Tesseract Ventures + CYDERES: A Layer of Safety and Peace of Mind.
September 17, 2020Cybersecurity Insights
Editor’s Note: This post was originally shared on the Tesseract Ventures blog, found here.
At Tesseract, we’re working to create a technology ecosystem that helps modern organizations become smarter and better connected through next-generation robotics, 21st-century software, and radically connected platforms. Each piece of this ecosystem has the ability to produce huge amounts of valuable, actionable data—data that can transform the companies that possess it, making them safer and more fulfilling for their workers, as well as more innovative and more efficient.
However, with great power comes great responsibility. Data is a precious commodity that must be protected from attackers, and each piece of an advanced technology ecosystem like Tesseract must be secured against intruders. This is why we have entered into a partnership with CYDERES, Fishtech Group’s Security-as-a-Service division, to secure that data, as well as analyze and respond to possible threats.
By integrating CYDERES’ innovative security and analytics solutions with our own technologies, Tesseract is able to protect its intellectual property as well as strengthen the service we provide to current and future customers.
We asked Tesseract Ventures CEO John Boucard, and CYDERES President, Eric Foster to discuss this exciting new partnership, and how it will impact both companies and their clients.

Eric Foster and John Boucard pose for the original TESS robot at the inception of Tesseract Ventures when John spent time as EIR at Fishtech/Cyderes.
How do Cyderes and Tesseract’s offerings complement each other?
John Boucard, Tesseract Ventures: The alignment of Cyderes and Tesseract completes the offering to our customers by adding a layer of safety and peace of mind. Tesseract will supply an IoT, Robotics, and Analytics platform, and CYDERES will provide both security for the data that is being generated and the high level of customer support and monitoring this kind of advanced technology requires.
Eric Foster, CYDERES: The two offerings will work together seamlessly to create, analyze, visualize, and investigate data. Tesseract sensors and robots feed the CYDERES data pipeline, which analyzes that telemetry for threats. The vast amounts of data produced by Tesseract’s cyber-physical tools are delivered into Google Chronicle and the CYDERES Cloud-Native Analytics Platform to enable intelligent analytics at the speed of thought. Alerts from the analyzed telemetry and the Tesseract robots flow into the CYDERES SOC for 24/7 investigation, detection and response, and then flow out to the client’s Tesseract hub where it can be easily visualized and investigated.

Cyderes 24/7 Command Center
What are some unique threats IoT networks need to be protected from, compared to traditional networks?
John Boucard: Any IoT network creates new threat vectors that can be exploited to create entry points into your private network and data. Each IoT node can be a potential access point. CYDERES provides a hardened network structure to prevent attacks and also identifies potential aggressive activities that need to be responded to.
Eric Foster: We also use the term “attack surface” a lot—meaning how much of your network exists and is exposed to attackers. For most organizations, adding a significant IoT presence means that you are significantly expanding your attack surface, and creating an environment that needs to have both prevention, detection, and response to security threats.

The Tesseract Smart Space in our KC office.
Does CYDERES approach cybersecurity for IoT and AI networks differently than you would more traditional digital platforms?
Eric Foster: Yes and No. Ultimately IoT and OT environments have a lot of the same challenges we’ve been dealing with for 20 or more years in information security, such as knowing where your assets are, ensuring they’re kept up to date with the latest patches and with the properly hardened configurations and are protected with preventative and detective technologies at multiple layers.
At the same time, there are definitely novel cybersecurity challenges presented by IoT and AI technologies. Many run on technology platforms where traditional cybersecurity controls fall short. Luckily, CYDERES has partnerships with leading IOT security solutions like Armis (armis.com) for agentless device security in a world of unmanaged and un-agent-able devices, Illusive Networks (illusivenetworks.com) for deception technology via Illusive IoT Emulations, and Extrahop Reveal(X) (extrahop.com) for network layer detection of IoT threats.

On the construction site, PRISM anchors and badges combined with IoT feed data into Mosaic and the Tesseract SMART SPACE, all under the umbrella of safety Cyderes provides.
Tesseract’s motto is “There’s nothing more human than technology.” How do you view the role of human workers evolving as technologies like IoT networks and predictive analytics become more common in the workplace?
John Boucard: The future we see is one where human workers become more efficient and effective by allowing them to focus on the areas where they add value. An IoT solution is nothing more than data acquisition that is reviewed by both human and predictive models to determine both meaning and direction. In the process, the human workforce becomes better informed, with relevant data delivered faster and in more useful ways than ever before.
Eric Foster:: One of our core philosophies at CYDERES is “human-led, machine-driven.” This alignment in thinking makes us and Tesseract ideal partners. We believe cybersecurity is a problem analogous to flying a modern aircraft—too many decisions need to be made for a completely manual, human-based approach to detection and response of cybersecurity threats. This is what many legacy security services providers offer, however. At the same time, automation, AI, and machine learning are important but are far from the panacea that many security vendors will sell it as.
We find that a skilled human piloting “fly-by-wire” controls, significantly enhanced with automation, orchestration, and judicious application of intelligent statistical analysis (including, but not limited to machine learning) presents a superior approach to both extremes.

Once the building is complete, the same tech stays in place for the new tenant.
Can you walk us through a potential real-life problem, and solution that Cyderes and Tesseract would bring to the situation?
Eric Foster: Let’s take the example of a major retailer who wishes to enhance its employee safety and its guest safety in the post-COVID-19 world. The goal is also to raise shareholder value through increased productivity and reduction of workplace accidents and incidents. The retailer decides to get there by leveraging Tesseract PRISM Proximity Tracking Wearable Sensors in conjunction with a smart building powered by Tesseract Prism Anchor sensors, as well as Tesseract semi-autonomous robotics such as the T.E.S.S. Multi-Mission Sensor Platform.
Now, employee and guest safety and security can be optimized through the creation of proximity alerts for workers, automated analysis of social distancing guidelines including reporting on social distancing and compliance, intelligent analysis of hot zones and chokepoints that cause productivity issues, and the ability to cross-reference individuals and their encounters over a specific period of time.
These sensors and robots generate a tremendous amount of IoT and security telemetry and alert data, which are fed into the CYDERES Cloud-Native Analytics Platform for both intelligent real-time analytics and optionally for human-led, machine-driven analysis by the skilled team of analysts working 24/7 from the CYDERES Cyber Defense Centers.
These analysts can triage alerts, respond to threats, and produce reports, including addressing safety violations, public health, public safety, and more. Instead of being overwhelmed with alerts, the client knows a team of experts is handling it in real-time, and they can instead focus on their business.
All the data and results can be visualized on-premise in the Tesseract Environment, a collaborative workspace designed to create immersive situational awareness and control over highly disparate information streams. It can also be accessed from anywhere via Tesseract’s Mosaic Extended Reality (XR) through virtual reality headsets.
All the while, Tesseract’s networks, data, intellectual property, and the significant interconnected networks of IoT devices and deployed Tesseract technologies throughout the retailer are protected by the award-winning managed detection and response offering from CYDERES, including the CYDERES Cloud-Native Analytics Platform powered by the revolutionary analytics of Google Chronicle and in partnership with the unmatched scale, availability, and performance of Google Cloud.
Six Tips for Boosting Your Insider Threat Deterrence Capabilities
September 16, 2020Cybersecurity Insights
At various times in any insider threat program, there inevitably will be shortcomings in governance, gaps in detection, difficulties tying data to a threat and substandard responses.
So what’s the best fail-safe when those other important program capabilities fall short? Deterrence.
Deterrence is one of the lowest-cost ways decrease the threat that malicious and negligent insiders pose to your organization. Because it is often viewed simply as a dull or awkward communications and training function, it rarely gets a second look.
Here at the halfway point of Insider Threat Awareness Month, however, we think it’s worth challenging your insider threat program managers to give deterrence a chance.
Below are six strategies for how you can make your deterrence strategy more innovative and effective.
- Training isn’t the only answer. Many think deterrence just means more training. If your answer to every problem at the organization is to hold a training session, throwing another one on top of the pile is unlikely to succeed. Think about other strategies like those mentioned in the webinar link at the bottom of this post (clip 43:01 – 46:53). There’s so much more to deterrence than training.
- Make it a juicy story. Share stories that are relevant and Just like people rubberneck when they drive past an accident, they have a hard time not participating and engaging when there’s a compelling story on the table. Talk about cases where people were caught in acts that highlight the effectiveness of your insider threat program. This can be anything from group emails to putting up awareness posters in the restrooms to ‘public service announcement’ at the beginning of a virtual meeting.
- Survey your employees about how seriously their managers take insider threats. Not many people feel strongly about an insider threat program unless they have seen positive changes because of it. And chances are that positive impact won’t happen for all your managers. But you can artificially increase that impact by acknowledging managers who score highly, or counsel those that aren’t taking it seriously.
- Don’t just threaten potential insiders. Research shows that if you can appeal to someone’s desire not to be an insider threat, it’s almost as effective as someone knowing that they are being watched. Meaning that messages like “losing information isn’t only costing the company millions, it’s compromising your coworkers’ life work” can be just as effective as installing a highly sophisticated (and expensive) monitoring system.
- Message your insider threat program. Be deliberate about the way you message the program to the organization. A short clip from the deterrence webinar below (15:23 – 17:34) talks about all aspects of a deterrence program and how you might think about messaging it.
- Have an offboarding process, and don’t deviate from it. Rarely do people leave a company (voluntarily or otherwise) feeling 100% positive about their experience. Offboarding is a time to communicate expectations and create physical boundaries to sever ties amicably and professionally.
Deterrence is so much more than training. And every deterrence strategy is going to look a little different depending on what your corporate culture looks like. For more information and ideas about how you can make your employees more resilient, aware and prepared for the risks posed by insider threats, check out our recent webinar on deterrence here.
# # #
Note: For a compelling (and juicy) story about a formerly high-flying corporate exec who becomes a malicious insider, download a free copy of our paper To Catch an IP Thief here.
Talking DevOps with Chuck Crawford, Co-Founder and Chief Strategy Officer
September 10, 2020Cybersecurity Insights
Over the course of the last 20 years in cybersecurity, security practitioners have had to adapt to the many challenges that have emerged as data has moved from on-premise data centers to cloud, or multi-cloud environments.
We recently sat down with Chuck Crawford, Co-Founder & Chief Strategy Officer, to talk about how modern organizations can address these evolving challenges with a DevOps culture that brings security to the table as a primary part of the CI/CD pipeline.
Chuck addresses the importance of bringing teams up to speed on the necessary people, processes, technologies, and terminologies of the various teams they work with, from development, to operations, to security, and beyond.
With the growing speed at which organizations deploy their applications and services, a proper DevOps culture is more important than ever. With security integrated in a meaningful way, you can ensure you are proactively addressing governance, compliance, and security issues, so that you can continue to quickly bring value to your customers without setbacks that may emerge if you are constantly approaching your deployments from a reactive standpoint.
Hear more from our DevOps talk with Chuck Crawford.
https://vimeo.com/452344834/73fe1c32cb
Tesseract Ventures Partners with CYDERES to Spearhead Initiatives in Cybersecurity
Partnership between these two revolutionary, award-winning cyber startups provides companies with scalable solutions to address current and future cybersecurity challenges.
KANSAS CITY, Mo. – September 2nd, 2020 – Tesseract Ventures, a Kansas City-based technology company helping organizations become smarter, better connected, and more efficient through next-generation robotics, 21st-century software, and radically connected platforms, today announced it has selected CYDERES, Fishtech Group’s Security-as-a-Service division, as a partner to assess, align and service the cybersecurity space.
This partnership will disrupt the current market, providing more cost-effective and scalable solutions to companies across all of Tesseract’s verticals including the construction, medical and military industries.
“CYDERES’ capabilities to analyze unlimited security telemetry with its Cloud Native Analytics Platform (CNAP) and the revolutionary power of Google Chronicle that Tesseract will have access to through the partnership ensures that we will have the same level of incredible insight over our security program as we bring to the table through our market expertise,” said John Boucard, founder and CEO, Tesseract Ventures. “Most importantly, the CYDERES Managed Detection and Response solution will keep our organization, employees, critical intellectual property, and our customer-facing systems safe and secure.”
This partnership contributes to Tesseract and CYDERES’ positions as leading innovators of the quietly revolutionary Kansas City business community. Aggregating CYDERES’ innovative security and analytics solution with its own advanced technology, Tesseract is able to protect its intellectual property as well as strengthen the service it provides current and future customers.
CYDERES’ skilled analysts will pilot the process of using data collected from Tesseract’s PRISM wearable robots and digital ecosystem to make insightful decisions and provide real-time alerts.
Customers can safely store all their data and have the option to receive follow up services activated by Tesseract’s Mosaic and Prism System and serviced by CYDERES.
Tesseract’s partnership with CYDERES sets sights on disrupting the cyber tech and cybersecurity industries and furthering its product and service offerings among its other verticals.
“Tesseract is enabling businesses to defy the boundaries of space and time through next-generation technologies including robots, smart spaces, wearables, and radically connected platforms,” said Eric Foster, president, CYDERES. “While it's important to protect both Tesseract and the impressive class of clients that it serves, this partnership goes far beyond CYDERES protecting Tesseract—there are many applications of Tesseract’s cyber-physical tools that are directly applicable to our clients, and we are excited to get started.”
About Fishtech Group
Born in the cloud, Fishtech Group is the leading current-generation service provider enabling secure business transformation. Our experienced cybersecurity professionals plan, produce, and implement innovative solutions that ensure security and success. We make businesses more secure while increasing productivity and visibility. We focus on threats so you can focus on your business.
Governance and Compliance Q&A with Michelle Thacker, Director of Cyber Risk and Compliance
August 27, 2020Cybersecurity Insights
Governance and compliance strategies and concerns have taken on new importance this year with the mass adoption of remote work from organizations all over the world.
Throughout this monumental shift, business leaders have been doing their best to navigate the new hurdles that have presented themselves. We've heard from many customers about how difficult it has been to prioritize where their focus should be so that they stay compliant and secure in order to ensure their business moves forward.
With that in mind, we recently sat down with our Director of Cyber Risk and Compliance Michelle Thacker to ask what questions she's been hearing from clients on present compliance priorities, what companies should be planning for the remainder of 2020, GRC technologies, business continuity planning, and more. You can find the videos from this Q&A below.
Compliance Priorities for Companies
Governance and compliance in an ever-changing landscape can be tough for organizations, especially in an abnormally turbulent year. The most important thing is to ask - what are our strategic goals as an organization? Michelle talks about what these goals may look like, and what companies should focus on for the remainder of 2020.
https://vimeo.com/438622072/e0021ab00c
What's Your Risk Posture?
Showing risk posture to executives within your organization is also a pain point for many of our customers. There can be such a sprawl of information, and it's important to present information in a clear and concise manner. Michelle talks about how tools can be of great use to accomplish these goals.
https://vimeo.com/438975330/73a2b89199
Helping Clients with Governance
Curious about how Fishtech is helping current clients from a Governance standpoint? This video will be a great way to find a starting point for how we can help your governance program get up to speed using Fishtech's advisory offerings.
https://vimeo.com/440364952/73baa3a1ff
GRC Technologies
Current GRC technologies are helping customers more efficiently conduct GRC operations and may be of great assistance to your organization. Michelle speaks to a few of these technologies and what they bring to the table.
https://vimeo.com/440400344/034291a747
Business Continuity Planning
The value of business continuity planning has never been more clear than in 2020. Disaster can strike at any moment, and it is important to have a plan in place to make sure your organization can continue to operate, even in adverse situations. Michelle dives a little deeper into this critical offering.
https://vimeo.com/440099359/82d7accd58
Working with Other Fishtech Practices
One of the great benefits of Fishtech Group is our robust practice offerings and their ability to work together to create the best solutions for our customers. Michelle talks about how these various practices tie into CRC.
https://vimeo.com/440420875/97236e16fe
Ransomware in Healthcare (CYDERES Technical Blog Series)
August 20, 2020Cybersecurity Insights

In the first 7 months of 2020, 41 healthcare providers have reported ransomware attacks. Some organizations may opt to pay the demands of an attacker to keep the incident private, consequently avoiding potential harm to their reputation. Others may have controls in place that effectively prevent the attack or mitigate the impact of any damages. It is difficult to determine how many organizations have been targeted as well as how many have been affected by ransomware attacks. Below is a sample of industry-related, publicly acknowledged ransomware attacks:
Maryland Health Services (Lorien Health) disclosed a Netwalker ransomware attack in June. Earlier this year, CYDERES observed a new trend by ransomware operators wherein sensitive data is exfiltrated from the network prior to data being encrypted. The data is then used as an additional point of leverage to encourage the victim to meet the attacker’s demands. Maryland Health Services experienced this as the ransomware operators were able to collect sensitive data on up to 47,754 individuals. Following the attacker’s demands not being met, decryption keys and portions of the stolen data was publicly released.
Cozer-Keystone, SFI Health, and UCSF also recently disclosed similar Netwalker attacks. In the case of UCSF, the university paid attackers approximately $1.14 million (USD) to obtain the decryption key and prevent the disclosure of their data. Best practices to prevent and respond to a ransomware attack are encouraged, as paying attacker’s demands does not guarantee decryption and return of data. This may also serve as an indicator to other malicious actors that the organization is willing to capitulate to ransom demands, increasing the possibility of a future attack.
Magellan Health disclosed a second security incident earlier this year after sensitive personal data including social security numbers, usernames, and passwords were exfiltrated. This occurred after an attacker phished an employee, deceiving them into installing malware which propagated to the server housing said information. Details around the ransomware type and responsible actors are limited and CYDERES intelligence partners have not seen mentions of the attack across the darkweb services they monitor. Still, Magellan serves as an example of the importance of preparation for an attack given a similar phishing incident from 2019.
Mat-Su Surgical, Woodlawn Dental Center, Argus Medical Management, and Indoco Remedies have also disclosed recent ransomware attacks. The degree of impact on each organization varies but illustrates the breadth and size of services within the health care industry that malicious actors target.
A ransomware variant Netwalker, aka Mailto, has been distributed by attackers exploiting the COVID-19 pandemic with COVID-19 themed email messages. The messages often contain tainted Word or Excel attachments and users are enticed into opening the files and executing the malware initialization. Operators of Netwalker have also been known to disguise the malware as legitimate software such as Sticky Password. The payload may allow access for the actor to install additional malware, surveil the network and exfiltrate data. Once the ransomware executes, it scans for and begins encrypting files on the infected device and presents the user with a demand for payment to unlock files and prevent public disclosure of data.
Several different ransomware variants exist that function similarly to Netwalker. Operators of the Maze ransomware and Sodinokibi (REvil), like Netwalker, have been observed exfiltrating data from impacted networks prior to executing encryption protocols to maximize the potential for an organization to pay to prevent public data disclosure. Some ransomware variants target specific types of devices or organizations. Snake (aka EKANS) is one such ransomware found to target industrial and manufacturing organizations with the capability of identifying and terminating common industrial control systems related processes to deliberately impact production capabilities.
Ransomware attacks against health care providers increased by 350% in the last quarter of 2019. The evolving tactics of ransomware operators, impact of the global pandemic, increasing regulatory penalties, and low cost/effort to operate malware will likely result in this trend continuing.
Fortunately, there are several steps that can help prevent, identify, and respond to ransomware provided by CYDERES below:
System backups
Device backups should occur frequently. Multiple copies of the backup should be made and stored offsite in addition to locally. Cloud backups should also be considered where appropriate. Having multiple backups stored in separate, nonconnected locations gives the ability to confidently restore lost or encrypted data in the event that local backups are compromised.
Network Segmentation
Flat networks allow an attacker or malware to easily discover and spread to nearby network assets. Sensitive or critical assets should be segmented to limit the amount of damage that can be caused by a malware/ransomware infection. A segmented network can also help prioritize deploying detection and response capabilities as the movement of data on sensitive segments can be more highly scrutinized than non-sensitive segments.
Technical controls may also be easier to implement for cordoning off access to unnecessary services within sensitive segments. A client segment for instance may require internet access where storage devices should not have a default route out to the internet.
EDR/AV
Next-generation endpoint detection and response/Antivirus agents should be deployed to any connected device where possible. Procedures should be in place to constantly review agent health and remediate noted exceptions. Signature files should be updated as soon as vendors make them available and currently installed versions should be part of the agent health check process.
Classic or legacy signature-based endpoint agents like anti-virus can be ineffective protecting against ransomware and modern threats. These solutions should be phased out in favor of modern tools that leverage AI and behavioral-based detections.
Least Privilege
User and system accounts should be limited to only the permissions needed for their assigned tasks. Local admin accounts on devices should be disabled, passwords rotated, and use of these accounts permitted only after a request has been reviewed and approved. Service accounts should be set to non-interactive and their use limited to the devices necessary to carry out their purpose.
Roles should be routinely reviewed, and permissions adjusted as users transition to new positions or shift responsibilities.
Separate accounts for power users can be created with elevated privileges. These accounts should enforce more stringent password requirements and be controlled via multi-factor authentication where possible.
Training and Awareness
A user education program should regularly conduct training and awareness campaigns covering topics such as: password usage, identifying phishing emails, data classification and handling, and reporting security incidents.
24 x 7 x 365 Security Operations
Security logs should be collected with systems running detection logic against the telemetry for threats to the environment. Logs and detection events should be monitored 24 x 7 for signs of intrusion or malware execution.
Incident response plans should be on file and kept up to date. Third-party IR retainers should be in place prior to a security incident to augment response capabilities, provide expertise, and to assist in limiting the impact of a ransomware incident.
Penetration tests should be routinely ran against applications, servers, and network infrastructure in search of vulnerabilities.
Network Hygiene
Maintain an inventory of server and application assets. The asset list can be used to prioritize detection and response capabilities as well as inform monitoring for and applying patches on critical systems.
A patching schedule should be maintained so that critical firmware, OS, or application patches are applied as soon as possible after the release of patches.
SMTP gateway should be configured to enable spam and malware filtering.
Email and HTTP(s) traffic to/from the network should be filtered to only known-good external entities where possible. Uncommon TLDs such as .ru, .tv, etc., and webmail like gmail, yahoo, etc. should be limited to approved vendors or third-party contacts. An exception process should be in place and updates implemented based on periodic review.
User installed applications and associated plug ins should come from a trusted package or software management repository. Unsigned or internet downloaded application installation and execution should be blocked.
Securing the organization from threats like ransomware may seem a daunting task, but the experts at CYDERES can help. If your organization needs managed detection and response across both your cloud and on-premise environment, Fishtech Cyber Defense and Response (CYDERES) can help. CYDERES offers a better, faster and scalable SOC with a managed SIEM. CYDERES solutions include:
- Enterprise Managed Detection & Response
- Global Security Operations Center
- CYDERES Cloud
- CYDERES Security Incident Response Team
- CYDERES Red Team
- CYDERES CNAP
Fill out the form below to get in contact with one of our CYDERES experts to find out how we can best leverage our services to secure your business.
Take Advantage of EDR Solutions with CYDERES
August 13, 2020Cybersecurity Insights
Every time we hear customer stories of breaches prevented, compliance achieved, costs slashed, technology optimized, or other real-world tales of digital transformation, we rejoice – it’s why we do what we do. More and more, we hear these stories come from the winning solutions presented by Fishtech’s CYDERES and Google Cloud’s Chronicle.
Often, we’re going into detail about the specifics of how CYDERES and Chronicle complement each other to bring out the best in each other’s offerings, with Chronicle’s revolutionary telemetry analysis at a mass scale, and the next generation managed detection and response from CYDERES that analyzes and reacts to the security telemetry and potential threats that Chronicle illuminates.
Next up, we’re excited to showcase how these already powerful solutions integrate with best-in-breed technology in other areas of your cyber program. Imagine a fully tech-agnostic platform that has the ability to integrate with other solutions in your current stack, seamlessly fitting into what you are already running to bring unprecedented value and protection to you and your data.
A great example of an integration that is a fantastic complement to what CYDERES and Chronicle bring to the table comes from the world of Endpoint Detection and Response, or EDR. Specifically, we’re looking at a feature from SentinelOne that allows more freedom with how you can gather and use the mass amount of telemetry generated from your endpoints making it a fantastic accessory for the ingestion capabilities of Chronicle, and the full enterprise managed detection and response from CYDERES.
For more on this, we’ll hand the reins over to John Tuckner, Director of Customer Success Engineering at CYDERES, who recently wrote about this SentinelOne feature and how it integrates with Chronicle and CYDERES. If you are interested in talking more about how you can take advantage of EDR solutions with CYDERES, fill out the form at the bottom of the page, and we can connect you with an expert to help you find the right solution for your organization.
Without further ado…
—
SentinelOne Deep Visibility Export
By John Tuckner
Editor’s Note: This article was originally posted on John Tuckner’s blog which you can find here.
The EDR market has proven itself to be incredibly valuable over the past 5–6 years. I think many security practitioners would agree there is no larger return on investment than buying an EDR. It has even become such a large and wide market that 1. marketing has taken the entire segment over and 2. the vendors have started really competing against each other for dominance from a features perspective (both probably very related). One feature I key in on is the ability to make your endpoint telemetry (the data you own!) accessible outside of the vendor provided platforms.
The most intriguing aspect to me in the EDR realm is the telemetry that all EDR platforms are able to capture. From CrowdStrike to Sysmon, there are varying levels of effort to capture and stipulations tied to each in order to gather that telemetry. One new and incredibly promising vendor that makes telemetry available now is SentinelOne! I can’t get enough of the progress they are making in this space with their expanded “Deep Visibility” features turning the corner from a traditional EPP platform into a telemetry rockstar. It is a solution that can help provide the data needed for detection from nearly anywhere at the speed at which attacks occur.
With the Deep Visibility feature set enabled in your instance, SentinelOne will provide a Kafka instance and give customers (+ MSSPs) access to that instance to process that data.
I could go on for days at the value of message queues for security data, but this is really a great way to provide data for use. Looking through SentinelOne’s community boards, it had been a common ask for their Deep Visibility data to be accessible for SIEM use and now we’re there!
Currently, the Deep Visibility data provided in the Kafka stream falls into these categories:
- Process Creation
- Process Termination
- Process Exit
- File Creation
- File Modification
- File Deletion
- File Rename
- DNS
- TCPv4 Connection
- TCPv4 Listen
- Persistency
- HTTP Request
- Login
- Logout
- Registry Key Creation
- Registry Key Rename
- Registry Key Delete
- Registry Key Export
- Registry Key Security Changed
- Registry Value Creation
- Registry Value Modified
- Registry Value Delete
- Registry Key Import
- Scheduled Task Register
- Scheduled Task Update
- Scheduled Task Delete
- Scheduled Task Start
- Scheduled Task Trigger
I am a power user of Google Cloud’s Chronicle platform and there is no better platform right now to process the huge amounts of data that endpoints generate from that list. For this ‘small’ deployment I’ll be working with, we’re at 18GB of unmetered ingestion a week.
—
The blog post goes deeper into specific use cases. If you’d like to read the rest of the post and the more technical examples, follow this link.
To summarize, giving customers visibility into all their security telemetry is incredibly important, and we appreciate SentinelOne as well as others who are giving this much needed attention inside their solutions.
And what’s the best way to procure the necessary high-volume and long-access storage at a price point decoupled from volume or usage? Not only that, but a solution that has combined with the search speed of Google and the robust reporting and response capabilities of CYDERES?
CYDERES CNAP.
Learn how we can “CNAP on” this solution to modernize your existing SIEM/SOC, or start a all-new one with a CNAP. Learn more about CYDERES CNAP here, or fill out the form below and let’s start a discussion.
Why Cybersecurity Should Not Be an Afterthought in 2020
August 6, 2020Cybersecurity Insights
As organizations increasingly move their assets to the cloud, cybercrime has continued to mature, and the prominence of cyberattacks has grown. For example, check out our recent blog post on some of the biggest payouts from ransomware attacks in 2019.
Cybersecurity, once a niche faction of a few forward-thinking organizations, is now a central pillar of the modern enterprise… or at least it should be. We read some statistics recently that shocked us.
“To uncover how the world’s leading companies are leading by example to deploy cybersecurity initiatives, Bitglass researched the organizations in the 2019 Fortune 500 and analyzed public-facing information (from what is available on their websites). Here are the Bitglass report findings summarized the 2019 Fortune 500 companies:
- 38 percent of companies are operating without appointing a CISO in position.
- Only 16 percent (of 38 percent) have another executive listed as responsible for cybersecurity strategy, such as a VP of security.
- 62 percent majority do have CISOs but merely 4 percent of them have listed it on their company leadership pages.
- 77 percent of companies have no mention of any individual on their website responsible for security strategy.
- 52 percent of companies do not have any language relating to customer or partner data protection.”
Read again that these are “leading companies” on the Fortune 500. What does that mean for companies all the way down to America’s small business core? The outlook is not rosy.
Frankly, these statistics highlight how behind the times many companies are from an organizational standpoint and highlights the lack of priority security maturity holds within their organizations. Let’s face it, cybersecurity isn’t always the flashiest part of an organization, nor is it viewed as a revenue generator, which often means it becomes an afterthought to businesses with growth on their minds.
Fortunately, many organizations are quickly realizing the truth: the lost time, effort, and money spent fighting trench warfare battles with malicious actors using outdated technology is a much greater growth risk than the upfront cost of ensuring that the solutions are in place.
The choice is clear – prepare wisely and allow your teams to devote their energy into building your business, or fail to plan and risk everything fighting an uphill battle.
Our resolve to help lead organizations to a more secure future has never been stronger. Cybersecurity should NOT be an afterthought, especially in 2020. Having high-level leadership in your company that is responsible for security strategy is vital for long-term growth and success.
The COVID-19 crisis has brought a wave of cyberattacks with it, and unsuspecting companies are really paying the price. Here’s one of our recent blog posts surrounding phishing attacks that are leveraging anxiety around the COVID-19 crises to distribute malware.
As the situation surrounding COVID-19 evolves, and companies continue to find ways to effectively work from home, we suspect we will continue to see a rise in attacks like these, with companies paying hefty prices if they fall victim.
How many sales are now needed to offset the cost of incredibly pricy cyberattack remediation? The cost of preemptive cybersecurity solutions looks like small potatoes in comparison.
Many of these solutions should be getting put in place from the top, but when leadership is not in place to set strategy, as seen in the statistics above, disastrous opportunities arise. So, what can be done?
Apart from recognizing where growth needs to occur within your organization, partnering with a cybersecurity solutions provider can help provide a jumping off point on how to make cybersecurity a more central part of your organization.
Gap assessments are a great place to start. Essentially, these assessments can help identify areas in your organization that may not be fully mature, or spots where you may be more vulnerable. Being able to identify the areas in which your organization is lacking can help to guide strategy moving forward by more effectively focusing on problem areas, rather than on cybersecurity at large.
Secondly, Fishtech Group offer services like “Virtual CISO” through our Strategic Staffing services. Strategic Staffing services provide long-term, skilled resources to help organizations fill in any gaps they may have in their organization’s security team.
With “Virtual CISO” your organization can gain valuable resources like access to experienced cybersecurity and business professionals to bolster your staff for a pre-determined amount of time.
This service can quickly provide vetted leadership to bypass the hurdles that hiring in-house security leadership can bring to the fore. No need to worry about competing with other organizations for low-availability, high-demand, qualified cybersecurity professionals to make sure you can fast track your company to cybersecurity maturity and have confidence as you continue to build out your processes and your team.
There’s too much at stake in the modern business landscape to let cybersecurity and security leadership be an afterthought. Download our fact sheet on our Strategic Staffing services, or fill out the form below to get in contact with our team so we can start having discussions on how we can make cybersecurity a main focus for your organization.
Navigate the troubled waters of 2020, and beyond, with confidence.
CYDERES CNAP Intel Pack
July 30, 2020Cybersecurity Insights
In our ongoing mission to lead organizations to a more secure future, two things are abundantly clear: cybersecurity maturity (people, process, technology) has never been more important, and a truly modern, cost-effective, technology agnostic and reliable cyber defense platform is extremely hard to come by.
Until now.
A robust cyber defense platform that leverages both the power of traditional SIEM features with the latest next-gen practices has finally arrived.
Why? Modern organizations require both the breadth of a traditional SIEM product’s capabilities as well as cutting-edge features like thread hunting support, fast-pivoting, scalable threat intel matching, and more.
Unfortunately, the leading legacy SIEM offerings force a doomed pick between mature but outdated tools with next-gen but incomplete ones.
What if you didn’t have to choose? What if “all the above” was an actual, realizable solution?
The launch of the CYDERES Cloud Native Analytics Platform (CNAP) has brought with it a flood of press releases, videos, articles, and webcasts.
All the same, we know it can be a lot to unpack all of this information in such a piecemeal way. For your convenience, we have put all of our CNAP content below in one easy-to-access place so that you can learn about what CYDERES CNAP is all about and how it can bring unprecedented speed and value to your organization.
If you are ready to harness the power of Google Chronicle (the same tool Google uses to protect itself) with all of the tuned up add-on offerings of CYDERES CNAP, fill out the form at the bottom of this post, and we can schedule some time to talk one-on-one about how we can help your organization.
Let's get started!
1. PRESS RELEASE: CYDERES CNAP Launches
Kansas City, MO (July 16, 2020) — CYDERES, the Security-as-a-Service division of cybersecurity solutions provider Fishtech Group, announces the launch of its Cloud Native Analytics Platform (CNAP, pronounced ‘snap’). CNAP provides a pre-assembled cloud-native SIEM solution delivered in an as-a-Service model, designed to enhance and extend the revolutionary security analytics and unmatched data lake capabilities of the Google Chronicle platform.
2. FACT SHEET WITH CASE STUDY
3. VIDEO: CYDERES CNAP Interview Series
We interviewed Eric Foster, President of CYDERES, to help give you a better idea of what CNAP is, why it was built, and more. Check out a few videos from the interview series below.
https://vimeo.com/434097015/64a087bde0
https://vimeo.com/437890857/8b1958d64a
https://vimeo.com/436531530/ef6660e00d
https://vimeo.com/437887487/6a86b8579d
4. BLOG: Dr. Anton Chuvakin (aka "The Godfather of SIEM") on CNAP
Google Chronicle's Head of Solution Strategy Dr. Anton Chuvakin wrote up a great piece on how Chronicle and CNAP work together to give you the best of traditional and next-gen offerings, culminating in a truly unique and effective solution for organizations in the modern era.
5. WEBCAST SERIES W/ DEMO: How to Modernize Your SOC in a CNAP
To round out the list, we have links to parts 1&2 of the long-form webcast series, "How to Modernize Your SOC in a CNAP". These webcasts dive deeper into CNAP features and offerings, with some live demos sprinkled in as well. These recordings will give you the broadest scope on what CNAP is all about, and it's game-changing abilities.
How to Modernize Your SOC in a CNAP pt. 1
Common legacy SIEM pain points and the what and how of this modern cyber defense platform (including demo of CNAP).
How to Modernize Your SOC in a CNAP pt. 2
The future of cyber defense, the evolution of SIEM and SOC teams, and best practices.
6. Long-Form CNAP Demo with Eric Foster, President of CYDERES
Let Us Know How We Can Help
We hope these resources are a great jumping-off point to learn more about the power of CYDERES CNAP and our partnership with Google Chronicle as we pave the way toward a more secure future for organizations like yours. If you would like to get in contact with one of our professionals to talk more about CNAP, fill out the form below.
Classifying Malware (CYDERES Technical Blog Series)
July 23, 2020Cybersecurity Insights

With the constant rise of cyber-attacks, understanding the type of threat your organization faces is a vital step towards stopping the attack. When it comes to malicious software threats, classifying malware can help answer the following questions:
- Was this a targeted attack?
- If so, who is behind this attack?
- How can we detect and stop this type of attack?
- What is the extent of the damage?
Some sandboxes are able to classify the malware sample, but what happens when the sandbox results come back empty? Analysts can search the web for their cryptographic hash while hoping someone has already stumbled upon this specific malware. Is there a way to compare the similarity of a binary against previously analyzed samples? Yes, there is. The following techniques will help compare a binary against previously classified samples:
- SSDeep
- Imphash
- Section hash
- Yara rules
Using a combination of these will ensure the best results. To demonstrate these tools and techniques, the following sample was retrieved from VirusTotal with the hash:
d18d211cf75fbc048d785af92b76a1aa7a01e381313b1a5e66e9cf564cbe78d4
Figure 1: VirusTotal results for the listed hash
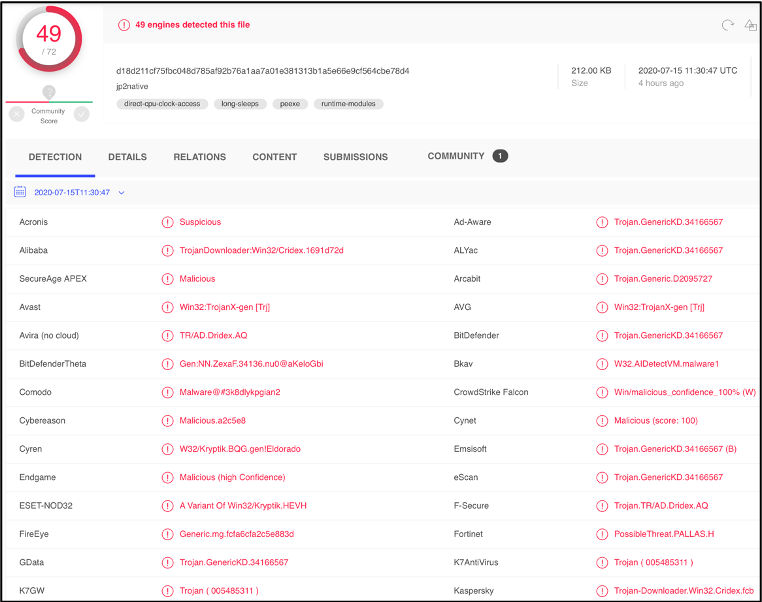
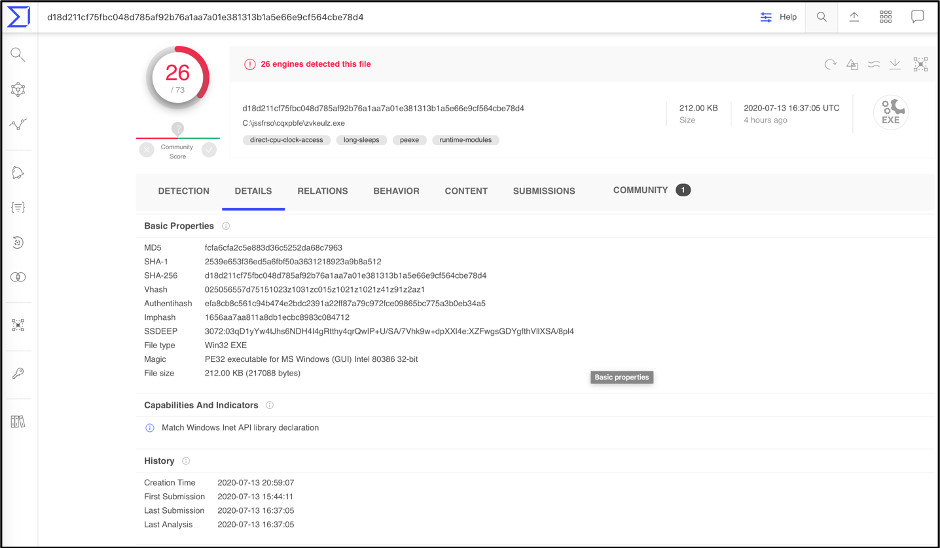
For future reference, this sample will be called Sample 1. We will first look at how these tools and techniques work and then we will compare and classify this sample to previously analyzed samples. Examining the DETECTION section in VirusTotal does not give us much information on the sample’s malware family. However, the DETAILS section lists the Imphash, fuzzy hash, and the section hash which is a great start.
Figure 2: VirusTotal Details section for the listed hash
SSDEEP
SSDeep is a tool that generates context triggered piecewise hashes (CTPH), also called fuzzy hashes. CTPH can match inputs that have homologies, or similar relations. Such inputs have sequences of identical bytes in the same order, although bytes in between these sequences may be different in both content and length. The ssdeep tool can be installed locally for Windows and Linux platforms. For information on installing ssdeep, head over to their site. If you have a directory full of previously analyzed samples, the analyst can use the following commands:
$ ssdeep * > fuzzy_hashes.txt
$ ssdeep -m fuzzy_hashes.txt malware.exe
The above command first writes all fuzzy hashes in the working directory to a file named fuzzy_hashes.txt. The second command compares the fuzzy hash (using the matching mode, -m) of malware.exe to the list of previously analyzed samples. Using ssdeep -h will show all the commands that can be used.
IMPHASH
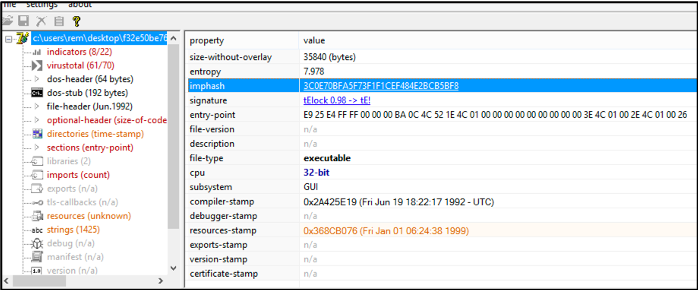
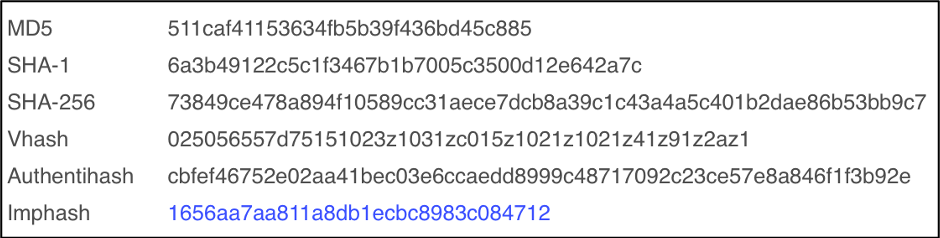
The imphash (Import Hash) is calculated based on the libraby/API names and their specified order within the executable. A quick way to calculate the imphash is to load the binary into PeStudio, as seen below.
Figure 3: PEStudio showing the imphash of a suspect binary
Section Hash
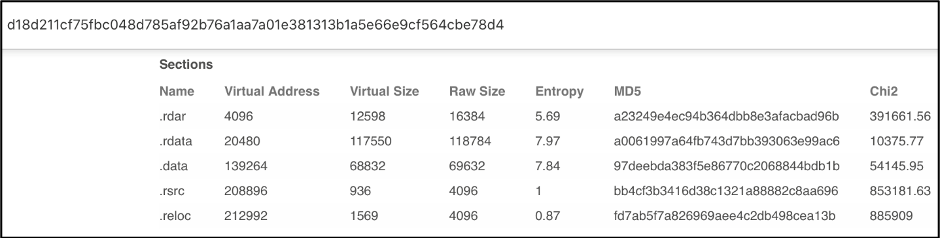
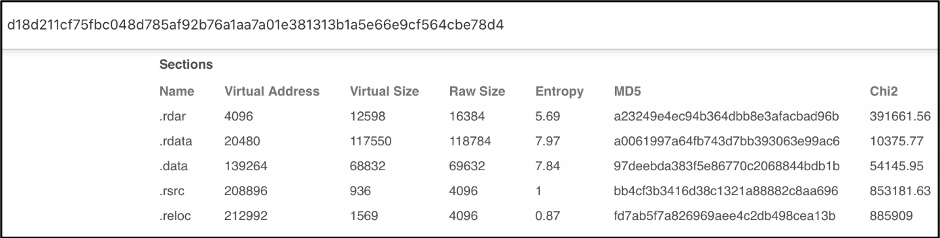
Scrolling down on the DETAILS section of the VirusTotal page, we can see the Sections hash listed. Similar to the imphash, section hash can help identify similar samples.
Figure 4: VirusTotal showing the Sections hash of Sample 1
Comparing and Classifying Sample 1
Searching for the fuzzy hash in VirusTotal, results in 20+ samples. Looking at the similarity column shows that the first sample has 100% similarity, which makes sense because this is our initial sample. The second sample has a 97.59% similarity, The higher the number the more similar the files.
Figure 5: VirusTotal showing the fuzzy hash search results
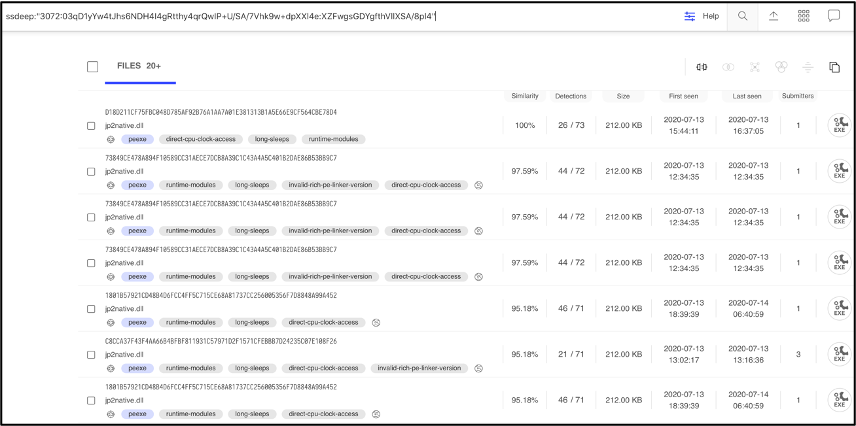
Comparing this 2nd sample to Sample 1, we can see the similarity. Both samples contain the same imphash of 1656aa7aa811a8db1ecbc8983c084712. This means they have the same import address table and were generated by the same builder kit.
Figure 6: VirusTotal showing the Imphash of Sample 1
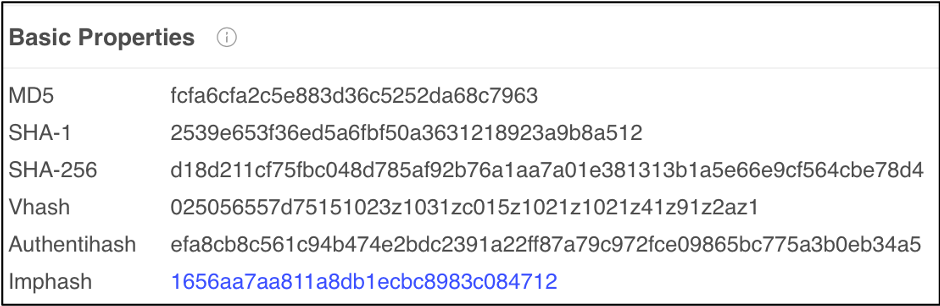
Figure 7: VirusTotal showing the Imphash of Sample 2
Several section hashes match the hashes of Sample 1, 4 out of 5 sections to be exact.
Figure 8: VirusTotal listing the Section hashes of Sample 2
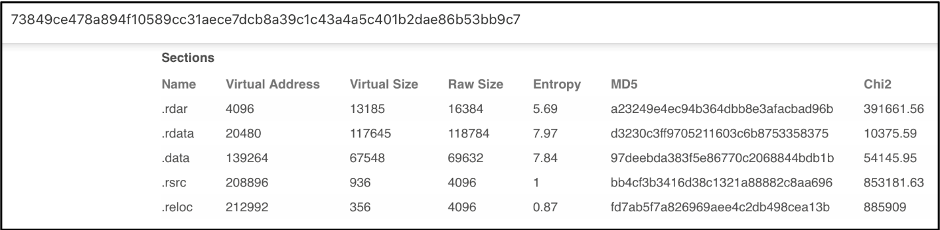
Figure 9: VirusTotal listing the Section hashes of Sample 1
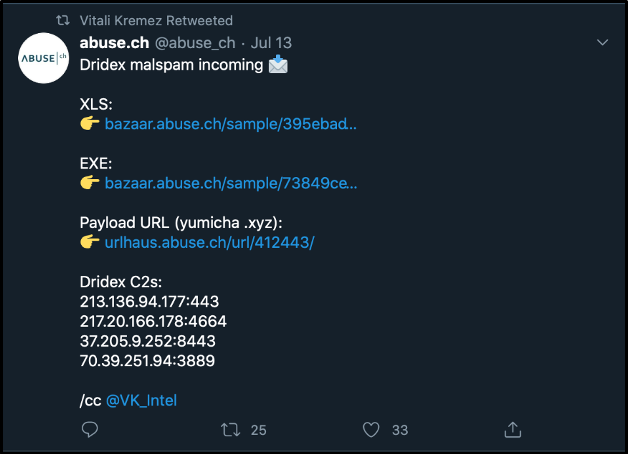
At the time of this writing, a web search for Sample 1 came back empty. A google search of Sample 2 (73849ce478a894f10589cc31aece7dcb8a39c1c43a4a5c401b2dae86b53bb9c7 listed in VirusTotal during our ssdeep search) with a 97.59% similarity, resulted in the following tweet from Vitali Kremez, a well-known security researcher.
Figure 10: Vitali Kremez retweet
It can be seen from the screenshot that this sample was classified as Dridex. When comparing and classifying malware samples, its important for the analyst to correlate findings with various sources and tools. This brings us to our last topic: Yara rules.
Yara rules
Yara is used by security researchers as a powerful malware classification and identification tool. Once yara is installed on the analyst’s system, rules can be created based on text or binary information contained in the malware sample. A rule consists of three sections:
- Rule name – Name to identify the rule
- Strings – This section contains text or binary information. There are several types of strings the analyst can look for:
- Text strings, with modifiers: nocase, fullword, wide, and ascii.
- Hexadecimal, in combination with wild-cards, jumps, and alternatives.
- Regular expressions, with the same modifiers as text strings.
There are many more advanced conditions you can use, but they are outside the scope of this post. More information on the use of YARA can be found in the YARA documentation.
- Condition – This section contains a Boolean expression, which will specify the condition for the rule to match.
Rule Example
{
strings:
$a = “text1”
$b = “text2”
condition:
($a or $b)
}
To apply what we have learned, let’s create a yara rule that can be scanned against Sample 1. From Vitali’s retweet, we know the 2nd sample has the following indicators of compromise (IOCs):
- Dridex payload URL: hXXp://yumicha.xyz/lvkahex.exe
- Botnet ID: 40400
- Dridex C2s:
213.136.94.177:443
217.20.166.178:4664
37.205.9.252:8443
70.39.251.94:3889
To create this rule, the known Dridex C2s will be used.
Rule dridex
{
strings:
$a = “213.136.94.177”
$b = “217.20.166.178”
$c = “37.205.9.252”
$d = “70.39.251.94”
condition:
($a or $b) and ($c or $d)
}
Running this rule in the terminal against a memory dump from Sample 1 results in a match. Running yara with the -s option, prints the matched strings. From the screenshot, the newly created rule matched on all the dridex C2s from the 2nd sample.
Figure 11: Terminal output of Dridex yara rule scan against Sample 1
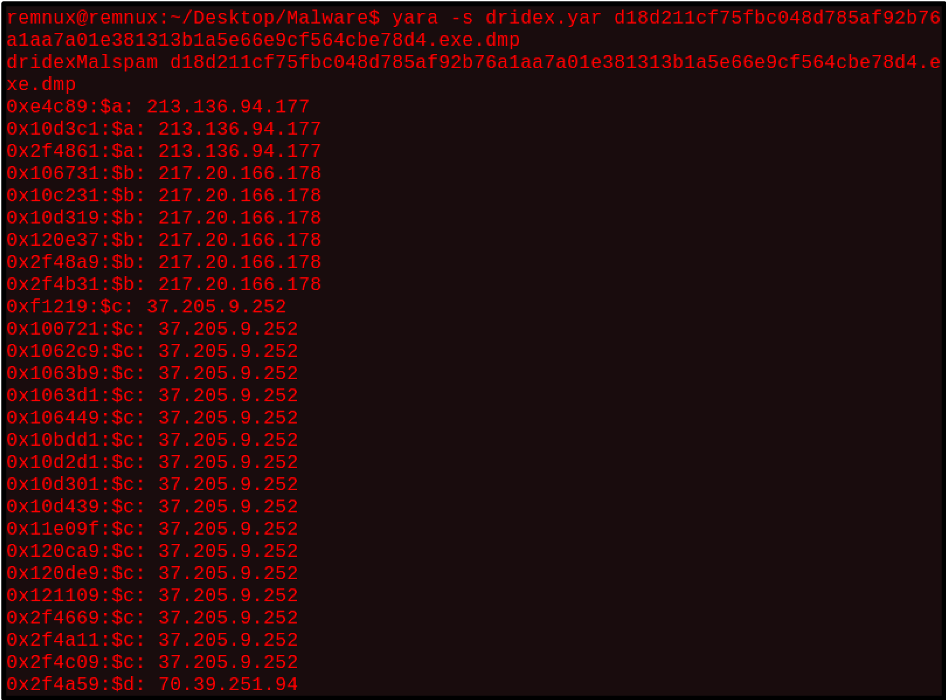
As malware authors often make small changes to their samples to thwart analysis, the techniques and tools discussed in this blog will help in classifying and comparing new malware samples. It is a good practice to generate the fuzzy hash, section hash, and imphash of all malware samples you analyze and store these hashes in a repository. Storing these hashes will allow the analyst to compare a new sample and determine similarity.
If your organization needs managed detection and response across both your cloud and on-premise environment, Fishtech Cyber Defense and Response (CYDERES) can help. CYDERES offers a better, faster and scalable SOC with a managed SIEM. CYDERES solutions include:
- Enterprise Managed Detection & Response
- Global Security Operations Center
- CYDERES Cloud
- CYDERES Security Incident Response Team
- CYDERES Red Team
To find out more about what these solutions entail, head over to our services link.
References
https://ssdeep-project.github.io/ssdeep/index.html
Dridex malspam incoming 📩
— abuse.ch (@abuse_ch) July 13, 2020
XLS:
👉 https://t.co/yFguJRpz0G
EXE:
👉 https://t.co/XK9LTSSVr3
Payload URL (yumicha .xyz):
👉 https://t.co/AeXWzZBLm6
Dridex C2s:
213.136.94.177:443
217.20.166.178:4664
37.205.9.252:8443
70.39.251.94:3889
/cc @VK_Intel










