simplistic – adding scores together, sometimes applying a multiplier or adding a very large value when a specific high-threat event occurs to move users to the top of the scoring list;
- The tools do not effectively score non-technical behaviors, but rather create watch lists with the information; and
- Scoring models are not built specifically for the insider threat domain, but rather relate to specific use cases such as data exfiltration and attempted unauthorized access, which can often be ‘explained away’ as a product of non-malicious and non-negligent activity.
With UAM and SIEM/UEBA tools, then, organizations have abundant alerts but lack an effective scoring capability to identify insiders whose behaviors indicate that they have conducted or are likely to conduct acts of concern.
So what is the best analytical tool to make sense of the volumes of alerts and behavioral indicators that can be found buried in all that technical and non-technical data? At Haystax, we believe in the power of a probabilistic model known as a Bayesian Inference Network, or BayesNet.
BayesNets are a place to capture the knowledge and insights of domain experts and then apply data as evidence to support this or that belief. They are ideally suited to situations where the problems are complex and don’t lend themselves to black-or-white binary answers, and where the data is sparse, noisy or even non-existent.
The Bayesian model at the core of our Insider Threat Mitigation Suite was purpose-built to assess the probability that a user’s behaviors indicate potential or actual insider risk. The model is the single environment where all of the technical and non-technical data and alerts generated from UAM and SIEM/UEBA systems can be applied and effectively evaluated, which is why we call it a ‘whole-person’ model. If a customer does not have a SIEM/UEBA system already in place, the Haystax Insider Threat Mitigation Suite can fulfill many of the data integration and analysis functions in its place.

The screen image above represents a portion of the Haystax whole-person insider threat model. Ingested and processed data can be applied to any model node. The impact of each new piece of evidence is determined by the strength and frequency of the event and probability attributes of how one node in the model affects another.
These nodes and their probabilities were developed with input from experts in the fields of behavioral psychology, security, counterintelligence, human resources, investigations and analytics. The result is a detailed yet understandable model that continuously assesses the probability that an insider has committed an adverse act or has exhibited concerning behaviors, and then produces a risk score on a dashboard in the Haystax user interface that allows decision-makers to proactively mitigate their highest-priority insider threats.
In Part 2 of this post we will compare and contrast how data-driven UAM and SIEM/UEBA solutions detect insider threats versus how the model-driven Haystax solution does it.
Part 2
In Part 1 of this post we explored the basic characteristics of user activity monitoring (UAM), security information and event management (SIEM), user and entity behavioral analytics (UEBA) and artificial intelligence-based analytics software systems.
In this part we will compare and contrast how data-driven UAM and SIEM/UEBA solutions detect insider threats versus how the model-driven Haystax solution does it.
For illustration purposes, let’s consider a company with 10,000 trusted insiders that has the following circumstances:
- 500,000 files per week are copied to removable media by 2,500 employees
- 50,000 files per week are being sent outside the company via email
- 100,000 DLP alerts per week for files being copied to removable media
- 10,000 DLP alerts for email
- 500,000 web page visits per week
- 100,000 files downloaded from websites
- 7,500 files uploaded to websites
The above assumptions are reasonable if there are few or no controls on the use of removable media and on sending files via email. The number of alerts generated would require a significant effort to review in a timely manner; therefore, there needs to be effective threat scoring to point the analysts to the insiders that pose the greatest threat to the organization.
To contrast the differences of how SIEM/UEBA solutions develop threat scores versus Haystax, and the effectiveness of each approach, we will evaluate three user behavior scenarios:
- User A has contextual, technical and non-technical behaviors;
- User B has contextual and technical behaviors; and
- User C has contextual and non-technical behaviors.
The scenarios and resulting scores are presented below.

User A has both cyber and non-cyber behaviors that should be considered in the overall threat analysis. The SIEM/UEBA score, on a relative scale of 0-100, is low. Scoring assumptions for the SIEM/UEBA are:
- Non-cyber behaviors and contextual data did not impact the score;
- The non-productive web browsing has low impact because it is not data exfiltration; and
- Sending files via email has low impact because the volume is low.
The Bayesian Inference Network (aka BayesNet) probabilities consider all of the activity, resulting in higher threat probabilities. The behaviors of User A could be indicative of many things – disengagement from the organization, unfamiliarity with company policy or attempts to test controls and monitoring. Identifying the increased threat level allows for further investigation (perhaps using the UAM tool) and proactive risk mitigation.
User B has contextual and technical behaviors and the SIEM/UEBA score is high, on a relative scale of 0-100. Scoring assumptions for the SIEM/UEBA are:
- The cyber behaviors are scored high due to the large volumes of data being sent outside the network; and
- The contextual data has no impact on the score.
The BayesNet probabilities consider all of the activity, resulting in higher threat probabilities. Specifically, the “Conducts Potential Insider Threat Activities” is high due to the data exfiltration. But the overall “Is Insider Threat Concern” is lower because it is impacted by the “Exhibits Concerning Characteristics,” which is lower due to the contextual data (e.g., position as recruiter, longevity with company, absence of other negative behaviors to increase the score). The behaviors of User B are likely that of an employee doing their job – sending company information to prospective employees.
User C has contextual and non-technical behaviors and the SIEM/UEBA score is zero, due to the absence of technical behaviors and the lack of scoring non-technical behaviors.
The BayesNet probability scoring indicates a low probability of “Conducts Potential Insider Threat Activities” due to the attempted access behaviors, and a medium probability of “Exhibits Concerning Characteristics” due to the access to critical data, attempted access, performance review and being a relatively new employee. User C does not appear to be a threat based on this information, but these behaviors should be retained and considered in the light of future behaviors.
These use cases demonstrate that insider threat programs should implement both UAM and advanced analytics. The UAM tools provide necessary details about users’ activities on computers and laptops, but do not contain all the data required to detect insider threat activity.
A broader set of data, usually at a higher level, needs to be integrated into and effectively analyzed by an advanced tool that can effectively consider both technical and non-technical indicators. The Haystax Insider Threat Mitigation Suite employs just such a tool: a BayesNet that effectively and consistently evaluates both of these behaviors, thus developing a picture of the whole person – and any early indications of insider risk.
# # #
Note: A former high-flying corporate executive suffers a series of personal and professional setbacks and gradually develops into an insider threat. Find out how Haystax would have used probabilistic analysis and technical/non-technical data to discover him prior to his massive theft of intellectual property, in To Catch an IP Thief.
Can You Achieve Better Security with Just a *Click*?
November 10, 2020Cybersecurity Insights
Cybersecurity can be daunting.
How many acronyms and buzzwords can there possibly be within one industry? ZTNA, SaaS, SASE, the list goes on. Where do you start when you’re wanting to secure your business? Today, we’re keeping it as simple and practical as possible, because honestly, sometimes a single step can make huge strides for an organization’s cybersecurity.
Today, we’re talking about multi-factor authentication.
Multi-factor authentication is under the umbrella of Identity and Access Management, or IAM, but forget all of that for a second. We said we’re keeping this simple, right? We’re just focusing on how one or two clicks can improve your security posture as you look to start building out a cybersecurity program that can handle the most advanced threats.
Everyone is used to the traditional way of securing your applications online. Submit your correct username and password, and you’re off to the races. Unfortunately, this approach is quickly becoming outdated as more and more sophisticated attackers find ways to break through this minimal defense.
In a presentation at the recent RSA Security Conference, Microsoft’s Director of Identity Security, Alex Weinert, said 1.2 million Microsoft accounts were compromised in January 2020 alone. Of those compromised accounts, 99.9% were not using MFA.
With multi-factor authentication, the goal is to add an extra layer of defense so that even if malicious attackers crack your password, they do not gain immediate access to your applications and information.
So, what does that look like in practice?
*Click*
Seriously.
It can be as simple as a click or two to add a much-needed extra layer of defense to your organization.
For example, you want access to a cloud application your organization utilizes. Using a multi-factor authentication approach, you would first enter your username and your password. Upon the correct entry of your credentials, a notification would be sent to your personal phone asking if you just logged in. All it takes is a *click* confirming that it was you. Upon this second step, you would then be granted access to your cloud application.
You can see how this can be a deterrent for potential attackers. If they don’t have access to your phone, they don’t have access to your applications.
Now, don’t get us wrong, this isn’t a one and done way to fully protect your organization. Identity and Access Management has many pillars that increase in complexity to further protect your organization to ensure there are even fewer chances that your applications and information will not be breached. As a start, check out our video on the pillars of IAM.
But truly, diving down that rabbit hole is a conversation for another time. The point is that multi-factor authentication is an easy way to get started down the path of a more secure future for your organization.
See? Cybersecurity doesn’t have to be daunting. Sometimes huge strides forward are just a *click* away.
Interested in learning more about implementing multi-factor authentication within your organization? Fill out the form below to get connected with one of our experts.
(And if you’re really itching to learn more about other forms of authentication RIGHT NOW, check out our blog post on “The Rise of Passwordless Authentication”. Overachiever over here!)
A Day in the Life of a GSOC Analyst (CYDERES Technical Blog Series)
October 22, 2020Cybersecurity Insights
Executive Summary
CYDERES, Cyber Defense and Response, is the security as a service division of Fishtech. This division was created to help organizations with 24/7 security operations through our award-winning managed detection and response offering. This article focuses on the day to day activities of a SOC Analyst.
Thursday Morning
Through the Missouri Innovation Campus I was provided with an opportunity to learn with a position as an intern in the CYDERES SOC. With the help of analysts and other CYDERES resources, I was able to recently apply some of the knowledge I have learned to a recent Bazar loader campaign. On September 24, 2020 I started off my day by grabbing a nitro cold brew from the break room before heading though the man trap that leads into the Security Operations Center. Using face recognition for the first door and my badge for the next, I headed to my desk. Once there, I looked at the Twitter feeds which are kept on the large display and noticed reports regarding a malspam campaign being linked to Bazarloader. Since I was working the abusebox, which is a service offered to clients in which suspicious emails are sent for analysis, I started to research on what the campaign looked like and noting any similarities to previously seen campaigns.
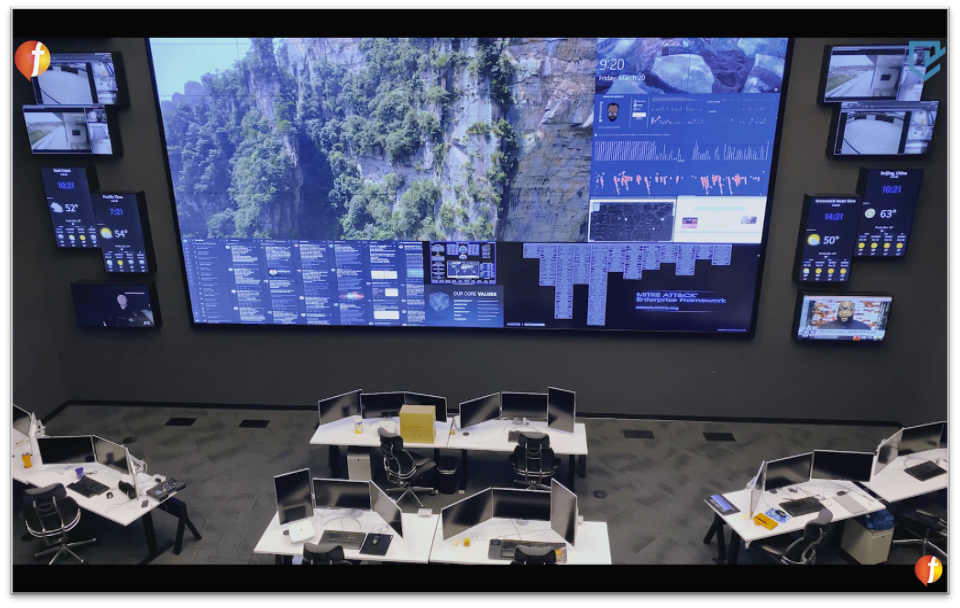
Figure 1: SOC in the Cyber Defense Center
Thursday Afternoon
Later that day, CYDERES received multiple copies of emails being delivered to different customers with a close resemblance to the emails seen that morning. The first item that stands out is they all had the same two subjects, “Re: what time?” and “Re: debit confirmation”. The second item that stood out was that they all had the same sending email address, “mike_warner@parkshorebmw[.]com”, which appears to be a legitimate email for a BMW dealership in Vancouver that was likely compromised or spoofed. While the sender looked reputable, investigating the body of the email showed similar items to previously seen phishing campaigns that lead to credential harvesters.
Figure 2: Sample email 1
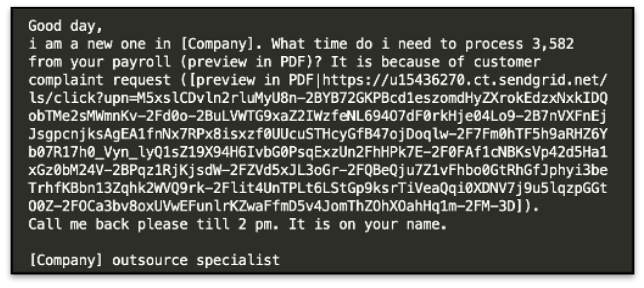
Figure 3: Sample email 2
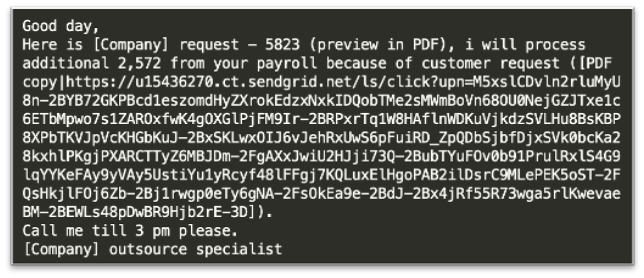
I observed that the emails contained common spear-phishing (Mitre T1566.002) techniques which address the email to the target company, while claiming to be an outsource specialist. The email also contained a sense of urgency by discussing payroll information and setting a time where a reply is needed, then requesting the user download a PDF file.
The link in the email shows it was sent via Sendgrid and contains a masked URL that will redirect to the payload. This follows the trend reported by Brian Krebs on how Sendgrid is commonly used to send out malicious emails to evade detection. The link in the email leads to a Google Document which looks very similar to ones that have been linked to Emotet malspam campaigns.
Figure 4: Screenshot of the requested download pdf
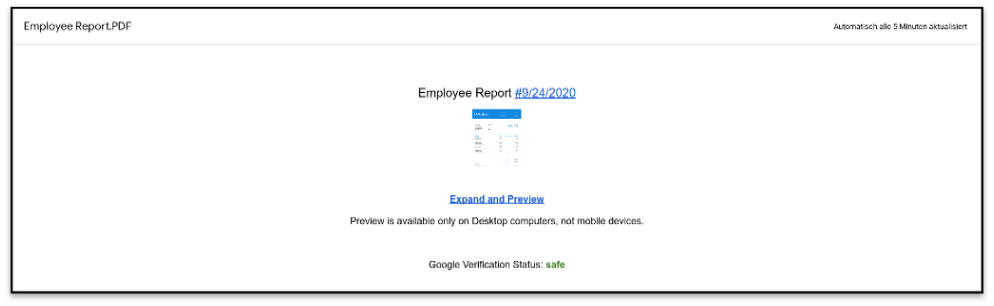 The page contains a message that claims that Google has verified this page and calls it “safe”. However, this is added by the threat actors in an attempt to make the page look legitimate. The page is hosted via Google’s cloud services which means that this document could have been created by anyone, so it should not be trusted for employee information.
The page contains a message that claims that Google has verified this page and calls it “safe”. However, this is added by the threat actors in an attempt to make the page look legitimate. The page is hosted via Google’s cloud services which means that this document could have been created by anyone, so it should not be trusted for employee information.
The link on the page was observed to download an EXE file even though the email and the website claim that the document should have been a PDF file.
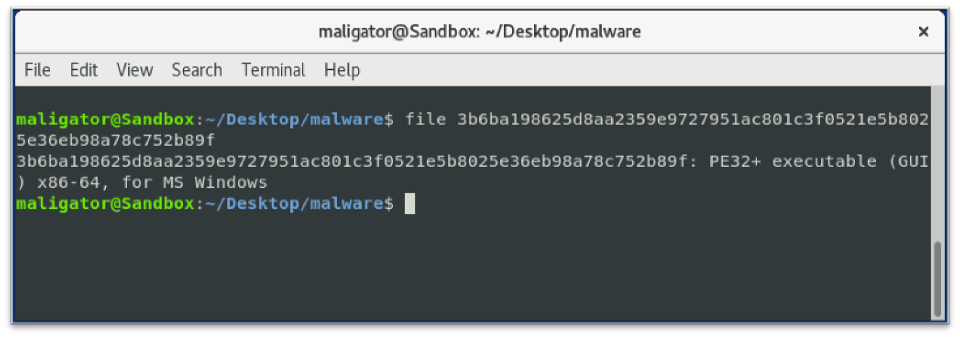
Running the file command shows the following:
Figure 5: File command on suspicious “pdf” file
 The downloaded binary had not yet been identified in Virustotal as malicious. The binary was then detonated in a sandbox environment but did not run in a Windows 10 32-bit environment. Switching to a Windows 10 64-bit sandbox, the sample loaded modules, but then after reading the GUID information it unloaded them. This appeared to be because the sample identified that it was in a VM or that it would not run on Windows 10. This is a common threat actor tactic used to try to avoid analysis which aligns with technique T1497 of the Mitre ATT&CK model.
The downloaded binary had not yet been identified in Virustotal as malicious. The binary was then detonated in a sandbox environment but did not run in a Windows 10 32-bit environment. Switching to a Windows 10 64-bit sandbox, the sample loaded modules, but then after reading the GUID information it unloaded them. This appeared to be because the sample identified that it was in a VM or that it would not run on Windows 10. This is a common threat actor tactic used to try to avoid analysis which aligns with technique T1497 of the Mitre ATT&CK model.
Research on the PDB path from the binary led to a github page with a theory that the binary might run on a Windows 7 VM. The referenced Github page talks in detail on how to escalate privileges in Windows 7. After detonating the sample in a local Windows 7 virtual machine, it was found that the sample was generating domains ending in “.bazar”. Similar to Trickbot, this loader evades detection by abusing the trust of certificate authorities. This loader, however, uses EmerDNS domains for command and control due to the domains being uncensorable. According to the emercoin site:
Because of Emercoin’s secure and distributed blockchain the domain name records are completely decentralized and uncensorable and cannot be altered, revoked or suspended by any authority. Only a record’s owner can modify or transfer it to another owner, and a record’s owner is determined by whoever controls the private key to the associated payment address.
Figure 6: Screencapture of bazar dns domains in Wireshark
Performing OSINT review on the IP address, 92.242.40[.]137, resulted in a tweet by @JAMESWT_MHT listing this IP as “Bazarloader” signed by “Nordkod LLC”:
Figure 7: Tweet listing the ip as bazarloader
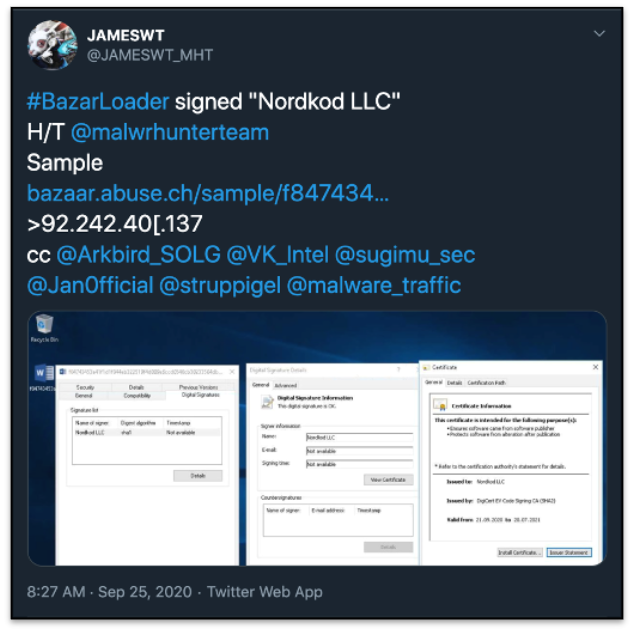
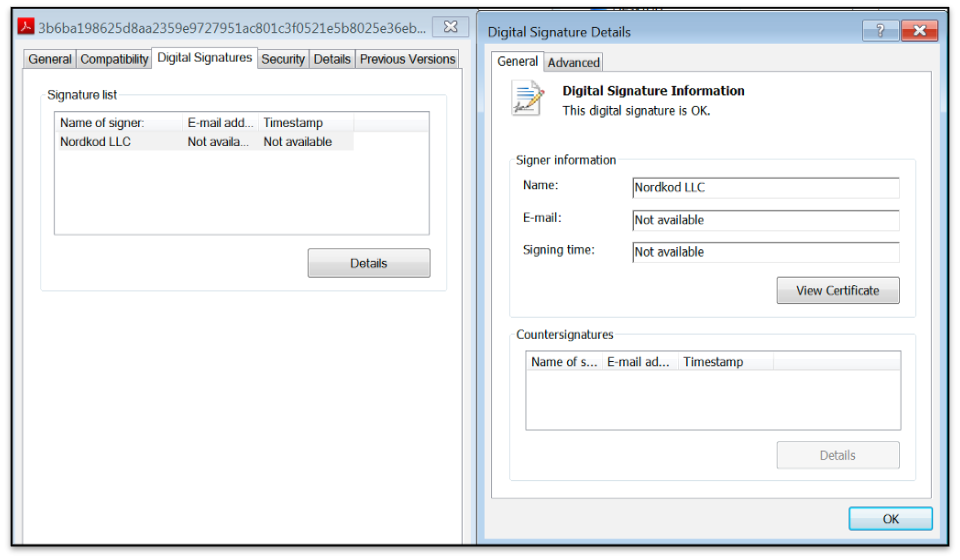
A look at the binary properties show the same signature listed on Twitter:
Figure 8: File signed as Nordkod LLC
The next steps were to follow customer specific playbooks to report and mitigate this campaign for our clients. For one customer, this included quarantining around 100 emails which had reached users but were mostly unread. Leveraging Chronicle, a search was made for any IOCs in the customer’s environment, which resulted in 0 hits. For a detailed analysis of Bazarloader, check out Cybereason’s article titled “A bazar of tricks: following team9’s development cycles”.
Leverage Fishtech’s Expertise
Analysts in the GSOC, Global Security Operations Center, provide 24×7 security monitoring, triage, and investigations across the entire security stack. From abuse box monitoring and human threat hunting to managed deception and network traffic analysis, CYDERES ultimately owns detection of threats in the client’s environment to be a force multiplier for in-house security capabilities. To learn more on GSOC or other services offered by Fishtech, fill out the form below, or check out the drop down menus at the top of the page.
References:
| https://krebsonsecurity.com/2020/08/sendgrid-under-siege-from-hacked-accounts/ |
| https://emercoin.com/en/documentation/blockchain-services/emerdns/emerdns-introduction |
| https://twitter.com/JAMESWT_MHT/status/1309469473833967616 |
| https://github.com/pauldotknopf/WindowsSDK7-Samples/blob/master/com/uac/elevationsample/ElevationManager.cpp |
| https://attack.mitre.org/techniques/T1497/ |
| https://www.cybereason.com/blog/a-bazar-of-tricks-following-team9s-development-cycles |
IOCs
| Phishing Urls: |
| hXXps://redacted[.]sendgrid[.]net/ls/click?upn=M5xslCDvln2rluMyU8n-2BYB72GKPBcd1eszomdHyZXrokEdzxNxkIDQobTMe2sMWmGk0T0fDgb82Scmnu0FhU33GfqxrVpZAf8fN |
| hXXps://docs[.]google[.]com/document/d/e/2PACX-1vSNRlZCfsXuh24McOcs7UlenV3L7e9W6BDiq48hHtm2odtzRVdXYWlU-t7Dryn_7ZqE4RVRuNFSlmqh/pub |
| Hash |
| sha256 3b6ba198625d8aa2359e9727951ac801c3f0521e5b8025e36eb98a78c752b89f |
| sha1 4e783aa0faa4a1a56d9e8b14c83b17f74bb8e31b |
| md5 62265048f49f6f22500f75ea45325603 |
| Bazar Loader’s DGA implementation (snippet) |
| acfhklaehhkn[.]bazar |
| bdehkkbfghkm[.]bazar |
| aegikmagiiko[.]bazar |
| bdfhilbfhhin[.]bazar |
| afggilahigin[.]bazar |
| ccegilceggin[.]bazar |
| bdfijlbfhijn[.]bazar |
| cdfhjlcfhhjn[.]bazar |
| dcghjkdeihjm[.]bazar |
| cdeijlcfgijn[.]bazar |
| dcfgikdehgim[.]bazar |
| cdegjlcfggjn[.]bazar |
| bdfiikbfhiim[.]bazar |
| ceegilcgggin[.]bazar |
| bcehjlbeghjn[.]bazar |
| dfggikdhigim[.]bazar |
| dehijkdgjijm[.]bazar |
| cdehilcfghin[.]bazar |
| afgiilahiiin[.]bazar |
| bdggimbfigio[.]bazar |
| bceijlbegijn[.]bazar |
| IP Connections |
| 193.183.98.66 |
| 51.254.25.115 |
| 95.174.65.241 |
| 192.71.245.208 |
| 94.16.114.254 |
| 151.80.222.79 |
| 195.10.195.195 |
| 176.126.70.119 |
| 92.242.40.137 |
ZTNA, SASE, Remote Work, and More with Dan Thormodsgaard, Co-Founder and Chief Technology Officer
October 15, 2020Cybersecurity Insights
The theme for the second full week of Cybersecurity Awareness Month has been “Securing Devices at Home and Work” which has taken on such an unprecedented importance in 2020. We recently caught up with Fishtech Group’s Co-Founder and Chief Technology Officer Dan Thormodsgaard to ask him a few questions on the state of cybersecurity after a tumultuous year. We go further into how he sees our industry adapting to what’s to come in 2021 and beyond and how it all relates organizations securing home and work devices. Along the way, we hit on newly-emerging hot topics in our industry like ZTNA, SASE, and Infrastructure-as-Code, and dive into Fishtech practice areas like CRC and IAM. Without further delay, here is our interview with Dan Thormodsgaard.
Is ZTNA Just Another Buzzword?
Is ZTNA just another buzzword? We don’t think so. Zero Trust Network Access can bring a lot of added security to your access controls as you move away from IP-based access controls to more application- and identity-based access controls.
What is SASE?
SASE, or Secure Access Service Edge, encompasses not only ZTNA, but the security stack as well. Dan elaborates on another recent hot topic in our industry.
Accelerate Your Business with Cyber Risk & Compliance
Cyber Risk and Compliance, or CRC, is a Fishtech practice that is based around helping you meet your compliance objectives that can ultimately win you new contracts, thus accelerating your business, while simultaneously working to keep you more secure.
The Power of Infrastructure-as-Code
Infrastructure-as-Code is the future of the modern enterprise. With the mass adoption of the cloud, Infrastructure-as-Code will become important to achieve efficiencies in your business to allow you to thrive in ways that were not possible in data-center-centric environments.
Identity & Access Management Priorities for 2021 & Beyond
Earlier this year, as remote work started to accelerate, access management was a primary focus for many organizations, but what should IAM priorities look like for 2021 and beyond? Dan talks about the four pillars of IAM and explains where we should go from here.
Best Practices for Insider Threat Visibility
There are many factors at play when you start talking about successful insider threat programs. It is important to have a great foundational layer of controls from many other practice areas to set your organization up for success. Dan explains some best practices for getting these controls up and running to make sure you are able to more easily and successfully implement an insider threat program for your business.
Biggest Cyber Challenge of 2020
2020 showed a lot of cracks in many organizations with regard to business continuity and their abilities to adequately adjust to work from home environments. Dan talks about a couple specific examples he saw in 2020 of how organizations adjusted to the unpredictability of this year, and why cloud adoption is so important.
The Importance of Validating Technology
Fishtech has built out a state of the art lab, not only for cloud-based environments, but for on-premise environments as well. Dan talks about our philosophy on validating technology and the steps we take to make sure we’re providing the right solution the first time.
Building a Flexible Cloud Architecture
Fishtech was lucky to be able to start from the ground up five years ago with decades of experience in our back pocket to create a flexible cloud environment that we could proudly show as a model for our customers of how to operate in a native cloud environment. Dan talks about how this was a huge help during the unpredictability of 2020.
Up-and-Coming Technologies
To round out our interview with Dan Thormodsgaard, we’re talking about the up-and-coming technologies that are getting his attention, most notably surrounding SASE.
Ready to discuss strategies for 2021? Fill out the form below to be connected with one of our experts.
Third-Party Risk Mitigation – If You Connect It, Protect It. #BeCyberSmart
October 8, 2020Cybersecurity Insights
In the modern business landscape, delivering products and services requires a network of partners and suppliers who will inevitably receive and handle sensitive information. Unfortunately, this increased reliance on third-party operators has led to an increased amount of breaches that originate from said third parties.
During this first week of Cybersecurity Awareness Month, in which we are focusing on the overall theme of “If You Connect It, Protect It”, we wanted to focus on ways you can protect your organization as you continue to connect with third parties. It is important to reduce your overall risk so that you can continue to grow your business with your network of partners and suppliers in a safe and efficient manner.
Third-Party Risk Mitigation with Zero Trust Network Access, or ZTNA
There are many ways to mitigate risks that emerge from connections with third parties. Earlier this week, our Chief Technology Officer and Co-Founder Dan Thormodsgaard talked about Zero Trust Network Access, or ZTNA, and the process of moving access controls away from being more IP-based to more application- and identity-based controls.
Later on in the video below, he also talks about how ZTNA can specifically tighten up access for third parties to reduce the risk of potential breaches by limiting what information third parties can have access to using these updated access controls.
There are also defined Third-Party Risk Management programs that can help you continuously assess the possible risks from partners you are in operation with so that you can work to remediate any potential issues before they become a bigger problem for your organization in the long run.
What better way to talk about best practices for partner operations than by focusing on great information from our own partner Prevalent and their “Six Steps to Complete Third-Party Risk Management”?
Six Steps to Complete Third-Party Risk Management
Step 1: Define/Build/Optimize – Basic Program Decisions
It’s important that you bring in experts to advise you during this step so that you can create solid foundational guidelines before you properly start your third-party risk program. The goal at this point is to establish which vendors need to send and receive what information, as well as how you will send and receive said information.
Step 2: Monitor for Vendor Cyber and Business Risks
This second step is critical to get an understanding of the risks your partners pose to your overall business and how it can affect your operations. It is important that you analyze both cyber and overall business risks.
Step 3: Collect Evidence and Perform Due Diligence
In this step, you will take action on collecting evidence and perform due diligence reviews. Depending on the make-up of your organization, you will need to decide if this is a process you will do yourself, share the responsibility with other vendors, or completely outsource the collection and analysis of evidence to a TPRM vendor, audit firm, or systems integrator.
Step 4: Analyze and Score Results
Here at the halfway point, you will have completed, and potentially even validated your collected evidence. You will now need to analyze and score all evidence so that you can prioritize risk migration activity.
Step 5: Remediate Findings
After collection and analyzation, you will need to now remediate the findings from your collection and analyzation of evidence. Vendors defined in step one that have greater criticality to the business or higher risk levels will need to be prioritized.
Step 6: Report to Internal and External Stakeholders
With a well-established third-party risk management program, you can organize your reporting process to avoid being bogged down by complex and time-consuming compliance reporting. Many partners, like Fishtech Group, can help you set up reporting for common regulations and industry frameworks to make sure you are reporting your findings efficiently and accurately.
Here’s a video of our own Michelle Thacker, Director of Cyber Risk and Compliance, talking about how Fishtech Group can help streamline your approach to reporting.
Benefits of TPRM
There are many benefits to third-party risk management in relation to compliance, but as you can see in the steps above, you are also establishing a rich repository of information that can help you identify risk areas in your organization, and help remediate them early, especially when problem areas may be critical to your overall operations.
Any third-party partner that is connected to your organizational activities in this era of mass information, needs to be assessed and protections need to be put in place to avoid opportunities for breaches to occur due to larger attack surface areas with your vendors and partners.
During Cybersecurity Awareness Month, take an opportunity to step back and think of any areas you may be vulnerable in your digital operations, including the often-overlooked capacity for breach through third-parties, among other vulnerabilities within your internal operations. The general guideline to focus on during this first week is “If You Connect It, Protect It”.
If you’d like a more detailed approach on the Six Steps to Complete Third-Party Risk Management, you can view the Prevalent white paper here.
If you’d like to talk to one of our experts about third-party risk management, or any other areas of cybersecurity, fill out the form below. Stay tuned to our blog all month long as we continue to focus on various areas of cybersecurity to help you #BeCyberSmart.
Cybersecurity Awareness Month 2020
October 1, 2020Cybersecurity Insights
Cybersecurity Awareness Month was launched by the National Cyber Security Alliance & the U.S. Department of Homeland Security in October 2004 and has been a continued focus in InfoSec communities each October since. On this first day of October, we’re turning our focus toward spreading cybersecurity awareness to help members of our community and the organizations we serve do their part and #BeCyberSmart.
This year’s theme of ‘Do Your Part. #BeCyberSmart’ is a call to action for individuals to own their role in protecting their part of cyberspace. We each have a role to play in making sure we protect our own devices to ensure the broader security of the individuals of the organizations we are a part of.
To start off this critical month, we wanted to highlight some blog posts that will help to inform you about many areas of cybersecurity and lay the groundwork for your better overall awareness and understanding on the intricacies of cybersecurity and how you can #BeCyberSmart.
Why Cybersecurity Should Not Be an Afterthought in 2020
As organizations increasingly move their assets to the cloud, cybercrime has continued to mature, and the prominence of cyberattacks has grown. Cybersecurity, once a niche faction of a few forward-thinking organizations, is now a central pillar of the modern enterprise… or at least it should be. We read some statistics recently that shocked us. Most importantly:
Only 38 percent of companies listed in the 2019 Fortune 500 were operating without appointing a CISO in position.
Read more statistics like these, and how you can begin your start prioritizing cybersecurity within your organization with Fishtech Group in our blog post “Why Cybersecurity Should Not Be an Afterthought in 2020”.
2020: Not Your Father’s Ransomware
Business leaders and IT professionals have become increasingly familiar with ransomware over the last several years. Time after time, we’re exposed to high-profile stories where brands and organizations we know and love are crippled by cyber criminals encrypting sensitive data and asking for money in exchange for the “safe” return of data.
In 2019 alone, the top 5 largest payouts to cyber criminals made by organizations struck by ransomware totaled over 1.6 million dollars.
Read more about ransomware and some of the straight-forward steps you can take to help reduce the risk of becoming a victim in our blog post “2020: Not Your Father’s Ransomware”.
Six Tips for Boosting Your Insider Threat Deterrence Capabilities
At various times in any insider threat program, there inevitably will be shortcomings in governance, gaps in detection, difficulties tying data to a threat, and substandard responses. So, what’s the best fail-safe when those other important program capabilities fall short? Deterrence.
Deterrence is one of the lowest-cost ways to decrease the threat that malicious and negligent insiders pose to your organization. Because it is often viewed simply as a dull or awkward communications and training function, it rarely gets a second look.
We compiled six strategies for how you can make your deterrence strategy more innovative and effective in our blog post “Six Tips for Boosting Your Insider Threat Deterrence Capabilities”.
Do Your Part. #BeCyberSmart
Throughout the rest of the month of October, we will be focusing on many areas of cybersecurity during Cybersecurity Awareness Month so stay tuned to our blog and our social media channels for blogs, videos, infographics, and more so that we can all do our part and #BeCyberSmart.
Next week we will take a deeper look at the theme of the first full week of Cybersecurity Awareness Month: If You Connect It, Protect It. The line between our online and offline lives is indistinguishable. This network of connections creates both opportunities and challenges for individuals and organizations across the globe. The first week of Cybersecurity Awareness Month will highlight the ways in which internet-connected devices have impacted our lives and will empower all users to own their role in security by taking steps to reduce their risks.
Learn more about Cybersecurity Awareness Month by visiting the official website, or fill out the form below to talk to our experts about any questions you may have on your journey to protect your part of cyberspace.
Insider Threat Program Lessons Learned
September 30, 2020Cybersecurity Insights
As Insider Threat Awareness Month draws to a close, it’s worth taking a look back at the trends and developments that shaped the industry’s thinking over the past year, what lessons were learned and how they can inform insider threat program best practices moving forward.
Here are our top three lessons learned, along with links to blogs and webinars from the past 12 months that go into greater depth on each point:
‘Whole-Person’ Analysis is Essential: Heading our list is the growing recognition among insider threat mitigation experts that technical indicators found in conventional SIEM and UEBA systems just aren’t adequate to find the really dangerous insiders, at least in time to avert a crisis. Analyzing non-technical indicators like personnel data, travel and expense records, badge data and even third-party records can reveal additional early indicators that someone is about to become an insider threat. Couple this with a probabilistic model that ‘reasons’ on the data to highlight the highest-risk insiders sooner rather than later and you’ve got a powerful tool that proactively prioritizes where you should focus your scarce analytic and investigative resources.
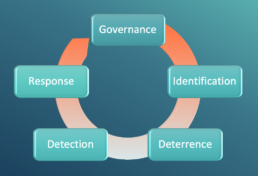
Develop a Five-Point Program: To be effective, an insider threat mitigation program must consist of five distinct elements. As we outlined in our five-part webinar series earlier this year, these elements are: Governance, Identification, Deterrence, Detection and Response. Skip one or more of these and your program won’t be nearly as effective.
Technology Doesn’t Solve Everything: This statement might sound strange coming from a software company, but the reality is that technology is only one component of a broader program that involves implementing the right policies and procedures, obtaining buy-in and ongoing support from top leadership and developing an effective program to communicate program missions and goals to staff and management. Use the governance element to create and manage the non-technology portions of the program.
Implementing an integrated insider risk mitigation program that combines clearly articulated policies, cross-departmental cooperation and leadership buy-in with the right investigative processes and analytical tools is not just good corporate practice, it also can save your company from data loss, reputational damage, civil liability exposure and, potentially, federal and state regulatory enforcement actions.
# # #
Note: Need a quick introduction to Haystax’s risk-based whole-person approach to insider threat mitigation? Check out our new solution intro video on the Haystax Insider Threat Mitigation web page.
Dissecting Valak (CYDERES Technical Blog Series)
September 24, 2020Cybersecurity Insights
Executive Summary
Valak was first discovered in 2019 as a malware loader and information stealer. Fishtech has seen an increase in thread hijacking being used by Valak threat actors to entice end users into clicking on phishing URLs or opening malicious documents. Valak leverages a plugin responsible for harvesting emails to further spread the malware. The following blog will examine how Valak is delivered and its capabilities.
Background
Valak was publicly recorded in October 2019 when two rules to detect Valak were created on Proofpoint’s ET Pro ruleset. The malspam network delivering Valak, or Shathak as Twitter labels it, has been seen targeting English and German-speaking businesses. Valak has evolved from acting as a loader to becoming a sophisticated, multistage piece of malware able to update itself and expand its capabilities.
Valak Delivery Method
The malspam delivering Valak uses existing email threads to increase the likelihood of the victim opening the attachment. To bypass email security, the attachments are password protected. This approach also hinders any automated sandbox analysis used to detonate suspicious attachments.
Figure 1: Email reply with password protected attachment
There are several features in this email that should arouse suspicion:
- The zip file attached to the email contains a 5-character password
- Sending the password on the same email usually means the threat actor is using this as a way to bypass antivirus or email filtering
- The email appears to be a reply to an email sent 9 months ago.
- The word ‘attached’ is misspelled “attach_ed
- A mismatch between the sender email and sender display name
Figure 2: Zip file containing a Microsoft Word Document
Attempting to open the file leads to a window prompt requesting a password.
Figure 3: Enter Password Window
Analyzing the document using ViperMonkey (a VBA Emulation engine) provides the following Summary of action carried out by the macro code:
Figure 4: Vipermonkey results for material06.20.doc
Examining the results show that the Macro ‘autoopen’ runs each time the victim opens the document. The API function ‘URLDownloadToFile’ is used to retrieve a file with a .cab extension. Once the file gap5.cab has been downloaded, it’s saved as 44312539.dat in the Directory c:\programdata. Regsvr32 is then used to run the 44312539.dat file.
As malware authors constantly change their tactics, it is always a good idea to verify analysis using multiple tools. To manually examine the Macros of the document, please see a previous blog here.
Similar URLs have been seen in URLhaus, urlscan.io and VirusTotal Intelligence. All the listed URLs are associated with Valak.
Figure 5: Download url listed in URLhaus
Opening the document in a virtual machine shows a message requesting the victim to enable macros. If macros were enabled for all documents, the file gap5.cab would have been downloaded automatically upon opening the document.
Figure 6: Microsoft Word Document requesting to enable Macros
After enabling macros, the Valak DLL is downloaded and saved to the C:\ProgramData directory.
Figure 7: Valak Dll saved to ProgramData directory
Regsvr32 is then used to run the Valak Dll. A window will confirm if the file was properly executed. Several versions of Windows failed to execute the file properly. The following screenshot was retrieved from a Windows 10 machine that executed the malware properly.
Figure 8: Pop up window where the Valak Dll was run
As shown below, the malware failed to run on a Windows 8 machine.
Figure 9: Pop up window showing file was not able to run
Once the Valak Dll is run, the file iVIwVADQD.eLxan is created in the “public” user directory and executed.
Figure10: Javascript configuration file
Figure 11: Process execution after enabling Macros
Additionally, placeholder, expired and legitimate domains can be seen in the contents of the configuration file along with the C2s, which are likely included to complicate manual static analysis. The legitimate domains are registered to Microsoft and Facebook:
- vo.msecnd[.]net – Microsoft
- msnbot-207-46-194-33.search.msn[.]com – Microsoft
- atdmt[.]com – Facebook
Placeholder domains that were never registered might be used in the future. Expired domains might have been C2s in the past:
- Knockoutlights[.]com – Domain Creation Date May 3, 2019
- Expired on Sunday, May 3, 2020
- d0d0f3d189430[.]com – No current IP address and appears it has not been registered
This leaves the following C2s:
- d0d0abee1d18255e[.]com
- Creation Date: 2020-06-18T12:32:43Z
- Current IP: 22.26[.]248
- Web Server Location: Portugal
- Organicgreensfl[.]com
- Domain Creation Date: June 4, 2020
- IP Address: 106.18[.]130
- Web Server Location: Germany
- a-zcorner[.]com
- Domain Creation Date: June 1, 2020
- IP Address: 119.156[.]128
- Web Server Location: Russia
The screenshot below shows the software signature, software version, and plain text variable names and values. As of this writing, Valak has evolved to using variable names and values with encoded strings.
Figure 12: Contents of configuration file (Part of the script)
Capabilities
The main purpose of the Dll loader is to write the initial scriptlet shown in figure 12 above and detonate the payload. This Dll loader is crypted and the crypter reconstructs the code placing it into memory. It will then perform multiple XOR loops and decompression which results in the unpacked Dll.
Valak script features:
- Create persistence in the victim’s machine
- Store Valak configuration in the registry
- Retrieve the “PluginHost” plugin
- Retrieve Client scripts
To create persistence, Valak creates entries under the registry key “HKEY_CURRENT_USER\\Software\\ApplicationContainer\\Appsw64\\” followed by a javascript file (Disk0.js) in the public directory which is called by a scheduled task named “Disk Diagnostics”.
Figure 13: Registry and Scheduled Task for persistence
The function “Loader.Persist” shows the javascript file “Disk0.js” being created and calling Loader.DeployHost at the end. The data retrieved by Loader.DeployHost using “Http.Request” is decoded and saved as an executable. This plugin is known as “PluginHost” and provides Valak with the ability to download additional plugins, making Valak more sophisticated than standard loaders. Notable additional plugins retrieved by Valak include “Exchgrabber” and “Clientgrabber” which target businesses by harvesting emails for ‘Thread Hijacking’ and used for stealing email credentials, respectively.
Figure 14: Loader.Persist function calling Loader.DeployHost
Figure 15: PluginHost Plugin being retrieved to further expand Valak’s capabilities
Conclusion
Valak has evolved from being a loader to a sophisticated piece of malware able to update and expand its capabilities. Malspam distributing malicious Word Documents delivering Valak is likely to continue.
CYDERES recommends that organizations conduct user-awareness training to educate users on commonly utilized phishing techniques and how to identify them. Common indicators that could indicate a phishing attempt include mismatched sender and reply-to addresses, a reply to an old email thread, grammatical errors or spelling mistakes, generic subjects or greetings, and emails that contain unsolicited documents. Additionally, organizations are advised to ensure that all security patches, especially those relating to Microsoft Windows, are applied as soon as they become available.
To become part of customer stories of breaches prevented, compliance achieved, costs slashed, technology optimized, or other real-world tales of digital transformation, take advantage of EDR solutions with CYDERES. If you are interested in talking more about how you can take advantage of EDR solutions with CYDERES, fill out the form at the bottom of the page, and we can connect you with an expert to help you find the right solution for your organization.
ATT&CK
Initial Access
Phishing attachment – ATT&CK ID: T1193
Execution
Regsvr32 – ID: T1117 1
User Execution – ID: T1204
Scripting – ID: T1064
Defense Evasion
Modify Registry – ID: T1112
Deobfuscate/Decode Files or Information – ATT&CK ID: T1140
Process Injection – ID: T1055
Command and Control
Remote File Copy – ID: T1105
Persistence
Schedule Task – ID: T1053
Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder – ID: T1547.001
References:
| https://www.proofpoint.com/us/daily-ruleset-update-summary-20191022 |
| https://twitter.com/luc4m/status/1265194192768315392 |
| https://www.virustotal.com/gui/domain/2zvdoq8grm7vwed20-zz.com/relations |
| https://urlscan.io/search/#2zvdoq8grm7vwed20-zz.com |
IOCs:
| 0aa589d6a1ddbf20647af5ceff898d92b72e6ea4d1c79f658bcb6d0213b71d95 |
| 8b25aa9582427a476c2e5b66cb00d59946e07021b9708571bb9187cb3d98917a |
| 4c0d7b112dfd99c751a85ad9539152c413ede7e5d976f75ae13a8b46ebf53e66 |